
15 server and networking interview questions and answers
Securing a job in the dynamic world of server and network administration often hinges on successfully navigating the interview process. While technical expertise is important, knowing what questions to expect and how to respond effectively can be just as crucial.
Reviewing fundamental concepts such as IP addresses and domain name servers, along with real-world troubleshooting scenarios, can prepare interview candidates with the knowledge and clarity to approach each one with confidence. Going into an interview, it's important to be prepared in the following ways:
- Technical expertise. Brush up on core concepts such as subnetting, routing protocols and network security principles. Practice troubleshooting common network issues and become familiar with relevant tools and technologies.
- Communication skills. Articulate answers clearly and concisely to demonstrate the ability to explain technical concepts to nontechnical audiences. Practice active listening and ask clarifying questions to ensure the interviewer's intent is fully understood.
- Confidence and professionalism. Maintain a positive and enthusiastic demeanor throughout the interview. Dress professionally and arrive on time, demonstrating respect for the opportunity.
While there is some overlap, the following review questions are divided into three categories: servers, system design and networking.
Server-specific questions
The following questions are related to servers:
1. What is Windows Server?
Microsoft Windows Server is an enterprise-class OS. It is designed to share services with multiple users and to provide extensive administrative control of data storage, apps and corporate networks. It's been around in one form or another since the early 1980s, when Microsoft produced two OS lines: MS-DOS and Windows NT. Symmetric multiprocessing, which makes applications run faster on machines with several processors, is a feature in the NT architecture.
Later iterations of Windows Server can be deployed either on premises or on a cloud platform, such as Microsoft Azure. Key features in later versions of Windows Server include the following:
- Active Directory (AD). Automates the management of user data, security and distributed resources, and enables interoperation with other directories.
- Server Manager. A utility to administer server roles and make configuration changes to local or remote machines.
If this question is asked, the interview candidate will likely be expected to show proficiency with current versions of Windows Server 2019 and 2022, Microsoft System Center Virtual Machine Manager 2022 and SQL Server PowerShell. They might also be expected to support Active Directory, Exchange, SQL Server, SharePoint, Microsoft 365, Azure, Citrix and Hyper-V.
2. What are proxy servers and why are they important?
A proxy server is a dedicated computer -- or a software system running on a computer -- that acts as an intermediary between an endpoint device, such as a computer, and another server from which a user or client is requesting a service.
To the user, the proxy server is invisible; all internet requests and returned responses appear to be directly with the addressed internet server.
Proxy servers are used for both legal and illegal purposes. Legitimate purposes include facilitating security, providing administrative control or providing caching services. Illegitimate purposes include monitoring traffic to undermine user privacy. An advantage of a proxy server is that its cache can serve all users. If one or more internet sites are frequently requested, these are likely to be in the proxy's cache, which improves user response time. A proxy can also log its interactions, which can be helpful for troubleshooting.
3. How would you recover lost files from a system infected by a virus?
If asked this question, know that the interviewer has had some firsthand experience. The interviewee can explain what they would have done to avoid the loss in the first place -- as long as they don't sound condescending.
Explain that the data recovery would depend on a number of circumstances, including which virus was the culprit. The recovery would also be limited by the data recovery software used to create the backup and the backup target media.
Communicate that it would need to be determined whether the actual files were corrupt or just the reference files -- such as the file allocation table that Windows uses -- to track which files are on the hard drive and where they are stored.
Also, note what would be done to retrieve files that were not backed up and accidentally deleted from a computer's file system -- knowing that they likely still remain on the hard disk in fragments.
Finally, mention if specific recovery tools or third-party services have been used.
4. What's the difference between a firewall and antivirus software?
Firewalls and antivirus software are typically used in tandem to protect data and access to the servers in which they reside.
Firewall software prevents intruders from gaining unauthorized access to a private network, and ultimately, the servers. They do this by establishing a border between an external network and the network they guard. The firewall inspects all packets entering and leaving the guarded network. As it inspects, it uses a set of preconfigured rules to distinguish between benign and malicious packets.
Antivirus software protects the data and servers from malware, such as viruses and worms. The software typically runs in the background, scanning servers and other network devices to detect and restrict the spread of malware. Many antivirus software programs include real-time threat detection and protection to guard against potential vulnerabilities as they happen, as well as system scans that monitor device and system files looking for possible risks.
5. What's the difference between Tomcat and the Apache Web Server?
Purpose. The purpose of the Apache HTTP Server is to serve static files -- such as text, HTML, images, audio and video files -- to web-based clients.
The Apache Tomcat server delivers content that changes. These changes depend on who the client is, whether the client has signed in and what the client has done on previous interactions with the server.
Prerequisites. The Apache HTTP Server has no prerequisites. It can be installed on any computer that runs a modern edition of Windows, a Linux distribution or Unix. Tomcat requires a JDK installation, along with a properly configured JAVA_HOME environment variable. The dynamic nature of Apache Tomcat comes from logic implemented in Java code that is written and deployed to it.
6. What professional server certifications do you have?
Here, the interviewer wants to know if the candidate has picked up relevant certifications such as Microsoft Certified certifications, VMware Certified Professional or others.
In 2020, Microsoft retired several server certifications in favor of role-based certifications for Azure. Candidates should prepare to explain how their certifications are still applicable to the job, as there are still many on-premises Windows Server deployments in enterprises.
7. What role do servers typically play in IT monitoring?
IT monitoring covers three sections: the foundation, software and interpretation.
Servers are included in the foundation, which is the lowest layer of a software stack. The foundation also includes CPUs and VMs.
IT monitoring can rely on agents or be agentless. Agents are independent programs installed on the monitored device to collect hardware or software performance data, reporting it to a management server. Agentless monitoring uses existing communication protocols to emulate an agent with many of the same functionalities.
For example, to monitor server use, an IT administrator installs an agent on the server. A management server receives that data from the agent and displays it to the user via the IT monitoring software interface, often as a graph of performance over time. If the server stops working as intended, the tool alerts the administrator who can repair, update or replace the item until it meets the standard for operation. It might be beneficial to review the essentials of server monitoring.
System design questions
The following questions are related to system design:
8. What is Active Directory?
Active Directory is a Microsoft product. It consists of several services that run on Windows Server to manage permissions and access to networked resources. AD stores data as objects, which are single elements such as a user, group, application or device. It categorizes objects by name and attributes. For example, a user's name might include the name string, along with information associated with the user, such as passwords and Secure Shell (SSH) keys.
The main service in Active Directory is Domain Services (AD DS), which stores directory information and handles the user's interaction with the domain. AD DS verifies access when a user signs into a device or attempts to connect to a server over a network. Administrators typically have different levels of access to data than users. It is important to note that on-premises AD DS differs from Microsoft Azure Active Directory.
If asked about Active Directory, the interview candidate should be comfortable explaining Group Policy. Group Policy is the hierarchical infrastructure that lets a network administrator in charge of Microsoft's Active Directory implement specific configurations for users and computers. Candidates should explain how they've used Group Policy to define security settings.
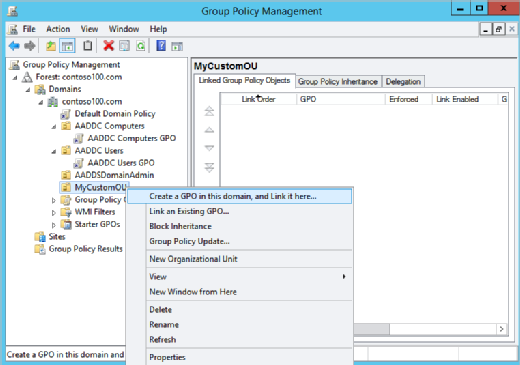
9. What IT automation tools have you used with servers?
These software tools replace a series of actions and responses between an administrator and the IT environment. Here, the interviewer wants to know what experience the interviewee has had with Microsoft's PowerShell, Broadcom's CA Server Automation, BMC Software's BladeLogic Server Automation or other tools that automate system tasks, such as batch processing.
Candidates are most likely to be asked about PowerShell. PowerShell has emerged as a critical tool for systems administrators by providing a consistent, adaptable technology for managing on-premises and cloud-based systems. Microsoft launched PowerShell in 2006 to work solely in the Windows environment, but the company open sourced the technology in 2016. Today, the tool aims to appeal to a wider range of admins, as it's now also available for Linux and macOS. PowerShell has also made the jump to broader computing models, spanning cloud environments such as Microsoft Azure and AWS.
If you are asked about PowerShell, be prepared to explain the benefits of Desired State Configuration (DSC) and its push and pull modes of operation.
10. What is a domain controller?
This is as much a history question as it is a science question. The interviewer might be fishing to see if the candidate knows that before Windows 2000, Microsoft's domain controllers were referred to as the primary domain controller (PDC) and backup domain controller (BDC) and were roles that could be assigned to a Windows NT network. They later became an integral part of AD.
In any case, the role of a domain controller is to serve as a gatekeeper, responding to security authentication requests within a computer domain. At the simplest level, it provides or denies access -- for example, by a username and password -- to domain resources.
Networking questions
The following are some questions related to networking:
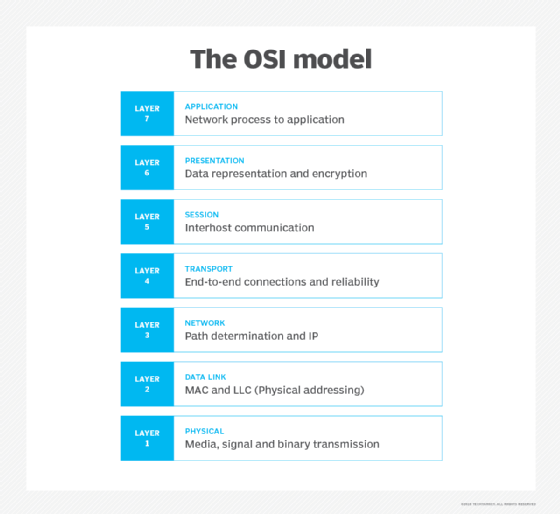
11. How many layers are in the OSI Model? Name and explain them.
Open Systems Interconnection (OSI) models how data is sent or received over a network. This model breaks down data transmission over a series of seven layers, each of which is responsible for performing specific tasks concerning sending and receiving data.
Interview candidates might be asked to distinguish between OSI and TCP/IP. The main similarity is that they both have a layered construction. However, the OSI model consists of seven layers, while TCP/IP consists of four layers.
The main concept of OSI is that the process of communication between two endpoints in a network can be divided into seven distinct groups of related functions or layers. Each communicating user, or program, is on a device that can provide those seven layers of function.
The seven OSI layers are as follows:
- Layer 7: The application layer. The is the top of the OSI communications model. The application layer provides services for an application program to ensure that effective communication with another application program on a network is possible.
- Layer 6: The presentation layer. The presentation layer ensures that the communications that pass through it are in the appropriate form for the recipient application.
- Layer 5: The session layer. The session layer manages the setup and teardown of the association between two communicating endpoints.
- Layer 4: The transport layer. The transport layer ensures the reliable arrival of messages across a network and provides error-checking mechanisms and data flow controls.
- Layer 3: The network layer. The network layer's primary function is to move data into and through other networks.
- Layer 2: The data link layer. The data link layer serves as the protocol layer in a program that handles the moving of data into and out of a physical link in a network.
- Layer 1: The physical layer. This is the lowest layer of the OSI communications model. The physical layer's function is to transport data using electrical, mechanical or procedural interfaces.
12. Explain the difference between a client and a server in simple terms.
Because client-server computing is nearly ubiquitous, it should be a fairly straightforward explanation of how one program (the client) requests a service or resource from another program (the server). Spend time explaining the pros and cons of the client-server model, as well as the basics of client-server protocols, particularly TCP/IP.
An important advantage of the client-server model is that its centralized architecture helps make it easier to protect data with access controls that security policies enforce. Also, it doesn't matter if the clients and the server are built on the same OS because data is transferred through client-server protocols that are platform-agnostic. An important disadvantage is that if too many clients simultaneously request data from the server, it might become overloaded. In addition to causing network congestion, too many requests might result in a denial of service.
As for the client-server protocols, explain that clients typically communicate with servers by using the TCP/IP protocol suite. TCP is a connection-oriented protocol, which means a connection is established and maintained until the application programs at each end have finished exchanging messages. It determines how to break application data into packets that networks can deliver; sends packets to and accepts packets from the network layer; manages flow control; and handles retransmission of dropped or garbled packets, as well as acknowledgement of all packets that arrive. In contrast, IP is a connectionless protocol, which means there is no continuing connection between the endpoints that are communicating. Each packet that travels through the internet is treated as an independent unit of data, without any relation to any other unit of data.
13. How do domain name servers function?
There are three types of domain name servers: DNS stub resolver servers, DNS recursive resolver servers and DNS authoritative servers. Domain name servers answer questions from both inside and outside their own domains. When a server receives a request from outside the domain for information about a name or address inside the domain, it provides the authoritative answer. When a server receives a request from inside its own domain for information about a name or address outside that domain, it passes the request out to another server. Usually, this server is one managed by its internet service provider (ISP).
If that server does not know the answer or the authoritative source for the answer, it reaches out to the domain name servers for the top-level domain (e.g., for all of .com or .edu). Then, it passes the request down to the authoritative server for the specific domain (e.g., techtarget.com or stkate.edu). The answer flows back along the same path.
14. Differentiate among attenuation, distortion and noise.
Attenuation in computer networking is the loss of communication signal strength, measured in decibels (dB). As the rate of attenuation increases, the transmission -- such as an email a user is trying to send or a phone call -- becomes more distorted. Attenuation can occur on computer networks due to range, interference (e.g., by radio interference or physical obstructions) or wire size (the thinner the wire, the greater attenuation).
Distortion refers to the change in shape of a signal. Distortion happens most often when signals are composites of different signals on various frequencies travelling across different mediums.
Noise is probably the most recognizable of the three. It describes a jumble of mixed signals, thermal noise and other noises.
15. What are the benefits of using subnets?
There are three key benefits to using subnets, which represent the logical partition of an IP network into multiple, smaller network segments:
- Reallocating IP addresses. Each class has a limited number of host allocations; for example, networks with more than 254 devices need a Class B allocation. If a network administrator is working with a Class B or C network and needs to allocate 150 hosts for three physical networks located in three different cities, they would need to either request more address blocks for each network or divide a network into subnets that let administrators use one block of addresses on multiple physical networks.
- Relieving network congestion. If much of an organization's traffic is meant to be shared regularly among the same cluster of computers, placing them on the same subnet can reduce network traffic and improve performance. Without a subnet, all computers and servers on the network would see data packets from every other computer.
- Improving network security. Subnetting lets network administrators reduce network-wide threats by quarantining compromised sections of the network and by making it more difficult for trespassers to move around an organization's network.
As with any job interview, it's important for the candidate to anticipate questions from the interviewer and come prepared. It can be helpful to practice answering these questions by participating in mock interviews with a partner who has experience with servers, systems design and networking, as they can provide constructive feedback.




