threat intelligence (cyber threat intelligence)
What is threat intelligence?
Threat intelligence, also known as cyber threat intelligence (CTI), is information gathered from a range of sources about current or potential attacks against an organization. The information is analyzed, refined and organized and then used to minimize and mitigate cybersecurity risks.
The main purpose of threat intelligence is to show organizations the various risks they face from external threats, such as zero-day threats and advanced persistent threats (APTs). Threat intelligence includes in-depth information and context about specific threats, such as who is attacking, their capabilities and motivation, and the indicators of compromise (IOCs). With this information, organizations can make informed decisions about how to defend against the most damaging attacks.
Why is threat intelligence important?
In a military, business or security context, intelligence is information that provides an organization with decision support and possibly a strategic advantage. Threat intelligence is a part of a bigger security intelligence strategy. It includes information related to protecting an organization from external and inside threats, as well as the processes, policies and tools used to gather and analyze that information.
Threat intelligence provides better insight into the threat landscape and threat actors, along with their latest tactics, techniques and procedures. It enables organizations to be proactive in configuring its security controls to detect and prevent advanced attacks and zero-day threats. Many of these adjustments can be automated so security stays aligned with the latest intelligence in real time.

Threat intelligence helps organizations make informed decisions about how best to secure their IT resources. Find out about both the promises and drawbacks of this security technology.
Types of threat intelligence
There are four varieties of threat intelligence: strategic, tactical, technical and operational. All four are essential to build a comprehensive threat assessment.
- Strategic threat intelligence. This analysis summarizes potential cyberattacks and the possible consequences for nontechnical audiences and stakeholders, as well as decision-makers. It is presented in the form of white papers, reports and presentations, and is based on detailed analysis of emerging risks and trends from around the world. It is used to paint a high-level overview of an industry's or organization's threat landscape.
- Tactical threat intelligence. Tactical intelligence provides information about the tactics, techniques and procedures (TTPs) that threat actors use. It is intended for those directly involved with protecting IT and data resources. It provides details on how an organization might be attacked based on the latest methods being used and the best ways to defend against or mitigate the attacks.
- Technical threat intelligence. This information focuses on signs that indicate an attack is starting. These signs include reconnaissance, weaponization and delivery, such as spear phishing, baiting and social engineering. Technical intelligence plays an important role in blocking social engineering attacks. This type of intelligence is often grouped with operational threat intelligence; however, it adjusts quickly as hackers update their tactics to take advantage of new events and ruses.
- Operational threat intelligence. With this approach, information is collected from a variety of sources, including chat rooms, social media, antivirus logs and past events. It is used to anticipate the nature and timing of future attacks. Data mining and machine learning are often used to automate the processing of hundreds of thousands of data points across multiple languages. Security and incident response teams use operational intelligence to change the configuration of certain controls, such as firewall rules, event detection rules and access controls. It can also improve response times as the information provides a clearer idea of what to look for.
Find out more about how AI and machine learning are changing threat intelligence services and tools.
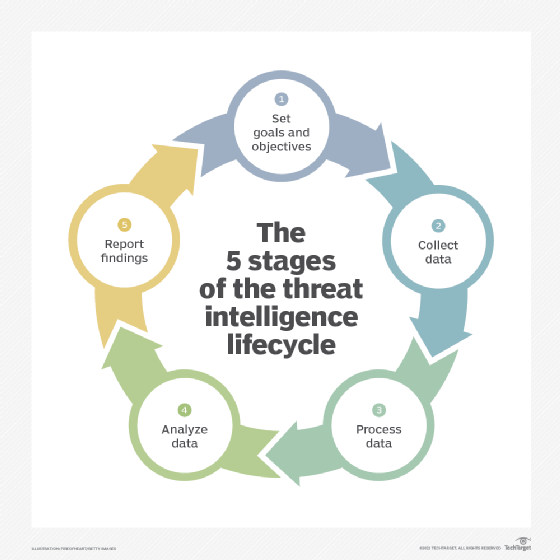
What is the threat intelligence lifecycle?
There are various steps involved in the threat intelligence gathering process, including the following:
Goals and objectives
To select the right threat intelligence sources and tools, an organization must decide what it hopes to achieve by adding threat intelligence to its security solutions and strategy. The goal will most likely be to aid information security teams in stopping potential threats identified during a threat modeling exercise. This requires obtaining intelligence data and tools that can provide up-to-date advice and alerts on the threats considered high risk and high impact. Another important objective is to ensure the right strategic intelligence is collected and provided to C-level management so it is aware of changes to the organization's threat landscape.
Data collection
Logs from internal systems, security controls and cloud services form the foundation of an organization's threat intelligence program. However, to gain insights into the latest TTPs and industry-specific intelligence, it's necessary to collect data from third-party threat data feeds. These sources include information gathered from social media sites, hacker forums, malicious IP addresses, antivirus telemetry and threat research reports.
Data processing
Gathering and organizing the raw data needed to create actionable threat intelligence requires automated processing. It is not viable to manually filter, add metadata, and correlate and aggregate varied data types and sources. Threat intelligence platforms or applications use machine learning to automate data collection and processing, so it can continuously provide information about the activities of threat actors.
Analyze data
This step involves finding answers from the processed data to questions such as when, why and how a suspicious event occurred. This step would answer questions about when a phishing incident happened, what the perpetrator was after and how phishing emails and a malicious domain are linked and how they're being used.
Report findings
Reports must be tailored to a specific audience so it is clear how the threats covered affect their areas of responsibility. Reports should be shared with the wider community when possible to improve overall security operations.
Get a better understanding of the threat intelligence lifecycle. AT&T Cybersecurity researcher Tom Hegel discusses how to go about building a framework for this technology.
Threat intelligence tools
There are numerous tools that can help organizations collect data and apply threat intelligence within existing security operations. Threat intelligence services also provide organizations with information related to potential attack sources relevant to their businesses; some also offer consultation services.
Some of the available tools include:
- Anomali ThreatStream pulls together threat intelligence from various sources and provides tools for investigations.
- Cyberint's Argos Digital Risk Protection Platform is a SaaS platform designed to analyze an organization's attack surface and the cyberattacks targeting its industry from the open, deep and dark webs.
- Kaspersky Lab's Kaspersky Threat Intelligence collects petabytes of data to generate threat intelligence feeds of actionable cyberthreat data and insights on the threats targeting particular industries.
- PhishLabs' Digital Risk Protection monitors the web for social media threats, data leakage, brand impersonation and account takeover.
- SOCRadar's ThreatFusion Cyber Threat Intelligence module gathers data from deep and dark webs. It uses intelligence feeds from several sources to alert security teams of potential threats and threat actors targeting an industry.
Learn about five other cyber threat intelligence feeds that might be worth considering.