traceroute
What is traceroute?
Traceroute is a command-line utility that returns information about the communication route between two nodes on an Internet Protocol (IP) network. The utility sends out User Datagram Protocol (UDP) test packets and tracks their path as they travel from the system where the utility is running -- the source -- to the destination, which might be a server, router or other device on the network.
Administrators and analysts can use traceroute as a diagnostic tool to troubleshoot network and connectivity issues. They can verify which network path their data is traveling and identify any places where there might be problems or unusual routing patterns.
Traceroute is included with Unix and most Unix-like operating systems, including Linux, macOS, FreeBSD and IBM AIX. If it's not included, users typically can install it manually, often for free, using a package manager such as Yellowdog Updater, Modified or sudo apt.
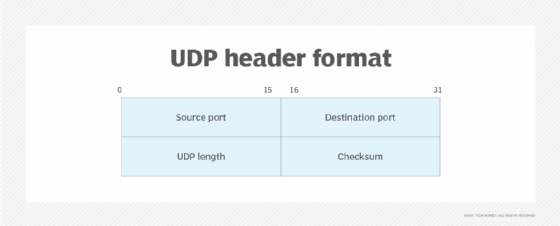
Though traceroute is not included with Windows systems, Microsoft offers a comparable utility called tracert. The tracert utility returns information similar to what traceroute provides. The primary difference between the two is that traceroute transmits UDP packages by default, whereas tracert transmits Internet Control Message Protocol (ICMP) echo request packets. However, traceroute includes an option for sending ICMP echo packets rather than UDP packets.
Traceroute is often compared to the ping utility, which can also be used to troubleshoot network issues. But the two serve different purposes. Ping can only verify connectivity between two network nodes; it provides no routing information. For that, a user needs traceroute or a comparable tool.
How traceroute works
When two nodes communicate across the internet or a large private IP network, data packets travel -- or hop -- from one gateway to the next until they reach their destination. Traceroute gathers details about these gateways and generates a list that shows the hostname and IP address of each one, if the information is available. The utility also records the time it took, in milliseconds, for the UDP packet to travel round-trip between the source computer and the specific gateway.
When you run a traceroute command, the utility sends a packet with a time limit of 1. This is known as the time-to-live (TTL) value, which indicates the number of permitted hops. In this way, the limit will be exceeded when it reaches the first gateway that receives the package, causing the gateway to return a time exceeded message. Traceroute uses this message to determine the round-trip time for the data to travel between the source computer and the first gateway.
After receiving the time exceeded message, traceroute increases the TTL value by 1 so that it will be exceeded when it is received by the second gateway in the path rather than the first. Upon receiving the packet, the second gateway returns its own time exceeded message, which traceroute once again uses to determine the round-trip time. This process continues for each hop in the path until the packet reaches its final destination or the request exceeds the total number of permitted hops.
Traceroute determines when a packet has reached its destination by including a port number that is outside the normal range. When the destination receives the packet, it returns a port unreachable message, which enables the utility to measure the time length of the final hop.
While a traceroute command is running, it displays information about each hop in the route path between the source and destination, listing the details one hop at a time. By default, traceroute sends out three probes to each gateway and then displays the results for each probe. The user can override the default number of probes when running a traceroute command.
If information about the gateway is not available for a specific probe, the utility will instead display an asterisk. This can occur if the gateway fails to respond for any reason. For example, it might be configured to disregard traceroute requests, or it might be too busy to respond to such requests. If a hop is listed with three asterisks, it means that all three probes failed to gather information about the gateway.
Running a traceroute command
To run a traceroute command, the user must specify, at a minimum, the utility's name, traceroute, and the destination's hostname or IP address. For example, the following command runs a traceroute request against TechTarget's site in Brazil.
traceroute www.techtarget.com.br
The following screenshot shows the last 12 hops returned by this traceroute command, which originated on the U.S. West Coast. The path includes destinations in California and Brazil, with other possible locations in between.

The left-hand column lists the hop numbers. The first hop shown is the 14th, and the last hop is the 25th, which is the destination. Each hop reflects the three probes for that specific gateway. For example, hop 23 shows a gateway in Brazil. The gateway's hostname is dist-fvcg2ita001.locaweb.com.br, and its IP address is 179.188.36.92. This information is followed by the three round-trip times, one for each probe.
In some cases, the hostname will give you a clear sense of its location, as in hop 14, which indicates that the gateway is in Great Oaks, Calif.
Hop listings often show two or three IP addresses. This can occur for a number of reasons, such as high traffic volumes or active load-balancing operations. For example, hop 22 indicates that the first two probes went to one IP address and the third probe went to a second IP address. The times associated with each IP address indicate the number of probes to that address.
Some listings include only the IP address and no hostname. You can often look up an address on a site such as whatismyipaddress.com. This can be useful in trying to better understand how traffic is being routed across the internet or where roadblocks might exist. These sites will often provide details about who is hosting a gateway and where it is located. If a listing includes nothing but three asterisks, as in hop 19, you can assume that the gateway did not respond to any of the probes. In that case, there is little you can learn from this listing other than that a hop was made.
Traceroute supports a number of options for controlling the utility's behavior and output. The exact options depend on the underlying operating system and its version of traceroute, although many options are common across systems. For example, different versions commonly support the -P option, which lets you specify an IP protocol such as ICMP or Transmission Control Protocol, rather than using the default UDP. Another common option is -q. With this one, you can specify the number of probes per hop, thus overriding the default three.
