desktop management interface (DMI)
The desktop management interface (DMI) is a standard industry framework that manages and tracks components on one or more personal computers, usually from a centralized console.
DMI is a standard from the DMTF, formerly the Distributed Management Task Force, an organization that creates open management standards spanning a broad range of types of IT infrastructure, including cloud, virtualization, networks, servers, storage, plus desktops and mobile devices.
Understanding DMI and DASH
At the DMTF, the initial DMI standard was defined in 1998, at which time it earned the description of the first desktop management standard from the DMTF. As a standalone standard, the DMI persisted until March 31, 2005, when it reached its end-of-life status. Since then, DMI has been supplanted by a large collection of DMTF standards known collectively as Desktop and Mobile Architecture for System Hardware, or DASH.
Is DMI still used?
DMI is not still in use. DASH has replaced DMI completely and falls under the working group at DMTF named the System Management Forum (SMF).
Components and specifications of DASH
The baseline DSP0227 standard goes back to 2011 and is entitled WS-Management CIM Binding Specification. The common information model (CIM) is a key aspect of the DMTF approach to management. It defines an open, vendor-neutral structure for CIM to store and access system and network management information.
This article is part of
What is desktop management and how does it work?
The Web Services for Management (WS-Management) Specification applies to how a web-based interface delivers secure and comprehensive access to a management user interface. Thus, DSP0227 describes how WS-Management provides secure, consistent information to manage desktop and mobile hardware devices under the DASH denomination. A second key specification, DSP0232, covers DASH Implementation requirements and is dated January 2022.
There are 39 defined DMTF profiles related to DASH that cover a wide range of system characteristics, including hardware, software, BIOS, networking, remote access, power states, and several other system content and capability aspects.
How does modern desktop management work?
DASH uses the WS-Management specification and the DMTF's CIM to collect, monitor and manage desktop and mobile systems using some or all of the data that the three-dozen-plus DASH-related DMTF profiles cover. DASH covers architectural semantics for desktop and mobile devices. It also uses industry-standard protocols and its profiles to standardize management mobile and desktop system management irrespective of machine state, operating system or other vendor specifics.
DASH allows the same tools, syntax, semantics and interfaces to work across most conceivable types of computing systems. This includes traditional desktops, mobile and laptop PCs, bladed PCs, virtual machines, thin clients, and mobile devices such as smartphones and tablets. The DASH Protocol Stack supports the various layers needed to support management applications through Web Services for Management using standard IP-based protocols and networked communications (Figure 1).
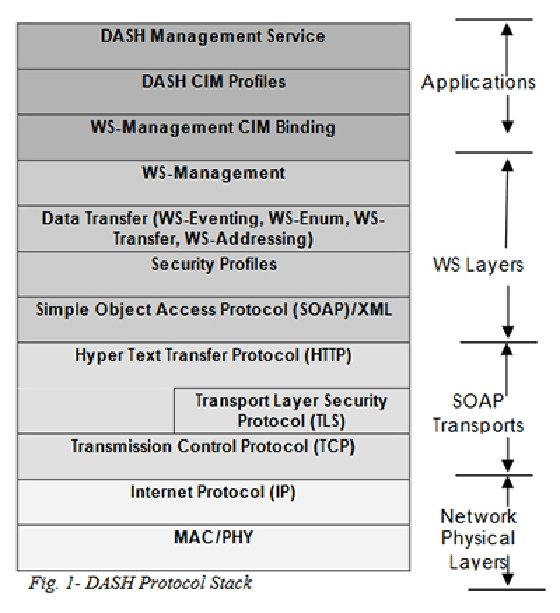
DASH comes into play through a related CIM profile and its DASH Management service, atop a standard collection of Web services and networking layers.
The stack rests on Simple Object Access Protocol (SOAP) messages that ferry XML content between communicating parties. Above that layer, Web Services management provides event handling, enumeration, data transfer and device and service addressing capabilities. This allows DASH to employ industry-standard network and transport layer mechanisms, including encryption, authorization and authentication, and to manage roles, authorization and accounts using standard profiles. Further, DASH provides access control over all its managed resources and operations using role-based access controls such as read-only user, operator and administrator to define different access levels and update and control capability.
DASH profiles
The 39 DMTF profiles defined for DASH provide all the required classes, instances, properties and methods to manage and control desktop and mobile operating systems. DMTF's 2022 DASH implementation 'Requirements Specification' explains how such profiles work in a DASH-compliant management environment. The DASH initiative also defines compliance testing requirements so that developers can ensure their management works properly. With this initiative in place, organizations can check to ensure that systems behave as they should.
DASH also offers a range of advanced capabilities that provide comprehensive end-to-end management. These include the following:
- Power control: access to information about system power and sleep states and the ability to interrogate and manage power plans.
- Boot control: the ability to remotely interrogate and restart desktop and mobile systems, including tools to manage BIOS and UEFI, firmware and set-up configuration activities that precede operating system startup.
- Detailed hardware information: including chassis and component model and serial number data, CPU, memory, fan, power supply and complete sensor suites.
All these advanced capabilities come with defined DMTF profiles. The SMF working group constantly maintains these profiles. In addition, DASH also supports a set of standard event message content in the DMTF Message Registry Schema -- part of the CIM. This permits broader interoperability among different implementations of management instrumentation and the software that subscribes to and receives event-related messages and data.
Who supports DASH?
The major hardware vendors support DASH, including AMD and Intel, among many others. Virtually all major management consoles, including Microsoft, and numerous open source environments, including KVM and VNX, SolarWinds, Jira, Citrix, VMware and many more, support DASH or provide DASH plugins for their runtime environments.
