Gmail
What is Gmail?
Gmail (pronounced Gee-mail) is a free web-based email service that provides users with 15 GB of storage for messages and the ability to search for specific messages.
The Gmail program also automatically organizes successively related messages into a conversational thread.
Gmail, otherwise known as Google Mail, can be accessed from a personal computer, tablet or any Android or iOS device.
According to Google co-founder and CEO Larry Page, the company was inspired to create Gmail because of a user's letter complaining about problems with existing email services, like Yahoo Mail and Microsoft Outlook.live.com (previously known as Hotmail).
Their complaints included the constant need to delete messages to stay within storage limits and the lack of searchability.

What are Gmail's features?
Gmail's interface is minimalistic and uncluttered. Gmail incorporates a search bar for users to find specific emails and messages can be filtered using tabs that automatically sort emails into categories.
Gmail also offers users the ability to chat with other Gmail users in real time, as well as make video calls. Gmail's storage capacity, at 15 GB, is considerably larger than most other free email services.
Gmail has several features not commonly found in other email services.
For example, Gmail allows users to archive messages instead of deleting them, and Gmail's search function is powerful enough to find specific messages even if a user can't remember the sender, recipient or subject line.
Gmail also offers a Priority Inbox feature that highlights important messages for the user and spam filtering to weed out spam and unsolicited or malicious emails.
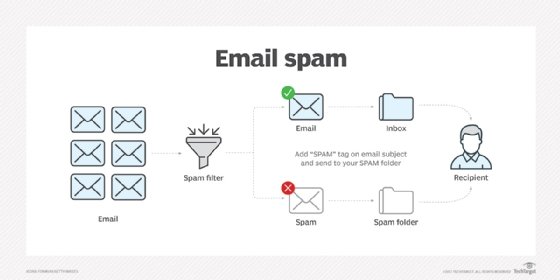
What are Gmail's security features?
Gmail's email system uses secure sockets layer (SSL) encryption when retrieving and sending emails, which means that email messages are less likely to be intercepted by a third party.
However, users must be careful to avoid phishing scams, which are email messages that appear to be from Gmail but are actually from a third party trying to gain access to a user's account.
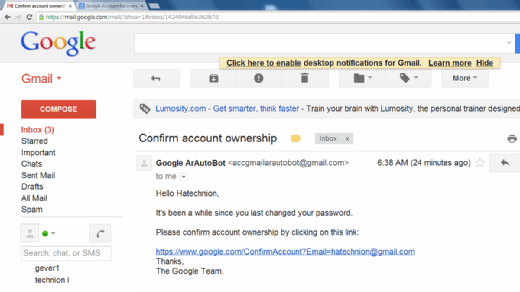
To avoid falling for a phishing scam, Gmail users should only log in to their Gmail account by going to the Gmail website and entering their username and password into the proper fields.
They should never click on a link in an email that purports to be from Gmail but goes to a different website, as these sites often have malware that can infect their PC or reveal their personal data to cybercriminals.
As an added form of protection, Gmail offers two-factor authentication, which requires users to enter not only their password but also a code that is sent to their phone when they try to log in.
This makes it more difficult for someone to gain access to a Gmail account because they would need to know the password and have access to the user's phone.
How to create a Gmail account
To use Gmail, you will need to create a Google account, which is simple and only takes a few minutes. To create a Google account, go to the Gmail website and click on the Create an account link.
- Enter your name, choose a username for your email account and set a password.
- You'll also need to enter a date of birth and gender.
- Once you've entered all the required information, click on the Next Step button.
- You'll then be asked to verify your phone number by entering a verification code that will be sent to your phone via text message or voice call.
Once you've verified your phone number, you'll be able to write a new email.
Using Gmail also grants you access to Google's other free-to-use productivity tools, such as the following:
- Google Chrome. A fast, free web browser powered by Google.
- Google Calendar. A calendar application that can be used to schedule events and track appointments.
- Google Docs. A word processing application that allows users to create and edit documents online.
- Google Sheets. A spreadsheet application that lets users create and edit spreadsheets online.
- Google Slides. A presentation application that allows users to create and edit presentations online.
- Google Hangouts. A messaging application that lets Gmail users chat with each other in real time.
- Google Meet. A video conferencing application that lets Gmail users chat with each other via video call.
- Google Drive. A cloud storage service that gives users access to their files from any device with an internet connection.

Additional apps include Google Play, Google News, Google Meet, Google Chat, Google Contact, Google Translate and Google Photos.
Access these applications by clicking on the Google apps icon in the upper right-hand corner of Gmail just to the left of your account profile picture. These should not be confused with Google Workspace (formerly G Suite), however, which is a suite of paid services that delivers productivity applications and collaboration tools plus cloud storage to businesses.
Compare Microsoft 365 vs. Google Workspace, learn about the Inbox Zero approach to email management, explore the role of mobile email management in the enterprise and delve into the world of email viruses and how protect against them.
