Eisenhower Matrix
The Eisenhower Matrix is a time management tool for prioritizing tasks. It is also known as the Urgent/Important Matrix, Time Management Matrix and the Eisenhower Method.
The Eisenhower Matrix gets its name from the 34th president of the United States, Dwight D. Eisenhower, who was quoted saying, "I have two kinds of problems, the urgent and the important. The urgent are not important, and the important are never urgent." This method was popularized by Stephen Covey's book The 7 Habits of Highly Effective People.
According to a consumer research study titled "The Mere Urgency Effect," people naturally choose urgency over importance by prioritizing tasks that are time-sensitive and less important, over tasks that are less urgent but offer greater rewards. The Eisenhower Matrix is used to overcome this common bias, as it factors in the importance of a task along with its urgency.
Urgency versus importance
Properly identifying the level of urgency and importance each task holds is critical to using the Eisenhower Matrix.
Urgent tasks demand immediate attention and carry clear consequences for not satisfying or completing them on time.
Important tasks contribute to longer-term objectives and goals that sometimes require planning in order to complete.
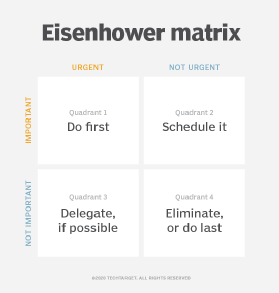
How does the Eisenhower Matrix work?
The matrix is divided into four quadrants. Users consider the urgency and importance of their individual activities, and sort them into the appropriate quadrants. Each quadrant has a specific call to action -- do, schedule, delegate or eliminate. Each quadrant has its own priority level: Quadrant 1 tasks should be done first, while Quadrant 4 tasks should be done last or eliminated.
Quadrant 1: "Do first." These tasks are both urgent and important, demanding immediate attention and action. Quadrant 1 activities are the highest priority group with clear deadlines, and carry consequences for poor work quality or not meeting the deadline.
Quadrant 1 tasks might include:
- Solving a company-wide IT outage.
- Preparing a presentation or report for an important meeting.
Quadrant 2: "Schedule it." These tasks are important, but not urgent. They may or may not have defined deadlines, but are still critical for long-term goals. Proactive management of activities in this quadrant can help lighten the load of Q1 tasks. Q2 activities should have the second highest priority after Q1 activities.
Quadrant 2 tasks might include:
- Attending professional networking events or conferences.
- Completing employee performance reviews.
Quadrant 3: "Delegate, if possible." These tasks are urgent, but not important. Though there is a level of time sensitivity, the tasks don't contribute significantly to long-term goals. This is where the ability to distinguish between urgency and importance comes into play. Typically perceived as "busy work," tasks that fall into this quadrant can be delegated without significant issue. Q3 activities have the third highest priority.
Quadrant 3 tasks might include:
- Attending noncritical meetings.
- Finishing menial paperwork.
- Completing administrative tasks.
Quadrant 4: "Eliminate, or do last." These tasks are neither urgent, nor important. Tasks in this quadrant are not necessary, and do not contribute to long-term goals or interests. It is recommended to either do these activities last or eliminate them altogether, and they constitute the lowest priority group.
Quadrant 4 activities might include:
- Sorting through spam emails.
- Scrolling through LinkedIn.
- Organizing files.
Limitations of its use
The Eisenhower Matrix is a simple way to prioritize tasks based on importance and urgency. While its simplicity makes it easy to use, it ignores other important considerations -- such as availability of resources, task complexity and effort levels.
Furthermore, the Eisenhower Matrix works best when there are relatively few tasks per quadrant. A higher number of tasks can overwhelm users and require further prioritization activities within each quadrant. With a high volume of tasks, filling out the matrix can also become time-consuming and a lower priority task of its own.
As this approach was designed for users in management positions, it can have limited benefits to users who can't delegate tasks or independently structure their daily activities. Without the option to delegate, there is less distinction between urgent/important and urgent/not important tasks. If users are not in charge of their own schedules, they will not be able to prioritize the order of their tasks, and will likely spend the majority of their time executing someone else's Q3 tasks.
Relation to the Pareto Principle
The Pareto Principle, or the 80/20 rule, is a theory stating that 20 percent of efforts determine 80 percent of outcomes. According to this theory, 20 percent of a company's employees produce approximately 80 percent of the company's results -- or perhaps 20 percent of a company's investments produce about 80 percent of its profits.
Applied within the context of personal productivity, the rule states that about 20 percent of an employee's work will yield 80 percent of the employee's impact. The purpose of the Eisenhower Matrix is to help users identify the most impactful 20 percent of tasks to focus on, and avoid wasting time on the less impactful 80 percent.
While the Eisenhower Matrix does not identify the exact 20 percent of work to focus on, it can provide a general insight into which tasks might yield larger results than others and are beneficial to prioritize.
