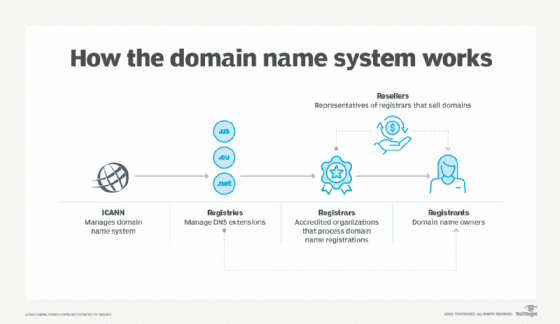
ICANN (Internet Corporation for Assigned Names and Numbers)
What is ICANN?
ICANN (Internet Corporation for Assigned Names and Numbers) is the private, non-government, nonprofit corporation with responsibility for Internet Protocol (IP) address space allocation, protocol parameter assignment, domain name system (DNS) management and root server system management functions. The Internet Assigned Numbers Authority (IANA) previously performed these services.
ICANN is pronounced EYE-can, as in "I can at least try to manage the internet."
What is ICANN's purpose and why is it important?
ICANN is a public-private partnership that is responsible for the following functions related to internet names and numbers:
- Allocation of IP address space. ICANN manages the distribution and allocation of IP version 4 and IP version 6 network addresses through five regional internet registries. These registries allocate IP network addresses and other internet number resources for their regions.
- Top-level domain name system management. ICANN administers the DNS through accredited domain registrars. Registrars are authorized to sell domain names.
- Protocol identifier assignment. ICANN maintains protocol identifiers, including reserved port numbers that internet protocols use and autonomous system numbers associated with global network routes.
- Top level domain management. Generic Top-Level Domain (gTLD) and country code Top-Level Domain name system management.
- Root domain name server system management. ICANN is responsible for maintaining the root domain server system.
These functions are important to maintaining the stability of the global internet and supporting uninterrupted global connectivity. ICANN must balance local, national, regional and international concerns while managing the DNS in a way that is acceptable to the majority of the world's internet users.
The 1998 memorandum of understanding (MoU) between ICANN and the U.S. Department of Commerce governs how ICANN would handle the functions it's responsible for as an independent and international organization.
The MoU spelled out the following guiding principles for ICANN:
- Internet stability. ICANN would manage domain registries, IP addresses and other internet identifiers to ensure a stable networking environment.
- Competition. ICANN would manage DNS in a way that promotes customer choice and competition.
- Bottom-up consensus. ICANN would use consensus-based processes to meet the needs of individual internet users and the internet.
- Representation. ICANN would promote efforts to be representative of all members of the internet community while meeting the needs of those groups.
ICANN registry fees
ICANN collects the following three types of fees from domain registrars:
- Annual accreditation fee. This fee is $4,000 per year for all registrars.
- Variable fees. This quarterly fee represents the shared cost of ICANN providing services to all registrars.
- Transaction-based fees. Every time a domain is added, renewed or transferred, the domain name registrar collects $0.18 to be paid to ICANN.
These fees were established after ICANN was formed as an independent organization and government contracts for providing domain and IP address services expired.
ICANN background and organizational structure
The original members of the ICANN board were chosen by the late Jonathan Postel, who headed IANA. IANA derived its authority under a contract from the U.S. government, which financed the Advanced Research Projects Agency Network from which the internet grew.
The need to globalize the governing of the internet -- among other concerns -- led the U.S. government to recommend the creation of ICANN as a global, independent entity to manage the internet's systems and protocols. The U.S. government essentially turned over control of the internet to ICANN, although domain name registration that Network Solutions performed continued under U.S. government contract for a limited time.
ICANN's board of directors includes 16 voting directors and four non-voting liaisons. Board members are almost all nominated by different ICANN sections and committees; one of the non-voting liaison members is appointed by the Internet Engineering Task Force. The ICANN president and CEO are also on the board.
Criticism of ICANN
Since its beginning, ICANN has had to deal with controversy. Concerns have included areas such as what new generic top-level domains should be permitted and whether alternative root server systems should be allowed.
In its early years, when ICANN was funded through the U.S. Department of Commerce, critics questioned whether such an important function to global connectivity should be controlled by the U.S. government. As it has gained independence, though, critics have pointed to its global importance and argue that ICANN should be more transparent and accountable to the public it serves.
ICANN's accountability model
According to its bylaws, ICANN periodically reviews how well it uses mechanisms for public input, accountability and transparency. It must ensure its actions reflect the concerns of the internet community and are accountable to it.
The ICANN Accountability and Transparency Review is the means by which this accountability model is enforced through ongoing assessments, reporting and process improvements.
ICANN recognizes the following three types of accountability:
- Public sphere accountability. ICANN uses various mechanisms that demonstrate it is behaving responsibly.
- Corporate and legal accountability. ICANN must fulfill its contractual and legal obligations.
- Community accountability. ICANN is expected to act in accordance with the expectations of its community.
ICANN meets its transparency commitments by openly and routinely publishing all documents relating to its operations and activities. Information may be withheld from the public only when there is a clear reason for confidentiality. For example, ICANN does not publish personal information about employees or information related to confidential discussions with governments.
History of ICANN
Some milestones in the history of the ICANN and predecessor organizations include the following:
- 1983. IANA is created as a result of Jon Postel's work administering IP address assignment as a contractor to Defense Advanced Research Projects Agency.
- 1996-97. The Internet Society and IANA creates the International Ad Hoc Committee. Its purpose is to develop a new model for governing top-level domains.
- 1997. U.S. commits to privatizing DNS management.
- 1998. After extensive international discussion and consideration of proposed solutions, ICANN is incorporated as a nonprofit, public-benefit corporation. Soon after, ICANN takes over management of IANA functions.
- 2000. ICANN contracts with U.S. Department of Commerce to perform IANA functions.
- 2000-2002. First expansion of generic top-level domains adds seven new gTLDs.
- 2003-2011. Second round of gTLD expansion adds an additional seven.
- 2012-2017. Third round of gTLD expansion adds over 1,200 new gTLDs.
- 2016. ICANN ends contract with U.S. government.
- 2017. ICANN begins operation following a global multistakeholder model.
Find out how some are reimagining fulfillment of ICANN's functions in the future, for example by using nonfungible tokens to manage domain names.
