direct inward dialing (DID)
What is direct inward dialing (DID)?
Direct inward dialing (DID) is a method organizations use to route incoming calls to specific private branch exchange (PBX) systems without an operator.
Organizations purchase DID numbers from a telephone company or service provider and assign them to individual extensions within the organization. When callers dial a DID number, they are automatically connected to the extension that is associated with that number.
DID numbers can route calls to any type of phone, including voice-over-IP (VoIP) phones, mobile phones and landlines. They are often used with call forwarding services so that calls can be routed to the person or department even if they are not in the office.
What are the benefits of using a direct inward dialing system?
Using DID, a company can offer its customers individual phone numbers for each person or workstation within the company without requiring a physical line into the PBX for each connection.
This helps reduce the number of missed calls and can make it easier for callers to reach the person or department they need. DID numbers can also help save time by eliminating the need for operators to route calls.
DID numbers can give organizations a more professional image, and they can create a local presence in multiple markets. For example, a company might rent 100 phone numbers from the phone company that could be called over eight physical telephone lines, called trunk lines. This would allow up to eight ongoing calls at a time.
Compared with regular PBX service, DID saves the cost of a switchboard operator, calls go through faster, and callers feel they are calling a person rather than a company.
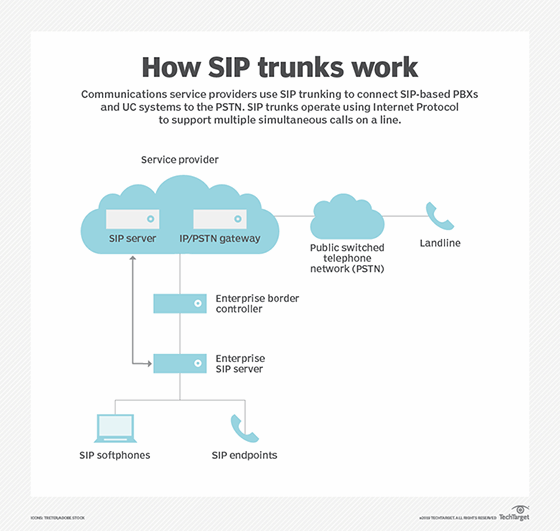
What are some use cases for direct inward dialing systems?
There are many ways direct inward dialing can be used, and organizations often customize the system to meet their specific needs. Some common examples include the following:
- Call forwarding. DID numbers can be set up to forward calls to any phone number, including mobile phones and VoIP phones. This is often used for after-hours call coverage or when employees are out of the office.
- Call center queues. Incoming calls can be routed to a call center queue so that they can be answered by the next available agent.
- Voicemail. Calls can be forwarded to voicemail so that callers can leave messages for individual employees or departments.
- Fax machines. Fax machines can be assigned DID numbers so that incoming faxes can be routed to the correct machine.
What is the difference between direct inward dialing and direct outward dialing?
DID allows customers to call a specific extension within an organization, while direct outward dialing (DOD) allows employees to make calls to phone numbers outside of the organization.
Both systems use unique phone numbers, but the major difference is that DID numbers are used to route incoming calls, while DOD numbers are used to route outgoing calls.
While DID is typically used by businesses, DOD is more often used by residential customers. This is because most businesses have PBX systems that can route calls internally with no direct outward dialing.
However, some businesses still use DOD so that employees can make calls from their desk phones without going through the PBX system.
See also: What are the benefits of centralized SIP trunking?
