Wireshark
What is Wireshark?
Wireshark is a widely used, open source network analyzer that can capture and display real-time details of network traffic. It is particularly useful for troubleshooting network issues, analyzing network protocols and ensuring network security.
Networks must be monitored to ensure smooth operations and security. Popular with academic institutions, government agencies, corporations and nonprofits, Wireshark is one such tool that can offer an in-depth view into network activities, diagnose network performance issues or identify potential security threats.
Key features of Wireshark
Wireshark seeks to simplify and enhance the process of network traffic analysis. Each function is designed to offer unique insights and control over network activities. Here are some of its core features:
- Packet capture (PCAP). Converts network traffic into a human-readable format, making it easier to understand and diagnose concerns.
- Real-time analysis. Provides a live view of network traffic, offering immediate insights into ongoing network activities.
- Filtering capabilities. Enables users to focus on specific types of network traffic, making analysis more efficient and targeted.
- Graphical user interface (GUI). Designed for ease of use, ensures that both beginners and experts can navigate and analyze data effectively.
Common uses for Wireshark
Wireshark can be used to examine the details of traffic at a variety of levels, ranging from connection-level information to the bits constituting a single packet.
PCAP can provide a network administrator with information about individual packets, including transmit time, source, destination, protocol type and header data. This information can be useful for evaluating security events and troubleshooting network security device issues.
Wireshark's capabilities extend beyond just monitoring to address other network administration tasks:
- Network troubleshooting. Pinpoints and resolves network issues with the comprehensive data Wireshark provides.
- Security analysis. Detects and analyzes potential security threats in the network.
- Performance analysis. Monitors and optimizes network performance to ensure smooth operations.
- Protocol analysis. Gains insights into the behavior of individual protocols within the network.
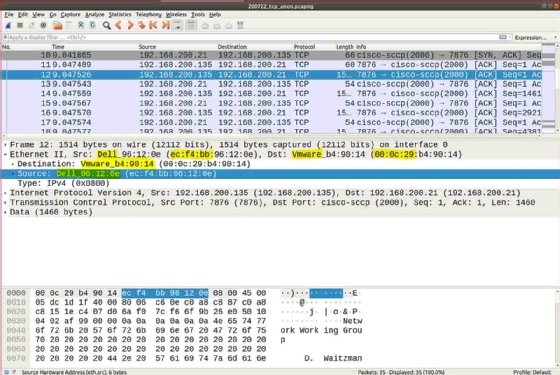
Wireshark user interface
Wireshark typically displays information in three panels. The top panel lists frames individually, with key data on a single line. Any single frame selected in the top pane is further explained in the tool's middle panel.
In this middle section of the display, Wireshark shows packet details, illustrating how various aspects of the frame can be understood as belonging to the data link layer, network layer, transport layer or application layer.
Finally, Wireshark's bottom pane displays the raw frame, with a hexadecimal rendition on the left and the corresponding American Standard Code for Information Interchange values on the right.
Supported file formats in Wireshark
Wireshark is known for its versatility and the wide array of file formats it supports. The primary file format used by Wireshark to save PCAPs is PcapNG, which stands for Packet Capture Next Generation. This format is recognized for its flexibility in capturing and storing packet data.
To support interoperability with third-party protocol analyzers, Wireshark also has the ability to read and save packet data in other file formats, including CAP and PCAP.
Potential areas for concern with Wireshark
Because Wireshark can also be used for eavesdropping, an organization using the tool should make sure it has a clearly defined privacy policy that articulates the rights of individuals using its network, grants permission to sniff traffic for security and troubleshooting issues, and states the organization's policies for obtaining, analyzing and retaining network traffic samples.
As the digital world continues to evolve, tools like Wireshark that offer in-depth insights into network behaviors will remain essential.
See how to customize workflows with Wireshark profiles and how to use Wireshark to sniff and scan network traffic. Learn how to examine a captured packet using Wireshark.
