differentiated services (DiffServ or DS)
What is differentiated services (DiffServ or DS)?
Differentiated services (DiffServ or DS) is a class of service (CoS) model to specify and control IP network traffic by class. The goal is to ensure that certain types of traffic that require a relatively uninterrupted flow of data get precedence over other kinds of traffic. One example is voice traffic.
DiffServ is one of the most advanced network solutions for managing network traffic in terms of CoS. It aims to divide traffic into multiple classes and treat them differently. Such classification and differentiation are especially useful when there is a shortage of networking resources. DiffServ operates at Layer 3 -- the network layer -- of the Open Systems Interconnection model.
Unlike earlier mechanisms, such as 802.1p tagging and type of service (ToS), DiffServ avoids simple priority tagging of packets. Instead, it uses more complex policy or rule statements to determine how to forward a given packet. DiffServ and CoS provide a way to control traffic that is both more flexible and scalable than the quality of service (QoS) approach.
In the DiffServ model, for a given set of packet travel rules, a packet is given one of 64 possible forwarding behaviors. These behaviors are known as per-hop behaviors (PHBs). Thus, the primary goal of DiffServ and its differentiated services code point (DSCP), or DiffServ code point, is to determine the PHB that defines the packet forwarding procedure of each node.
DiffServ code point
The DSCP is a six-bit field in the IP header. It is a part of the eight-bit ToS field inside the IP header and specifies the PHB for a given flow of packets.
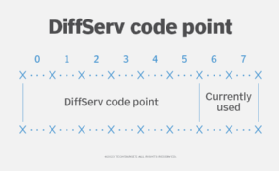
The DSCP value can range from 0 to 63. The field is used to mark a packet to ensure that each device in the network handles it correctly without having to individually evaluate packet contents for each packet. Once a packet is marked, it can be treated differently from other packets based on admin-defined QoS policies. Consequently, a particular packet can be queued, another can be dropped, etc.
In the IP header, the DSCP field is superseded by the IP precedence value and the ToS field. Like DSCP, these fields are also used to mark traffic to influence PHB in the network.
Per-hop behavior in DiffServ
In a network, the forwarding treatment of a packet is determined by DSCP. PHB defines each node's packet forwarding treatment. When the PHB is defined by the DiffServ protocol, the traffic classes can be grouped in different ways, including the following:
- Expedited Forwarding (EF) group. Traffic with specific QoS requirements.
- Assured Forwarding (AF) group. Composed of traffic classes AF1, AF2, AF3 and AF4, each with its associated value -- AF1 is given the highest priority and then dropped to the lowest priority class when switching networks.
- Best Effort (BE) group. QoS levels not assured and the network not sensitive to metrics like latency and packet loss.
DSCP of value 000000 denotes that the packets receive BE treatment. AF PHBs are intended for better than BE services, like virtual private networks. EF PHBs are meant for real-time services that typically have well-defined and stringent requirements for latency, packet loss, jitter, etc.
DiffServ defines the DS fields and PHBs. However, it is the responsibility of the edge routers (ERs) to classify, police and shape packets; specify these rules in the service-level agreement (SLA); and decide how many classes of service to provide. If more than one domain is involved, there may be an SLA between them, which determines if the DS field of a packet is re-marked.
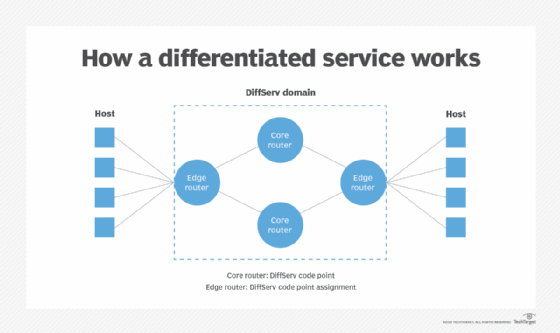
DiffServ domain
The scope of the DiffServ protocol is identified by the DiffServ domain. This domain is composed of two types of nodes. The first is edge routers, which are located at the borders of the domain. ERs execute several important functions:
- Assign the DSCP value to each packet as per the QoS information provided by the incoming network.
- Horizontally map the DiffServ and the QoS protocol inside the incoming domain.
- Assign the same DSCP values to all traffic flows with similar QoS requirements.
Apart from ERs, the DiffServ domain also includes core routers (CR). Unlike ERs, CRs are located inside the domain, and their role is to forward the packets with different policies as per their DSCP values, while ensuring that flows with the same DSCP value are treated the same inside the domain.
Advantages and disadvantages of DiffServ
The DiffServ architecture is useful where there is a need to provide prioritized service mechanisms without requiring routers to maintain connection-level information. Services are prioritized by marking IP packets with DSCPs located in the IP header. Routers along the way prioritize packet processing and forwarding based on the DSCP value for different types of services.
Another advantage of DiffServ is that, unlike Resource Reservation Protocol (RSVP), it does not have to maintain a soft state. Therefore, it does not have to periodically refresh each reserved node to recover from errors or to automatically adapt to network changes. This enables DSCP to avoid the connection-level scalability issue that is common with RSVP.
DiffServ is also scalable because resources are allocated in the granularity of class, and the amount of state information is proportional to the number of classes, not the number of flows. Additionally, DiffServ can simplify network operations because sophisticated operations -- classification, marking, policing and shaping -- are only needed at the network's edge.
One disadvantage of DiffServ is that it does not provide performance guarantee. Also, it is usually effective only when the amount of high-priority traffic, e.g., voice or other real-time services, is small. Finally, in some cases, end users may not be able to perceive the performance difference, say, from BE to AF or EF.
