Hofstadter's law
What is Hofstadter's law?
Hofstadter's law states that a project always takes longer than expected, even when the law is taken into account. Simply put, time estimates for how long a project will take to complete always fall short of the actual time required to complete it.
The law holds true even when the time allotment is increased to compensate for the human tendency toward underestimation. In other words, the law still proves true even when you factor in the possibility that you may need more time to complete the project.
Hofstadter's law is frequently evoked in the context of IT and software development. It is particularly relevant to time management, productivity, project management and DevOps.
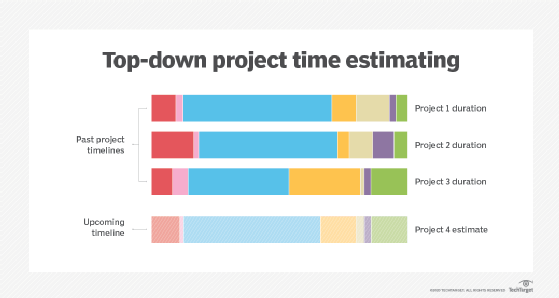
Hofstadter's law refers to a type of planning fallacy. It is the observation that we tend to underestimate the time that is required to complete any given task. This is why project time estimates fail so often, even if the project itself is well managed and well controlled. It's also why actual time durations are always longer than the worst estimates, even estimates that account for extra time by taking Hofstadter's law into consideration.
The law is frequently cited among software development teams, particularly during discussions about project planning, time management and team member productivity. Hofstadter's law always rings true in these contexts, especially if the project is complex or time-consuming. This is because complex projects usually include more steps, which means there are more possibilities for delays and setbacks. In such cases, some teams believe at the outset that the project will be delayed or go over budget, so there's no point in creating a schedule or sticking to it.
Real-life examples of Hofstadter's law
In addition to software development, Hofstadter's law has also been observed in several real-world settings. For example, the Sydney Opera House was completed 10 years later than estimated and cost almost $100 million more than its original estimate of $7 million. Similarly, the Berlin Brandenburg Airport, which was scheduled to open in 2011, actually opened in 2020, overshooting its original budget of 2.83 billion euros with a final tab of almost 10 billion euros.
The history and evolution of Hofstadter's law
Douglas Hofstadter is a cognitive scientist and author. He introduced the eponymous law in 1979 in his book, Gödel, Escher, Bach: An Eternal Golden Braid. The book broke new ground in the then-latent fields of intelligence theory and symbolic systems, earning a 1980 Pulitzer Prize for Hofstadter.
In the book, Hofstadter discusses chess-playing computers. Since the 1960s, there were numerous claims that computers would beat humans at chess within the "next 10 years," but decades after the prediction was first made, humans were still beating the machines.
It wasn't until 1997 that IBM's Deep Blue computer beat the then-reigning world champion Garry Kasparov. In Hofstadter's 1979 book, he wrote that the day a computer would become a chess world champion was still more than 10 years away. He also said that the inability of machines to triumph over humans was "just one more piece of evidence for the rather recursive Hofstadter's law."
Hofstadter's law is recursive in nature because it calls itself by reference. It also implies that it is not only difficult to estimate a project, but potentially infinitely difficult.
Hofstadter's law and optimism bias
Optimism bias -- also known as the illusion of invulnerability -- is the mistaken human tendency to believe that we are less likely to experience negative events and more likely to experience positive events, even though reality may suggest otherwise. This tendency to underestimate the negative and overestimate the positive is clearly reflected in Hofstadter's law.
Hofstadter's law illustrates one element of optimism bias, which is why it often leads teams to underestimate the time required to complete a project. They may also overestimate the benefits of a proposed system and underestimate its drawbacks.
Hofstadter's law is also closely related to the "ninety-ninety rule" in computer programming that was first proposed by Tom Cargill of Bell Labs in the mid-1980s. The rule states that the first 90% of the code accounts for the first 90% of the development time. The remaining 10% accounts for the remaining 90%.
Obviously, this so-called rule is both mathematically and logically flawed. However, it does spotlight a well-known reality in programming that also ties into Hofstadter's law: It's hard to finish a software development project on schedule. In other words, the estimated project time and actual project time almost never match in the real world.
Strategies to beat Hofstadter's law
As every developer and project manager knows, it's impossible to beat Hofstadter's law. Delays and budget overruns are a common and unavoidable problem in every software project, regardless of how carefully a program evaluation and review technique, or PERT, chart was developed. However, it is possible to minimize delays and prevent project costs and schedules from spiraling out of control.
Value stream management -- sometimes known as value stream mapping (VSM) -- is one effective strategy to control project timelines and prevent too many delays. VSM involves breaking down each step in the software development lifecycle (SDLC) into individual components.
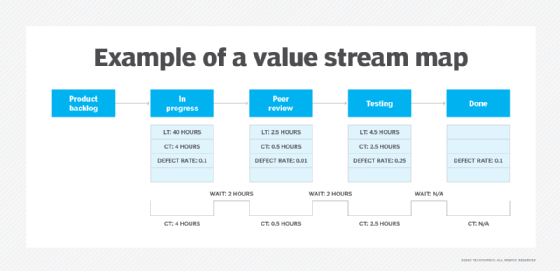
The goal is to make complex processes more visible and provide a more detailed view of the SDLC so software teams can better manage the project and align it with business objectives. VSM also enables them to focus on what works and find ways to fix what doesn't.
See how to deliver software with an SDLC iterative model, learn project management tools and strategies and explore how value stream mapping cuts delay and boosts efficiency.