social networking
What is social networking?
Social networks are websites and apps that allow users and organizations to connect, communicate, share information and form relationships. People can connect with others in the same area, families, friends, and those with the same interests. Social networks are one of the most important uses of the internet today.
Popular social networking sites -- such as Facebook, Yelp, Twitter, Instagram and TikTok -- enable individuals to maintain social connections, stay informed and access, as well as share a wealth of information. These sites also enable marketers to reach their target audiences.
Social networking sites have come a long way since the first social networking site, SixDegrees.com, was launched in 1997. Today, the world is rapidly adopting newer social networking platforms. According to DataReportal, a Kepios analysis from January 2022 indicated that there are more than 4.74 billion social network users worldwide.
How does social networking work?
The term social networking entails having connections in both the real and the digital worlds. Today, this term is mainly used to reference online social communications. The internet has made it possible for people to find and connect with others who they may never have met otherwise.
Online social networking is dependent on technology and internet connectivity. Users can access social networking sites using their PCs, tablets or smartphones. Most social networking sites run on a back end of searchable databases that use advanced programming languages, such as Python, to organize, store and retrieve data in an easy-to-understand format. For example, Tumblr uses such products and services in its daily operations as Google Analytics, Google Workspace and WordPress.
What are social networks?
With the broad spectrum of websites, apps and services that exist online, there is no single exact definition of a social network. Generally, though, social networks have a few common attributes that set them apart.
- A social network will focus on user-generated content. Users primarily view and interact with content made by other users. They are encouraged to post text, status updates or pictures for viewing by others.
- Social networks allow the user or organization to create a profile. The profile contains information about the person and a centralized page with the content posted by them. Their profile may be associated with their real name.
- A social network has a way to form a lasting connection with other users. These connections are commonly called friending or following the other user. They allow the users to find other users and form webs of relationships. Often an algorithm will recommend other users and organizations they may want to form a connection with.
Although often used interchangeably, social network is different than social media. A social network focuses on the connections and relationships between individuals. Social media is more focused on an individual sharing with a large audience. In this case, media is used in the same sense as in mass media. Most social networks can also be used as social media sites.
What is the purpose of social networking?
Social networking fulfills the following four main objectives:
- Sharing. Friends or family members who are geographically dispersed can connect remotely and share information, updates, photos and videos. Social networking also enables individuals to meet other people with similar interests or to expand their current social networks.
- Learning. Social networks serve as great learning platforms. Consumers can instantly receive breaking news, get updates regarding friends and family, or learn about what's happening in their community.
- Interacting. Social networking enhances user interactions by breaking the barriers of time and distance. With cloud-based video communication technologies such as WhatsApp or Instagram Live, people can talk face to face with anyone in the world.
- Marketing. Companies may tap into social networking services to enhance brand awareness with the platform's users, improve customer retention and conversion rates, and promote brand and voice identity.
What are the different types of social networking?
While there are various categories of social networking sites, the six most common types are the following:
- Social connections. This is a type of social network where people stay in touch with friends, family members, acquaintances or brands through online profiles and updates, or find new friends through similar interests. Some examples are Facebook, Myspace and Instagram.
- Professional connections. Geared toward professionals, these social networks are designed for business relationships. These sites can be used to make new professional contacts, enhance existing business connections and explore job opportunities, for example. They may include a general forum where professionals can connect with co-workers or offer an exclusive platform based on specific occupations or interest levels. Some examples are LinkedIn, Microsoft Yammer and Microsoft Viva.
- Sharing of multimedia. Various social networks provide video- and photography-sharing services, including YouTube and Flickr.
- News or informational. This type of social networking allow users to post news stories, informational or how-to content and can be general purpose or dedicated to a single topic. These social networks include communities of people who are looking for answers to everyday problems and they have much in common with web forums. Fostering a sense of helping others, members provide answers to questions, conduct discussion forums or teach others how to perform various tasks and projects. Popular examples include Reddit, Stack Overflow or Digg.
- Communication. Here, social networks focus on allowing the user to communicate directly with each other in one-on-one or group chats. They have less focus on posts or updates and are like instant messaging apps. Some examples are WhatsApp, WeChat and Snapchat.
- Educational. Educational social networks offer remote learning, enabling students and teachers to collaborate on school projects, conduct research, and interact through blogs and forums. Google Classroom, LinkedIn Learning and ePals are popular examples.
What are the advantages and disadvantages of social networking?
Social networking can be a double-edged sword. On one end, it provides unsurpassed social benefits, yet it can also make people more vulnerable to the spread of misinformation, as well as privacy and security threats.
Social networking offers the following benefits to consumers and businesses:
- Brand awareness. Social networking enables companies to reach out to new and existing clients. This helps to make brands more relatable and promotes brand awareness.
- Instant reachability. By erasing the physical and spatial boundaries between people, social networking websites can provide instant reachability.
- Builds a following. Organizations and businesses can use social networking to build a following and expand their reach globally.
- Business success. Positive reviews and comments generated by customers on social networking platforms can help improve business sales and profitability.
- Increased website traffic. Businesses can use social networking profiles to boost and direct inbound traffic to their websites. They can achieve this, for example, by adding inspiring visuals, using plugins and shareable social media buttons, or encouraging inbound linking.
Social networking also has the following downsides:
- Rumors and misinformation. Incorrect information can slip through the cracks of social networking platforms, causing havoc and uncertainty among consumers. Often, people take anything posted on social networking sites at face value instead of verifying the sources.
- Negative reviews and comments. A single negative review can adversely affect an established business, especially if the comments are posted on a platform with a large following. A tarnished business reputation can often cause irreparable damage.
- Data security and privacy concerns. Social networking sites can inadvertently put consumer data at risk. For instance, if a social networking site experiences a data breach, the users of that platform automatically fall under the radar as well. According to Business Insider, a data breach in April 2021 leaked the personal data of more than 500 million Facebook users.
- Time-consuming process. Promoting a business on social media requires constant upkeep and maintenance. Creating, updating, preparing and scheduling regular posts can take a considerable amount of time. This can be especially cumbersome for small businesses that may not have the extra staff and resources to dedicate to social media marketing.
Social networks in business
There are many ways a business or organization can use social networks. Globally, the average person spends over two hours a day using social networks. This represents a great opportunity and market.
Most social networks are run as for-profit companies. They make most of their revenue from selling ads or promoted content. Facebook's parent company Meta has an almost $300 billion market cap.
Social networks can be used for customer research, engagement and marketing. They offer a way to directly connect businesses and customers. Brands can build a community around themselves. Social networks collect information about users' likes and dislikes, allowing for extremely targeted advertising. Social media listening allows an organization to learn what people are saying about their company.
Some businesses are implementing internal social networks. In very large organizations this can increase employee engagement and satisfaction. Also, as teams become more geographically diverse or have members working from home, private social networks can promote collaboration and information sharing.
Some business are beginning to use social networks in their recruitment strategies.
Examples of social networking
Every established organization advertises on social networking these days. Here are four examples of social networking websites:
- Yelp. Picking a restaurant, dentist, doctor or hair salon is not always easy, so social networking sites like Yelp offer crowdsourced customer reviews of these types of businesses or providers.
- Pinterest. Bookmarking sites like Pinterest enable users to share photos and organize links to a variety of online resources and websites. Similar to a digital scrapbook, Pinterest enables users to save specific pins to pinboards, making it easier to search for specific topics and share them with followers.
- Rover. A popular pet-sitter services portal, Rover enables pet owners to connect with pet sitters, dog walkers and pet-boarding services.
- Airbnb. Airbnb helps travelers search for a place to stay based on their preferences, including multishared spaces, shared spaces with private rooms and entire properties. Places on Airbnb are mostly rented out by homeowners.
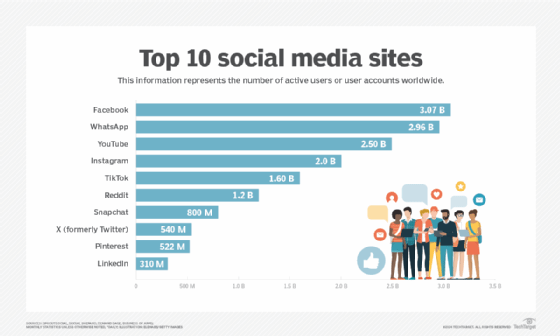
What are the top 10 social networking sites?
Although there are numerous social networking websites, the following sites are the most popular:
- Facebook. Facebook users create profiles, share information, send messages and post status updates on their walls. Ranked the most active social networking platform by DataReportal, Facebook has more than 2.9 billion active users. In 2021, the company was renamed Meta to reflect its business beyond just social media.
- YouTube. This popular video-sharing website enables users to share, upload and post videos and vlogs. According to Global Media Insight, YouTube has more than 2 billion monthly active users.
- WhatsApp. This free instant messaging app lets users send text messages, make video and voice calls, and share documents. According to WhatsApp, it has more than 2 billion users worldwide.
- Instagram. This free social media platform enables users to share long- and short-form videos and photos. It is primarily designed for iOS and Android smartphone users, but a desktop version is also available. However, sharing and uploading of content is only available through the Instagram app. Also owned by Meta, Instagram has over 2 billion monthly active users as of December 2021, according to CNBC.
- TikTok. This app is used for sharing and making personalized short videos. TikTok caters to a younger audience and is well known for being a lively and fun-to-use social networking platform. According to the Business of Apps newsletter, TikTok has more than 1.2 billion users as of the end of 2021.
- Tumblr. This microblogging site enables users to publish multimedia and other content types inside short blog posts. Users can also follow other users and make their blogs private. According to FinancesOnline, as of February 2021, Tumblr has more than 518 million user accounts.
- Twitter. Launched in 2006, this social media platform enables users to share their thoughts and opinions with a broad audience by posting messages known as tweets that contain up to 280 characters. According to DataReportal, as of January 2022, Twitter has more than 436 million users.
- Pinterest. The Pinterest bookmarking site enables users to save and organize links to favorite online resources and destinations through tagging. According to Pinterest Inc., the platform has 431 million global monthly active users as of December 2021 -- a 6% decrease over the previous year.
- Reddit. Founded in 2005, Reddit provides a diverse collection of forums and subforums -- also known as subreddits -- on a variety of topics, including sports, breaking news and technology. Here, users can comment on each other's posts, as well as share news and content. According to Reddit, it has more than 50 million daily active users. This translates into 430 million monthly users as of 2019, according to The Small Business Blog.
- Snapchat. This multimedia app can be used on smartphones running Android or iOS. Founded in 2011, Snapchat enables users to send pictures or videos called snaps to friends. These snaps vanish after they have been viewed. According to Snap Inc., Snapchat has 319 million daily active users as of the end of 2021.
Controversies in social networks
Social networks are used daily by much of the world's population. There are therefore many controversies that surround their use and management.
Social media addiction is becoming common. People can begin to feel a sense of anxiety if they don't check their social media accounts, or they may compulsively refresh them. Social networking posts are also highly curated, people only post the good things that happen to them. This can cause a warped view of reality where the viewer thinks that others have better lives than they do. This leads to a fear of missing out (FOMO) on social events.
Cyberbullying is when someone makes social media posts with the intention to harm someone else. This can take the form of publicly posting the private information of someone or sending abusive messages. Tragically, cyberbullying has led to the suicide of some individuals. It is now a major concern in public schools. Doxing is when someone publicly posts the personally identifiable information, such as an address or phone number, of someone else.
As mentioned in disadvantages, privacy is a major concern for many social network users. Anything that is posted can be used by the site to sell advertisements. This can include location information, embarrassing details or private data. This information could also be requested by law enforcement officials. Additionally, some social networks have confusing privacy settings, causing people to accidentally make information public. Since they store a lot of personal information, social networks are also susceptible to data breaches.
Censorship is a hot-button issue for many social networks. Social networks are private companies, so the content posted by individuals isn't necessarily protected by governmental free speech laws, but instead is at the discretion of the site's terms of service (ToS) or administrators. This can put the site into the position of arbitrating what is or is not allowed on the site. This can be particularly divisive when it comes to political issues, hate speech and calls to violence that may be posted by public figures. Some say that the sites have a moral responsibility to take a hard stand against all negative speech, while others say that all speech should be allowed by the platforms and any content removal is censorship.
Misinformation can be easily spread on social networks. Users are encouraged to share the latest news or discuss new topics. This can cause rumors or hearsay to be shared as truth. Others share their opinions as fact. It has also been reported that users, organizations and even governments may intentionally share false information, sometimes while pretending to be someone else. This has caused some social networks to begin adding fact checking alerts to some posts that may contain misinformation.
Learn ways to spot disinformation on social media and essential social media guidelines for employees.