Hotspot 2.0
What is Hotspot 2.0?
Hotspot 2.0, also known as Wi-Fi Certified Passpoint, is a standard for public-access Wi-Fi that enables seamless roaming among Wi-Fi networks and between Wi-Fi and cellular networks. The Wi-Fi Alliance and the Wireless Broadband Association developed Hotspot 2.0 to enable the seamless handoff of traffic without requiring additional user sign-on and authentication.
Hotspot 2.0 is based on the IEEE 802.11u standard, which is a set of protocols published in February 2011 that allows cellular-like roaming behavior for mobile devices as well as increased Wi-Fi bandwidth and service on demand for wireless-equipped devices.
If the device supports 802.11u and is currently subscribed to a Hotspot 2.0 service from a service provider, it automatically connects to an available Hotspot 2.0 network and roams like how a cellphone moves seamlessly between cell towers, offering service coverage throughout a given area. The steps involved in wireless network discovery, registration, provisioning and access are automated so that little or no manual configuration is needed to connect and stay connected to the Wi-Fi network.
How does Hotspot 2.0 work?
A typical hotspot is a wireless local area network node that provides internet connectivity and virtual private network access from a single location for users of devices with wireless connectivity. Hotspots are common in hotels, airports, libraries and coffee shops. Normally a user must connect manually to a hotspot by checking their wireless connection options, selecting one and entering authentication information (usually a simple password). The physical connectivity zone is determined by the range of the wireless access devices owned by the establishment. In most cases, the radius is about 100 to 200 meters.
Hotspot 2.0 is an evolutionary step in wireless networking designed to help users overcome some annoyances of traditional wireless hotspots. The keys to Hotspot 2.0 are roaming and automation services. Roaming lets wireless mobile devices connect automatically to the nearest Hotspot 2.0 whenever the device is in range. Automation establishes the wireless connection automatically without deliberate user selection or other actions. Hotspot 2.0 emphasizes the meaningful organization of wireless hotspots throughout buildings, campuses, metropolitan areas and beyond.
As a user moves beyond the range of one wireless hotspot and into the range of another, the wireless connection is transferred to the better point of connection, letting the user roam and receive services throughout a much larger physical area than a single traditional wireless access point (AP) could provide. This is fundamentally the same way that cellular service operates, and the wireless roaming and handoff process can continue if there's service coverage -- a hotspot is available -- from a provider.
Hotspot 2.0 requires the following elements to function properly:
- A device that supports IEEE 802.11u for Passpoint internetworking.
- The device must be within a Hotspot 2.0 service area.
- The wireless APs within the Hotspot 2.0 service area must be enabled and configured for Hotspot 2.0, which service providers must ensure.
- The user must have a valid subscription or authentication for the greater Hotspot 2.0 service.
Key features of Hotspot 2.0
Some of the most notable features of Hotspot 2.0 include the following:
- Wi-Fi roaming. Whereas a typical Wi-Fi network is constrained to a small singular range of less than 200 meters from an access point, a Hotspot 2.0 implementation supports secure and seamless roaming between networks without disruptions or reconnecting to different wireless networks.
- Automated connectivity. The addition of Wi-Fi Certified Passpoint lets roaming devices automatically discover and connect to other Passpoint-enabled networks without requiring deliberate connections to each network from the user as they roam.
- Better security. Whereas common Wi-Fi uses Wi-Fi Protected Access (WPA) personal security protocols for home networks, Hotspot 2.0 uses WPA2 security for enterprise-class prevention of advanced attacks, such as eavesdropping, rogue access points and man-in-the-middle attacks.
- Better traffic handling. Traffic prioritization is a major challenge for most networks. Hotspot 2.0 provides quality-of-service (QoS) features that let providers prioritize selected traffic types and ensure vital applications like voice and video receive adequate bandwidth.
- Better policy control. Modern networks depend on policies as much as traffic management, and Hotspot 2.0 offers policy creation and enforcement that helps manage bandwidth, content and access control so that service providers exercise control over their own networks.
How to use Hotspot 2.0 networks
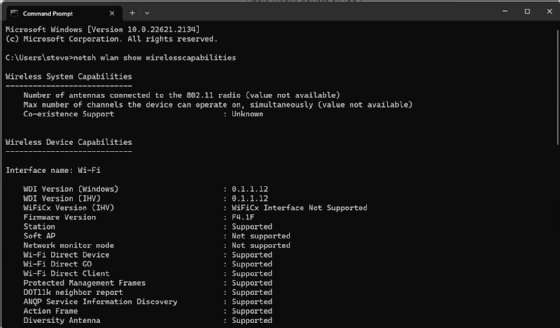
Users and technicians can easily determine whether a Windows 10 or 11 PC supports Hotspot 2.0 by checking for Access Network Query Protocol (ANQP) Service Information Discovery. This is the service needed by Wi-Fi hotspot services such as Passpoint. Support for ANQP services can be found by interrogating the PC's wireless capabilities using the following steps:
- Click Start.
- Select Search and look for Command Prompt.
- Launch the command prompt. Select Run as Administrator, if necessary.
- Type netsh wlan show wirelesscapabilities and press Enter.
The command returns a wealth of details about the computer's wireless features and functionality. Look for the ANQP Service Information Discovery entry, which is the third from the bottom in Figure 1. If the response is "Supported," the device should support Hotspot 2.0.
Similarly, users can determine whether an Android smartphone supports Hotspot 2.0 by opening Advanced Wi-Fi network settings and locating a Hotspot 2.0 entry. If the entry is present -- regardless of whether the feature is enabled or disabled -- the Android device should support the service. Otherwise, the device likely won't support Hotspot 2.0.
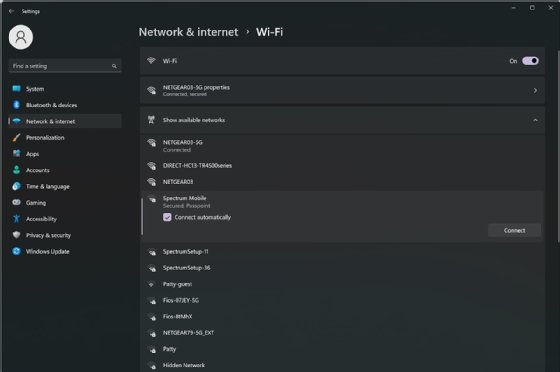
Windows 10 provides a direct way to enable or disable Hotspot 2.0 through the Wi-Fi dialog in the computer's "Settings" app. However, Windows 11 eliminates this direct Hotspot 2.0 control and enables Hotspot 2.0 by default. Users simply select the available Hotspot 2.0-enabled network from the list of available or nearby wireless networks, as shown in Figure 2. Once the user enters their one-time credentials, the computer should be on the Passpoint-enabled network.
The process is similar on Android smart devices. Open the Wi-Fi settings on the device, select the desired Hotspot 2.0 network, and enter one-time credentials. The device should then have access to the Hotspot 2.0 network.
Benefits of Hotspot 2.0
Hotspot 2.0 touts the following benefits for mobile device users:
- Extended service areas. This means more mobility over greater distances. Hotspot 2.0 is designed to facilitate partnerships between Wi-Fi service providers to create extended Wi-Fi coverage areas that can vastly exceed the range of a single wireless AP. This promises greater convenience for mobile device users and more collaboration between service providers.
- Automated connectivity. Busy mobile device users can become confused when selecting from an array of available Wi-Fi networks, as it's almost impossible to know which available connections might be legitimate and which might be malicious. The use of Hotspot 2.0 lets a device connect to known and safe networks wherever they're located.
- Advanced security. Hotspot 2.0 uses WPA2 encryption and, combined with the Passpoint protocols, make a user's wireless connection immune to far more types of attacks than previous Wi-Fi security features.
Disadvantages of Hotspot 2.0
Despite the features and benefits promised in Hotspot 2.0 technology, there are several potential limitations and disadvantages to consider:
- Devices incompatibility. Although Hotspot 2.0 is largely based on existing wireless standards for bandwidth and functionality, devices must support Passpoint behavior to connect to Passpoint-enabled networks. This is the foundation that allows automatic connections and seamless handoffs for roaming. Mobile devices that don't support the Passpoint certification program might not work on those extended wireless networks.
- Unavailable service providers. A successful Hotspot 2.0 program depends on service providers implementing and supporting the technology as well as forming a collaborative extended wireless network. Service providers that forego the technology or avoid the business collaboration needed to build larger networks might limit adoption for users.
- Imperfect security. Even with the addition of WPA2 enterprise security standards in Hotspot 2.0, security isn't impenetrable or flawless. Both users and service providers must understand the vulnerabilities and risks involved in wireless networking, especially in busy public areas.
- Performance. Hotspot 2.0 is designed to offer QoS features capable of enhancing the performance of data traffic such as video. But the addition and configuration of more protocols can potentially reduce performance or capacity for other data types. Service providers are continually searching for better technology and configuration options to enhance performance, so this remains a work in progress.
How does Hotspot 2.0 compare to traditional public Wi-Fi networks?
Hotspot 2.0 isn't a revolution in wireless networking but, rather, an evolutionary step in wireless networking technology that adds protocols to support the roaming and automation capabilities required for larger integrated wireless network architectures. Hotspot 2.0 doesn't make significant changes to Wi-Fi bandwidth or latency, and wireless components that are Hotspot 2.0-compliant should be fully backward compatible with traditional single-network Wi-Fi deployments.
Learn how the internet and Wi-Fi compare and contrast. Distinguishing between the two is important to ensure network administrators can speed up provided support when necessary.
