privileged identity management (PIM)
What is privileged identity management (PIM)?
Privileged identity management (PIM) is the monitoring and protection of superuser accounts that hold expanded access to an organization's IT environments.
Oversight of superuser accounts is necessary so that the greater access abilities of these accounts are not misused, abused or neglected. Without this oversight, superuser accounts are unmanaged, which can then lead to loss or theft of sensitive corporate information or introduction of malware that can compromise the entire enterprise IT network.
PIM is a process or program for identifying the privileged accounts, also known as superuser accounts, within an organization. Doing this can help with the monitoring, control and management of the access privileges each superuser has to the organization's resources in order to protect those resources from harm. In addition to being supported by tools on various operating system platforms, PIM also is a named service under Microsoft Entra ID.
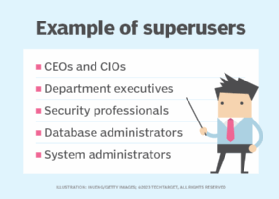
Superusers, such as database administrators and system administrators, can perform actions on an enterprise system that a typical end user cannot. For example, a superuser can change other users' passwords; add, remove or modify user profiles; change device or network configurations; install new programs on enterprise endpoints; or modify enterprise databases or servers.
To prevent the misuse of superuser accounts and protect the organization, it's vital to monitor these accounts on a 24/7 basis. It's also critical to limit the number of such accounts and to remove or modify the accounts when the superuser no longer needs the expanded access, such as when the employee leaves the company. To achieve these goals, PIM is a crucial element of enterprise cybersecurity and information security programs.
PIM is typically implemented to manage the superuser accounts that are allowed to access mission-critical or sensitive assets, which may be files, user accounts, documents, intellectual property, business secrets, application code, databases, security systems or anything else whose loss or compromise may adversely affect the organization.
Why is privileged identity management important for enterprises?
In many organizations, superuser accounts, such as those for database administrators, chief information officers and chief executive officers, are loosely governed. Identity management software often leaves superuser accounts totally uncontrolled, while enabling advanced privileges on the corporate network. Furthermore, the owners of those accounts often have no formal training in managing them, much less in protecting against their misuse and compromise.
If superuser accounts are not properly controlled and managed, threat actors may be able to compromise the accounts in order to access the company's sensitive assets or data. They may also be able to take advantage of vulnerabilities in enterprise systems to steal superuser credentials and then use those credentials to steal enterprise data.
In some cases, adversaries steal privileged account credentials to gain access to the enterprise network and then persist within it to perform long-term surveillance or cause long-term damage. This issue is known as an advanced persistent threat, and it is a common outcome of poor or nonexistent PIM.
By implementing PIM controls and measures, organizations can keep an eye on all privileged accounts. In maintaining such oversight, they can ensure that only those accounts can access and use sensitive accounts. They can also mitigate -- or at least minimize -- many of the security risks that are created by privilege misuse or abuse.
Benefits of privileged identity management
An extensive PIM program increases the security team's visibility into all the privileged users and accounts in the enterprise. This visibility is vital to enable access control and protect enterprise systems, especially those with sensitive data.
Without a PIM program, it's harder to identify and govern superuser accounts. Accounts that are nonoperative -- for example, because the superuser's role has changed or because they have left the organization -- but still valid pose serious security risks. Threat actors can take advantage of such accounts to access enterprise systems and execute many kinds of cyber attacks. An ongoing PIM strategy ensures that these dormant accounts are regularly reviewed and, if necessary, blocked, thus preventing misuse by attackers.
PIM is also important for ensuring regulatory compliance. Many standards, such as General Data Protection Regulation, require that only certain types of individuals are allowed to have superuser access to sensitive enterprise assets. Implementing appropriate PIM tools and policies enables security and compliance teams to meet such regulatory requirements and maintain compliance.
Another advantage of PIM is that it streamlines the process of granting and removing access privileges. The use of automated tools and well-designed PIM workflows enables security personnel to add and remove superusers with minimal hassle, while maintaining a strong security posture for the organization.
Strategies to implement privileged identity management
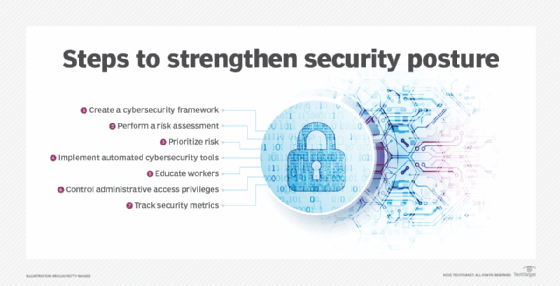
To implement PIM, it can be helpful to follow these proven strategies:
- Create a policy that specifies how superuser accounts are managed and what the account holders should and should not be able to do.
- Develop a management model that identifies a responsible party to ensure that the above policies are followed.
- Inventory privileged accounts to determine how extensive the population is and to identify the holders.
- Establish tools and processes for management, such as provisioning tools or specialized PIM products.
It's also important to identify the attack surface, i.e., all the enterprise assets that are at risk of compromise if a privileged account is misused. Creating an IT asset inventory can show which assets are most in need of protection, which can then provide guidance for the creation of an effective privileged account policy and program.
Deploying two-factor authentication or multifactor authentication, implementing a password policy, and monitoring the behaviors and activities of privileged account holders are some other ways to implement PIM and protect privileged accounts -- and the enterprise -- from bad actors.
Privileged identity management vs. privileged access management
The terms privileged identity management and privileged access management (PAM) are often used interchangeably. However, they are two different, albeit overlapping, concepts in enterprise security. In fact, PIM is a subset of the broader area of PAM.
PAM is about managing privileged accounts and credentials, as well as managing the access rights of those accounts. Thus, in addition to identifying superusers and controlling the list of superusers, PAM aims to control which superuser has what level of administrative access to which enterprise asset.
PAM tools are also used to monitor privileged users so that their privileges are not misused, either by the users themselves or by someone else, such as a malicious threat actor who gets their hands on those credentials.
See how to find the best privileged identity management tool, and weigh privileged identity management tools' pros and cons. Explore the effectiveness of traditional authentication methods and reasons identity and access management is important. Check out identity and access management tools to protect networks.








