Fibonacci sequence
What is the Fibonacci sequence?
The Fibonacci sequence is a set of integers (the Fibonacci numbers) that starts with a zero, followed by a one, then by another one, and then by a series of steadily increasing numbers. The sequence follows the rule that each number is equal to the sum of the preceding two numbers.
The Fibonacci sequence begins with the following 14 integers:
0, 1, 1, 2, 3, 5, 8, 13, 21, 34, 55, 89, 144, 233 ...
Each number, starting with the third, adheres to the prescribed formula. For example, the seventh number, 8, is preceded by 3 and 5, which add up to 8.
The sequence can theoretically continue to infinity, using the same formula for each new number. Some resources show the Fibonacci sequence starting with a one instead of a zero, but this is fairly uncommon.
Calculating the Fibonacci sequence
The Fibonacci sequence can be calculated mathematically. In this approach, each number in the sequence is considered a term, which is represented by the expression Fn. The n reflects the number's position in the sequence, starting with zero. For example, the sixth term is referred to as F5, and the seventh term is referred to as F6.
Using this numbering, the Fibonacci sequence can be defined by the following three equations:
- F0 = 0 (applies only to the first integer)
- F1 = 1 (applies only to the second integer)
- Fn = Fn-1 + Fn-2 (applies to all other integers)
The first two equations are essentially stating that the term in the first position equals 0 and the term in the second position equals 1. The third equation is a recursive formula, which means that each number of the sequence is defined by using the preceding numbers. For example, to define the fifth number (F4), the terms F2 and F3 must already be defined. These two numbers, in turn, require that the numbers preceding them are already defined. The numbers continuously build on each other throughout the sequence.
The following table shows the position of each term, along with its Fn value and Fibonacci number, starting with the first term and ending with the 14th.
| Term position |
Fn value |
Fibonacci number |
| 1st |
F0 |
0 |
| 2nd |
F1 |
1 |
| 3rd |
F2 |
1 |
| 4th |
F3 |
2 |
| 5th |
F4 |
3 |
| 6th |
F5 |
5 |
| 7th |
F6 |
8 |
| 8th |
F7 |
13 |
| 9th |
F8 |
21 |
| 10th |
F9 |
34 |
| 11th |
F10 |
55 |
| 12th |
F11 |
89 |
| 13th |
F12 |
144 |
| 14th |
F13 |
233 |
You can try out the formula for yourself, using the table to find the sequence numbers preceding the target term value. For example, the following calculation finds the Fibonacci number for the term in the tenth position (F9):
F9 = F9-1 + F9-2 = F8 + F7 = 21 + 13 = 34
The challenge with a recursive formula is that it always relies on knowing the previous Fibonacci numbers in order to calculate a specific number in the sequence. For example, you can't calculate the value of the 100th term without knowing the 98th and 99th terms, which requires that you know all the terms before them. There are other equations that can be used, however, such as Binet's formula, a closed-form expression for finding Fibonacci sequence numbers. Another option it to program the logic of the recursive formula into application code such as Java, Python or PHP and then let the processor do the work for you.
History of the Fibonacci sequence
The Fibonacci sequence is named for Leonardo Pisano (also known Fibonacci), an Italian mathematician who lived from 1170 to 1250. Fibonacci considered the sequence to be an answer to the following question:
"How many pairs of rabbits will be produced in a year, beginning with a single pair, if in every month each pair bears a new pair which becomes productive from the second month on?" The result can be expressed numerically as 1, 1, 2, 3, 5, 8, 13, 21, 34 ...
A Sanskrit grammarian, Pingala, is credited with the first mention of the sequence of numbers, sometime between the fifth century B.C. and the second or third century A.D. Since Fibonacci introduced the series to Western civilization, it has had a high profile from time to time. In The Da Vinci Code, for example, the Fibonacci sequence is part of an important clue. Another application, the Fibonacci poem, is a verse in which the progression of syllable numbers per line follows Fibonacci's pattern.
Fibonacci numbers can also be used to define a spiral and are of interest to biologists and physicists because they are frequently observed in various natural objects and phenomena. The branching patterns in trees and leaves, for example, and the distribution of seeds in a raspberry reflect the Fibonacci sequence.
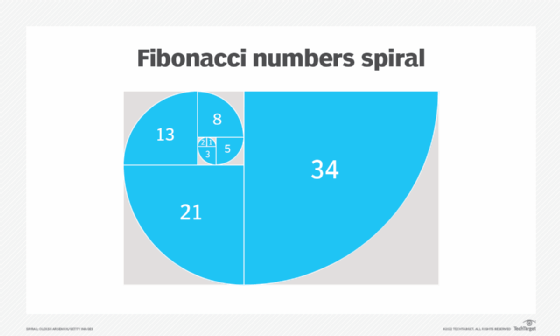
The Fibonacci sequence is often associated with the golden ratio, a proportion (roughly 1:1.6) that occurs frequently throughout the natural world and is applied across many areas of human endeavor. Both the Fibonacci sequence and the golden ratio are used to guide design for architecture, websites and user interfaces, among other things.
See also: glossary of mathematical terms and algorithms, mathematical symbols.
