e-signature (electronic signature)
What is an e-signature (electronic signature)?
An e-signature (electronic signature) is a digital version of a conventional handwritten signature. In many countries, including the United States, an e-signature can provide the same legal commitment as a handwritten signature if it meets certain criteria.
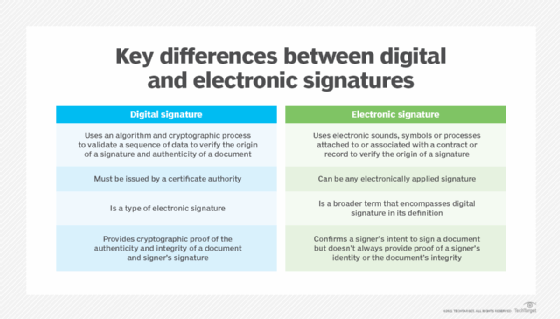
The terms e-signature and digital signature are often used interchangeably, although this is incorrect. A digital signature is a type of e-signature, but not all e-signatures are digital signatures.
An e-signature provides a quick and easy way to sign electronic documents without the need to print paper or affix wet ink signatures. Essentially, it is a process where computers are used to certify the integrity of a document and to authenticate the person signing the document (signer).
E-signatures don't require pen and paper but allow the parties involved to agree with or approve a document, just like they would do with handwritten signatures.
Secure and legally enforceable, e-signatures can replace handwritten signatures for many documents and in many processes. Advanced e-signatures are backed by technology to ensure the authenticity of signatures and signers, as well as the integrity of documents.
E-signatures vs. digital signatures
As mentioned, the terms e-signature and digital signature are often confused and used incorrectly as synonyms. An e-signature is a broader category referring to any signature that is transmitted electronically. Thus, it may be a digitally produced signature on a document, or it may be generated through an electronic document-signing service.
A digital signature is a specific type of e-signature with advanced features to maintain security and compliance. Digital signatures use mathematics, certificate authorities (CAs) and cryptographic algorithms to authenticate the signer and validate the authenticity and integrity of a message, software or digital document.
Types of e-signatures
There are three standards for e-signatures:
- Simple electronic signature (SES).
- Advanced electronic signature (AES).
- Qualified electronic signature (QES).
SES is the most basic -- and least secure -- type of e-signature. It refers to any method of applying an electronic signature, such as a typed name or other digital reproduction of a signature, to digital documents, such as contracts and agreements. It requires no identity verification from the signer and uses no encryption or authentication. As a result, an SES is easy to falsify and the most susceptible to fraud, making it suitable for lower-risk transactions.
AES provides more robust security by ensuring that only the intended signer can access and sign a document, thus reducing the risk of fraud. This is typically accomplished through the use of public key infrastructure to generate and attach a digital certificate to the e-signature. The signer maintains sole control of the private key, which serves to verify their identity. Additionally, when the AES-signed document is opened by the recipient, the CA verifies that no changes have been made to the file. It is recommended for moderate-risk transactions.
QES is the most secure and fraud-resistant form of e-signatures, yet also the most complex. In the EU, it is legally equivalent to a handwritten signature. It contains all the security measures used in AES, plus additional forms of identity authentication, such as a face-to-face or video verification through a Qualified Trust Service Provider.
Legality of e-signatures
The laws of most countries also legally define what an electronic signature is, where it can be used and where it cannot be used (e.g., to sign wills). E-signatures are legally binding in many countries, meaning they have the same legal authority as handwritten signatures.
The U.S. law enshrining the validity of e-signatures is the E-Sign Act, passed in 2000. The European Union's eIDAS (electronic IDentification, Authentication and trust Services) regulates e-signatures in Europe.
In many countries, an e-signature is as legally valid as a handwritten signature if it meets these four criteria:
- Intent to sign. The signatory intends to verify his or her identity when signing the document.
- Consent to do business electronically. The signatory agrees to do business electronically for which the document has been created.
- Association of signature with the record. The system used to capture the e-signature can verify the process by which the signature was created.
- Record retention. The e-signature is stored for the required amount of time so it can be referenced by all interested and authorized parties.
The benefits of e-signatures
E-signatures speed up many documentation workflows by accelerating approvals and agreements. Also, they eliminate the need to print, sign, scan and resubmit documents -- processes that can lead to delays if the signer does not have access to the necessary technology. Because they do not require paper, e-signatures are an environmentally friendly alternative to handwritten signatures.
E-signatures also provide flexibility and convenience by allowing signers to use their preferred device and signing application. E-signature solutions are portable, so the parties involved in a transaction can both sign and request e-signatures, regardless of their global location.
Applications of e-signatures
E-signatures can be used in many scenarios where handwritten signatures are used. Examples include contracts (e.g., sales or employment), transactions (e.g., online banking) and administrative procedures (e.g., tax declarations).
That said, simple e-signatures are best suited for documents that don't contain sensitive data or must meet stringent compliance or security standards. For documents that are subject to rigorous security and compliance standards and certain legal requirements, it is better to sign documents using more secure digital signatures.
Many corporate departments such as the following can save time, money and paper using e-signatures:
- Finance and accounting.
- HR.
- IT.
- Marketing.
- Sales.
Many industries are also adopting e-signatures, including the following:
- Financial services.
- Government.
- Legal.
- Life sciences and healthcare.
- Manufacturing.
- Retail.
E-signature workflows
An e-signature workflow is a systematic and chronological series of steps that makes it easy to electronically sign digital documents. The workflow can automate some or all of the signing process to accelerate completion, increase process transparency and increase the trust between the parties involved in the transaction. Moreover, a proper workflow ensures that all e-signed documents (and their contents) are secure and that document recipients can authenticate the signatory's identity.
An e-signature workflow typically follows these steps:
- Sender/signatory creates the document and uploads it to the e-signature solution.
- Signatory digitally sends the document to the recipient.
- Recipient reviews the document.
- Recipient signs the document and returns it to the sender (or to other intended parties).
- The signed documents are stored in a secure location to enable future access.
- An authorized person sends the link to access the document to other authorized parties.
How to choose an e-signature product
When it comes to selecting an e-signature product, it is important to consider the organization's needs and how the solution would integrate into existing and desired documentation workflows. For many industries and use cases, it is preferable to select a solution that balances legal enforceability and ease of use.
In addition, the e-signature solution should be able to demonstrate the validity of signatures and that it can prevent document tampering and fraud. Features like audit trails are also desirable.
Learn about six e-signature software providers.







