Six Sigma
What is Six Sigma?
Six Sigma is a business methodology for quality improvement that measures how many defects there are in a current process and seeks to systematically eliminate them.
In 1984, a Motorola engineer named Bill Smith developed the Six Sigma management system to reduce the variations in Motorola's electronic manufacturing processes that were causing product defects.
Since then, the strategies, tools and cultural norms that support the management system have been adopted by upper management and project teams in a wide variety of industries to increase operational excellence.
Additionally, the meaning of the word "defect" has broadened to include any deficiency in business processes that prevents a company from meeting its customer's needs.
How does Six Sigma work?
In statistical analysis, the Greek letter sigma is used to denote a standard deviation from the mean. In the 1920s, statistical process control pioneer Walter Shewhart proposed that in lean manufacturing, three sigma from the mean is the tipping point that indicates there are too many defects and process improvement is required.
This was the accepted norm for many years until Bill Smith proposed gathering and analyzing data at a more granular level and making six sigma the point at which a process has to be corrected.
Because it is almost impossible to achieve zero defects -- a concept known as infinity sigma -- six sigma allows for 3.4 defects per million opportunities for a defect to occur. In contrast, three sigma allows for 66,807 defects per million opportunities.
Once the necessary data has been gathered, a company that is implementing Six Sigma methodologies uses statistics to create a baseline sigma. The baseline illustrates how close -- or how far -- the company is from achieving six sigma and serves as a measuring stick for assessing future improvement.
What is the importance of Six Sigma?
Six Sigma proponents claim its business strategy benefits include up to 50% process cost reduction, cycle-time improvement, less waste of materials, a better understanding of customer requirements, increased customer satisfaction and value stream, and more reliable products and services.
Motorola holds the federal trademark for Six Sigma, and it is generally acknowledged that Six Sigma can be costly to implement and can take several years before a company begins to see bottom-line results.
In 1995, General Electric CEO Jack Welch's very public endorsement of Six Sigma helped businesses outside of manufacturing understand how Six Sigma methodologies can be used to improve customer satisfaction in any industry.
What are the key principles of Six Sigma?
The key sigma principles are the following:
- Customer focus
- Use data
- Improve continuously
- Involve people
- Be thorough
Six Sigma methodologies
The above principles can be applied with one of two improvement methodologies: Six Sigma DMAIC and Six Sigma DMADV. Each term's name is derived from the major steps in its process, but each has its own use.
- DMAIC (define, measure, analyze, improve, control) is used to correct a process that already exists.
- DMADV (define, measure, analyze, design, validate) is used to create a new process.
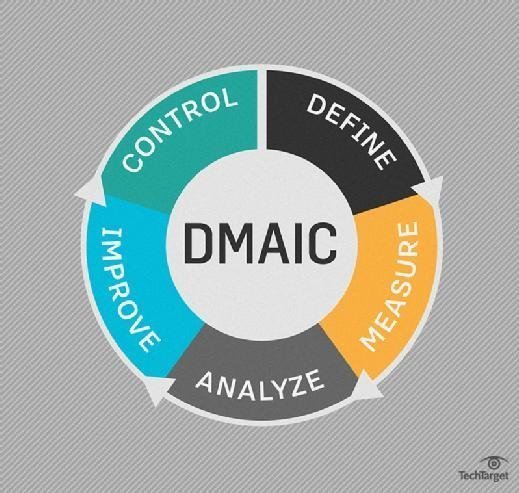
DMAIC
Here is a step-by-step breakdown of Six Sigma DMAIC:
- Define: Identify the project goals and all customer deliverables.
- Measure: Understand current performance.
- Analyze: Determine root causes of any defects.
- Improve: Establish ways to eliminate defects and correct the process.
- Control: Manage future process performance.
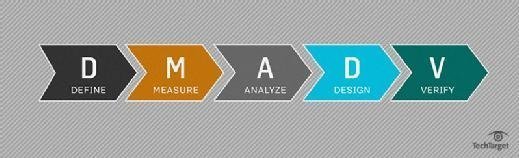
DMADV
Here is a step-by-step breakdown of Six Sigma DMADV. The first three steps of this methodology are identical to DMAIC. Because the two acronyms are so similar, some companies use the acronym DFSS (design for Six Sigma) in place of DMADV.
- Define: Identify the project scope and all customer deliverables.
- Measure: Understand current performance.
- Analyze: Determine root causes of any defects.
- Design: Create a process that meets customer needs and expectations.
- Verify: Ensure process designed meets customer needs and performs adequately.
When contemplating Six Sigma DMAIC versus DMADV, it is important to understand the circumstances in which each should be used.
The DMAIC methodology should be used when an existing product or service is not meeting customer needs or performing to its highest standards.
The DMADV methodology should be used when an organization is developing a new product or service, or when using DMAIC for a current project or process fails.
How to implement Six Sigma
To implement Six Sigma within an organization, the first step is to properly make the case for statistical tools like Six Sigma, and its potential benefits to get stakeholder buy-in.
Additionally, it's important to set the expectation that being entirely defect-free is not realistic. However, there are some best practices that can help to ensure the making of as much improvement as possible.
Once management understands the potential behind Six Sigma, the following eight steps can help to implement a sigma project and ensure a clean rollout.
- Step 1: Motivate stakeholders by highlighting quality losses.
- Step 2: Implement project management and obtain the necessary resources.
- Step 3: Educate team members on the Six Sigma management method.
- Step 4: Create a Quality control chart and identify priorities.
- Step 5: Assign ownership for all team members involved.
- Step 6: Ensure measurement of the right metrics and indicators.
- Step 7: Perform a root cause analysis to understand the defect.
- Step 8: Govern the program to ensure proper implementation and continuous improvement.
Please note that these steps may vary depending on whether you are utilizing Six Sigma or Lean Six Sigma.
What is the difference between Six Sigma vs. Lean Six Sigma?
The purposes of Six Sigma and Lean Six Sigma are different.
The Six Sigma method is focused on limiting fluctuation within business processes and quality management of process output by implementing problem-solving statistical methods.
Conversely, the primary focus of Lean Six Sigma is to eliminate waste and improve existing processes.
Six Sigma certification and resources
All Six Sigma processes are executed by the following:
- Six Sigma White Belts
- Six Sigma Yellow Belts
- Six Sigma Green Belts
- Six Sigma Black Belts
Sigma programs are overseen by a Six Sigma Master Black Belt, per the terms created by Motorola.

The International Association for Six Sigma Certification (IASSC) is one organization that provides a certification program.
At IASSC, yellow, green and black belt exams are designed to measure a person's knowledge of topics contained within IASSC's Universally Accepted Lean Six Sigma Body of Knowledge.
Another sigma training organization offering belts from white to black is 6Sigma.us.







