Hick's law
Hick's law is a psychological principle which states that the more options are available to a person, the longer it will take for him or her to make a decision about which option is best. Hick's law is also sometimes referred to as the Hick-Hyman law.
Named for psychologists William Edmund Hick and Ray Hyman, the law provides a logarithmic function which models the reaction time (RT) required to make a decision:
RT = a + b log2(n)
In this function, n is the number of choices while a and b are constants which depend on the circumstances of the decision being made.
Hick's law only applies to situations in which decisions are simple or based on quick reactions. For example, one experiment showed that customers were more likely to purchase jars of jam when there were six flavors displayed than when there were 24 flavors, because making the difficult decision when there were too many flavors deterred potential buyers. Conversely, a decision which requires more thought or research will not be affected, such as choosing a restaurant to eat at or a multiple-choice question on a test.
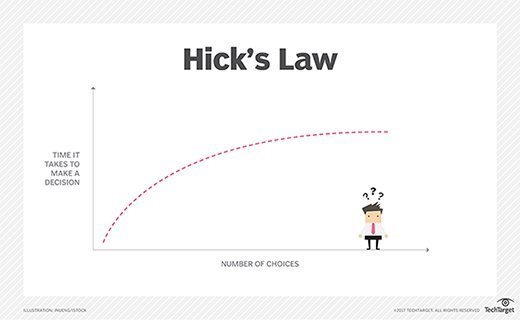
Hick's law is often utilized in user experience design. Designers often use the "Keep it Simple, Stupid" principle to avoid overwhelming potential users or website visitors. This is especially important for websites when planning navigation menus. Having too many links makes it difficult to find the category that the user is looking for, and discourages them from staying on the website.
One way of avoiding this issue, if having many options is necessary for the purpose of the website, is categorizing options. Grouping them together cuts down on the items in the list, making it much easier for the user to find what they are looking for and make a decision faster.
