
computer security incident response team (CSIRT)
What is a CSIRT?
A computer security incident response team, or CSIRT, is a group of IT professionals that provides an organization with services and support surrounding the assessment, management and prevention of cybersecurity-related emergencies, as well as coordination of incident response efforts.
The main goal of a CSIRT is to respond to computer security incidents quickly and efficiently, thus regaining control and minimizing damage. This involves following National Institute of Standards and Technology's (NIST) four phases of incident response:
- preparation
- detection and analysis
- containment, eradication and recovery
- post-incident activity
To do so, CSIRTs may take on many responsibilities, including the following:
- create and update incident response plans;
- maintain and communicate information to internal and external entities;
- identify, assess and analyze incidents;
- coordinate and communicate response efforts;
- remediate incidents;
- report on incidents;
- manage audits;
- review security policies; and
- recommend changes to prevent future incidents.
A central assumption of this definition is that a CSIRT is an organized entity with a defined mission, structure, and roles and responsibilities. This assumption excludes any ad hoc or informal incident response activity that does not have a defined constituency or documented roles and responsibilities. This assumption is driven by the belief that, without a formalized incident response capability, it is not possible to deliver effective incident response.
The Forum of Incident Response and Security Teams, an international association of incident response teams, released the "FIRST CSIRT Framework." This detailed document builds on Computer Emergency Response Team Coordination Center (CERT/CC) guidance that has been used since the late 1980s. The framework also outlines service areas CSIRTs could offer constituents, including information security event management, infosec incident management, vulnerability management, situational awareness and knowledge transfer.
CSIRT attributes and processes
While every CSIRT is unique to its organization, in general, CSIRTs have three attributes that differentiate them from other incident response teams: their mission statement, constituency and list of services.
Mission statement
The CSIRT mission is a statement of purpose or its reason for existing. A CSIRT's mission defines its areas of responsibility and serves to set expectations with its constituency.
An example CSIRT mission statement may be: "It is the mission of XYZ CSIRT to protect XYZ Corp. by creating and maintaining the capability of detecting, responding and resolving computer and information security incidents."
Constituency
A CSIRT constituency must be clearly defined. This is the customer base or recipients of incident response services. The constituency is assumed to be unique to a given CSIRT and is often its parent organization.
List of services
The CSIRT mission is carried out through the delivery of CSIRT services to its constituency. CSIRTs may offer several services, but there are fundamental ones that a CSIRT must offer to be considered a formal incident response team. At its most basic level, a CSIRT must be able to do the following:
- Receive an incident report from a constituent. In order to receive an incident report from a CSIRT constituency, the constituency first needs to know the CSIRT exists. Constituents also need to understand what the CSIRT does and how its services are accessed, as well as the service and quality levels it can expect. Thus, the CSIRT needs to have defined its mission and services, announced itself to its constituency and published guidance on how incident services are requested. This includes publishing an incident response policy, processes, procedures, forms and resources necessary to inform and enable constituencies to file incident reports.
- Analyze an incident report to validate and understand the incident. Once an incident report has been received, the CSIRT analyzes the report to validate that an incident or other type of activity that falls under the CSIRT mission has indeed occurred. The CSIRT then determines if it understands the report and the incident well enough to create an initial response strategy that fulfills the goals of regaining control and minimizing damage. Part of being able to analyze an incident report and respond efficiently is having staff that can perform a variety of tasks. Members of the CSIRT should have written plans, policies and procedures that document their specific roles and responsibilities.
- Provide incident response support. Depending on how the CSIRT is organized and the services offered, a CSIRT may provide incident response support via the following:
- on-site incident response services delivered directly to the constituent;
- incident response services delivered over email or the phone; or
- coordinated incident response services that combine and allocate the efforts of multiple incident response teams across multiple constituents.
In some situations, an organization's CSIRT may only develop and oversee incident response strategies and services rather than implement them. For example, other groups or departments, such as network engineers or system and data owners, may carry out the response strategy with the CSIRT managing the effort.
How is a CSIRT structured?
How a CSIRT is structured depends on its parent organization's needs. For example, consider if 24/7 coverage is needed, the availability of trained employees, whether full- or part-time team members are required, and operating costs.
There are several common CSIRT structures, including the following:
- Centralized CSIRT. In a centralized CSIRT, a single incident response team serves the entire organization, and all incident response resources are contained within the dedicated unit. This model is well suited for small organizations or organizations with limited geographic scope.
- Distributed CSIRT. In a distributed CSIRT, several independent incident response teams exist. The distribution of CSIRT resources may depend on wide geographic scope of the organization or the location of its major facilities. Other attributes that include whether a company is organized by a business unit structure or simply by the distribution of employees and information assets may also influence the CSIRT's distribution. Additionally, most distributed CSIRT models require a coordinating CSIRT.
- Coordinating CSIRT. This CSIRT manages other, often subordinate, CSIRTs. This CSIRT coordinates incident response activities, information flow and workflow among distributed teams. A coordinating CSIRT may not provide any independent incident response services itself. Instead, it focuses on the efficient and effective use of resources in the distributed teams. For example, CERT/CC, the Software Engineering Institute's (SEI) computer emergency response team, is a coordinating CSIRT that orchestrates activities among national, governmental and regional CSIRTs.
- Hybrid CSIRT. A hybrid CSIRT combines attributes of centralized and distributed CSIRTs. The central CSIRT component is often full time, and the distributed component is composed of subject matter experts (SMEs) who may not be attached to incident response activities except as needed during security events. In this model, when the central CSIRT detects a potential event, it analyzes the incident and determines the response needs. Then, the appropriate distributed CSIRT experts can be called up to assist in these activities. Though a hybrid CSIRT relies on SMEs who are not full-time CSIRT members, it is definitively a formal incident response team. The hybrid CSIRT's distributed units of experts are designated as incident response professionals with defined roles and responsibilities and receive formal incident response training. They may also be required to obtain and maintain incident handler certifications.
- CSIRT/SOC hybrid. In this specialized hybrid model, the security operations center (SOC) is responsible for receiving all alerts, alarms and reports indicating potential incidents. If the SOC requires help with additional analysis, the CSIRT is activated. In general, the SOC acts as a front end for the CSIRT, performing incident detection, and then passes incidents to the CSIRT to handle.
- Outsourced CSIRT. An outsourced CSIRT can be a helpful option for companies that lack the resources or staff to build an in-house team. This CSIRT model involves staffing an internal CSIRT with contractors rather than employees or outsourcing CSIRT tasks and services that may be only occasionally needed, such as digital forensics.
How to build a CSIRT
Developing an effective incident response strategy means an organization can detect and respond to a computer or infosec incident in a way that limits damage and keeps recovery costs as low as possible.
When developing an incident response team, consider the following:
- Decide what types of technical backgrounds, roles and responsibilities are required.
- Assign a team leader to oversee CSIRT efforts, as well as communicate incidents and progress to the executive leadership.
- Determine the proper CSIRT organizational model and the required functioning hours for the team.
- Create security plans, policies and procedures for a variety of potential threats and incidents.
- Provide CSIRT members with routine cybersecurity education and awareness training.
- Conduct systemwide risk assessments.
- Identify critical incident response assets, including data, business processes, technology and people.
- Have a well-documented asset management plan.
- Implement a configuration management program to ensure all software is patched and any updates are tested and applied in a timely manner.
- Execute a defensive network architecture using routers, firewalls, intrusion detection and prevention systems (IDSes/IPSes), network monitors and security operations.
CSIRT member roles: Who should be on the team?
An effectively functioning CSIRT requires an array of members with various skills and responsibilities. There is no one-size-fits all approach, however. Organizations must staff and train employees to meet their specific security incident response needs.
Several factors affect the organization of CSIRT roles, including the organization's risk profile and CSIRT structure. In general, CSIRT members include the following:
- CSIRT team lead. This executive role, typically occupied by the chief information security officer (CISO), communicates incidents with C-suite executives and coordinates the CSIRT budget.
- Incident manager. This role coordinates CSIRT meetings, ensures accountability from CSIRT members across the organization and determines whether incident findings should be escalated to executives.
- Supporting CSIRT staff. These technical roles, such as the security analyst, incident handler, shift lead or forensics investigator, are responsible for incident detection, response and reporting activities.
- Cross-functional CSIRT roles. To carry out its mission, a CSIRT often incorporates legal, human resources (HR) and public relations (PR) professionals into the team. For example, a member of the legal team advises on potential lawsuits from shareholders or employees, as well as the incident disclosure process. An HR role in the CSIRT manages personnel issues and communicates incidents to employees. PR staff handle press releases; employee, partner, customer and stakeholder communications; and media inquiries regarding security incidents.
What should CSIRT members do? Skills and responsibilities
CSIRT staff play a critical role in upholding the CSIRT mission and service. An effective CSIRT requires staff members to maintain a diverse range of technical and nontechnical skills.
Technical skills
CSIRT staff need a baseline of technical skills and security knowledge to perform daily tasks. A general understanding of security principles, vulnerabilities, programming and network protocols constitute this baseline. In addition, CSIRT staff should be trained in the following technical skills for incident handling:
- identifying intruder tactics and techniques;
- securing CSIRT communications through encryption;
- analyzing incidents to determine how to respond effectively; and
- maintaining incident records and reports.
Nontechnical skills
CSIRT work is service-based. Thus, all CSIRT staff must demonstrate diplomacy and communicate competency in interactions with constituents.
- Willingness to follow instructions. Staff should be familiar with defined CSIRT procedures and policies and the importance of upholding them.
- Communication. Staff should demonstrate effective written and interpersonal communication skills necessary to fulfill duties such as documenting incident reports or presenting technical briefings.
- Collaboration. Due to the cooperative nature of the CSIRT structure, members must be committed team players to ensure collective morale, productivity and agility.
- Time management. Staff should understand how to use provided criteria to prioritize various CSIRT activities and determine when to ask for help from management.
- Analytical reasoning. CSIRT staff need to think out of the box to anticipate attacker techniques and problem-solve in potentially volatile situations.
- Stress management. The demanding nature of incident response and risk of security staff burnout warrant special attention to managing stress, as well as work-life balance.
- Continuous learning. Incident response is a constantly changing area of expertise. Thus, CSIRT members must be inquisitive people and embrace opportunities to further their skills through training, certification or mentorship.
How to manage a CSIRT
It is important to have a dispersed and well-managed CSIRT. Most CSIRTs are structured to maintain 24/7 monitoring. This is done by dividing operating hours into three shifts, each with a designated shift lead. During their shifts, shift leads should communicate their work and findings with other shift leads. This information should then be relayed to the CSIRT team lead or executive staff member to maintain transparency with the rest of the organization.
Larger companies should not only separate employees by time, but also geographic location. Smaller companies may find it more cost-effective to outsource CSIRT processes for after hours.
SOC vs. CSIRT vs. CERT
Organizations may employ one or more of the three main types of incident response teams: CSIRTs, SOCs and CERTs. Sometimes, these terms are used synonymously, though differences do exist, depending on the organization's use of the term(s).
The most unique of the three is the SOC. This dedicated facility monitors and defends technology and hardware and acts as a command-and-control center for an organization, region or country. It protects networks, servers, applications and endpoints. A SOC's responsibilities, however, extend beyond that of just incident response.
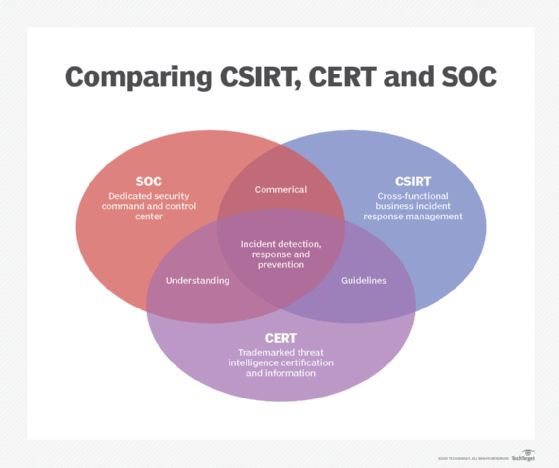
CSIRT, CERT and the less-often-used computer incident response team (CIRT) are often used interchangeably. In general, CSIRTs, CERTs and CIRTs all handle incident response, though their specific tasks may vary by organization. The terminology used by an organization should be adequately defined, along with the goals, structure and use of resources necessary to properly respond to incidents.
It is important to note that CERT is a registered trademark of Carnegie Mellon University (CMU). Organizations may use the CERT mark after achieving authorization. However, some organizations -- likely unaware it is trademarked -- still use it to define their incident response teams.