password entropy
What is password entropy?
Password entropy is a measurement of a password's strength based on how difficult it would be to crack the password through guessing or a brute-force attack. A password's entropy is typically based on the type of characters used -- lowercase letters, uppercase letters, numerical digits or special characters -- and the password's length, or total number of characters.
Password entropy predicts how long it will take to crack a password if sustained attempts to hack it are carried out consistently over a period of time, such as 1,000 attempts per second. For example, a brute-force attack might be able to crack the password accidental in about 58 minutes, according to Security.org, but it might take 7 quadrillion years to crack the password ac@xC1d!3aTlx4$3Hg using today's technology.
Password entropy is usually expressed in terms of bits. The lower the number of bits, the easier it is to guess the password. The higher the number, the more difficult it becomes to crack. An already-known password has 0 bits of entropy; one that can be guessed on the first attempt half the time has 1 bit of entropy. The password accidental has an entropy of 47 bits, and the password ac@xC1d!3aTlx4$3Hg has an entropy of 117.98 bits, which is a very strong password.
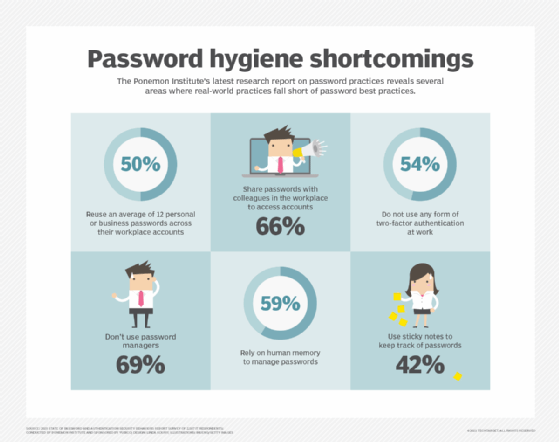
The National Institute of Standards and Technology (NIST) provides the following guidelines for organizations that manage user passwords:
- Set a minimum limit for the password length, such as eight characters.
- Make it possible to create long passwords of at least 64 characters, and encourage users to create longer passwords.
- Don't impose rules about character usage that result in users focusing more on satisfying the rules than on creating good passwords.
- Use a blocklist to prevent users from creating common passwords.
- Encourage users to avoid using personal information or easy-to-guess formulas in their passwords.
- Don't require users to change their passwords arbitrarily, but require them to change their passwords if there is a suspected security breach.
The goal is not to create passwords that are overly complex and difficult to remember, but rather to choose ones that are more memorable yet not easily guessed by anyone else. A user can often remember a longer, simpler passphrase better than a shorter password with an odd mix of characters, and the longer password might also have a greater entropy.
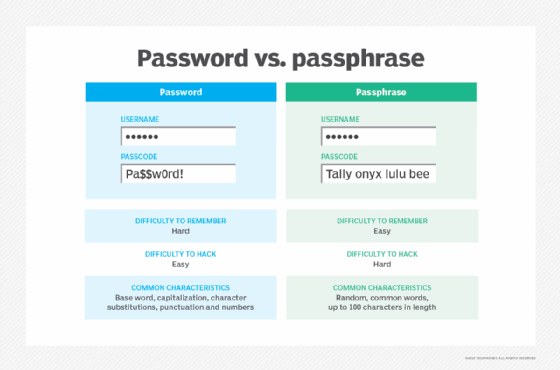
How is password entropy calculated?
A password's entropy can be determined by calculating the base-2 logarithm of the number of possible characters multiplied by the password's length, as expressed by the following formula.
E = log2(RL)
In this formula, E represents the amount of password entropy in bits, R equals the total number of possible characters, and L equals the password's length.
To determine the number of possible characters, you must first identify the types of characters included in the password. The four types commonly used are lowercase letters, uppercase letters, numerical digits, and special characters or symbols. For each included type, you must determine the total number of possible characters in that character set and then add all the set totals together.
The following totals show the breakdown for each character set as they appear on a typical American QWERTY keyboard:
- Lowercase letters (a-z) = 26.
- Uppercase letters (A-Z) = 26.
- Numerical digits (0-9) = 10.
- Special characters (!, @, #, $, %, ^, etc.) = 32.
For example, if a password includes only lowercase letters and numerical digits, you would add 26 and 10 to come up with 36 total possible characters for that password. If a password includes all four types, the total number of possible characters is 94, or 26 + 26 + 10 + 32. Note that some entropy calculations include the space, which raises the total to 95. The following examples should help to make all this clearer.
The first example demonstrates how to calculate the entropy for the password quadrants, which uses only lowercase letters and is nine characters long. To calculate the total number of possible characters, you would normally start by adding the included character sets together. In this case, however, the password contains only lowercase letters, so there is only one set of 26 characters, which means that there are only 26 possible characters. Therefore, the R value in the equation is 26, and the L value is 9 to reflect the password's length.
R = 26 (possible characters)
L = 9 (total characters)
You can now plug these figures into the entropy formula and calculate the total entropy.
E = log2(RL)
E = log2(269) = log2(5429503678976)
E = 42.3 bits (approximate)
As the calculations indicate, the entropy for the password quadrants is 42.3 bits. However, suppose the password is qUa@47!tS, which is still nine characters long, but now contains all four character types. When the four character sets are added together, the R value becomes 94, while the L value remains the same.
R = 26 + 26 + 10 + 32 = 94 (possible characters)
L = 9 (total characters)
As before, you can plug the R and L values into the formula to determine the password's entropy.
E = log2(RL)
E = log2(949) = log2(572994802228616704)
E = 58.99 bits (approximate)
The entropy, which is about 58.99 bits, is now much higher because the password contains all four character types. Instead of including all types, however, you can simplify the password, but make it longer. For example, the password long.quadrants uses only two character types, but is 14 characters long, giving us the following R and L value.
R = 26 + 32 = 58 (possible characters)
L = 14 (total characters)
Once again, you can insert the R and L values into the formula to arrive at the password's entropy.
E = log2(RL)
E = log2(5814) = log2(4875194084160300000000000)
E = 82.01 bits (approximate)
The password has an entropy of 82.01 bits, which is much better than the previous example, even though the password is a lot simpler and consequently easier to remember.
As the examples demonstrate, a longer password can achieve a higher entropy even if it is less complex than a shorter password. In the last example, the password long.quadrants includes two simple words and one period, but it has a much higher entropy than qUa@47!tS, which is more difficult to remember. The second password is also a lot harder to enter into a text box, especially on a device such as a smartphone.
Explore enterprise password security guidelines in a nutshell and see how to create and enforce a password policy across the enterprise. Check out passwordless authentication options and best practices and the differences between a password and a PIN.
