Kotlin
What is Kotlin?
Kotlin is a statically typed, object-oriented programming language that is interoperable with the Java virtual machine (JVM), Java Class Libraries and Android.
The Kotlin programming language was originally designed to improve the Java programming language and is often used in conjunction with Java. Despite being the preferred development language of Android, Kotlin's interoperability with Java has led it to be used with many application types.
What is Kotlin used for?
Kotlin is a general-purpose development language used mainly for Android mobile app development. Besides Android apps, Kotlin is also useful for the following:
- Server-side development. Back-end web app development traditionally uses Java. Kotlin can be used alongside Java for development on the server. Kotlin supports Java Class Libraries.
- Full-stack web development. Developers use Kotlin for JavaScript to translate Kotlin lines of code into JavaScript for front-end web development. This approach lets them use the same code on the front and back ends.
- Multiplatform mobile development. Developers use Kotlin for Android and other mobile platforms, including Apple iOS, Apple watchOS and Linux.
- Data science. Kotlin is often used for data science tasks, such as building data pipelines and putting machine learning models into production. Jupyter and Zeppelin, two popular data science tools used with Java, also support Kotlin.
Organizations that create Android applications using Kotlin can also use those skills to manage their cloud-based resources.

Benefits of Kotlin
Some of the advantages of Kotlin are the following:
- Interoperability. Kotlin interoperates with Java because they compile to the same byte code. Kotlin can be compiled into JavaScript or an LLVM encoder, which enables programmers to perform just-in-time compiling to ensure that code embedded in another program runs smoothly. It also shares tooling with Java. These features make it easy to migrate Java applications to Kotlin.
- Safety. Kotlin is designed to help avoid common coding errors that can break code or leave vulnerabilities in it. The language features null safety and eliminating null pointer exception errors.
- Clarity. Kotlin eliminates some of the redundancy in the basic syntax of popular languages like Java. Kotlin is a timesaver for developers because it provides more concise code. Developers can write programs with less boilerplate code, increasing their productivity.
- Tooling support. Kotlin has tooling support from Android with tools optimized for Android development, including Android Studio, Android KTX and Android SDK.
- Community support. Although Kotlin is a relatively new language compared to Java, it has a community of developers who work to improve the language and provide documentation.
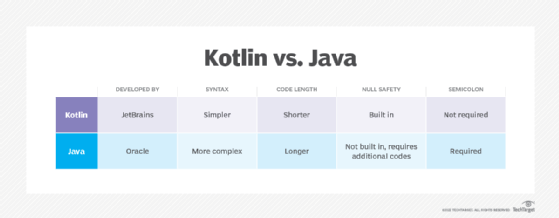
Kotlin vs. Java
Kotlin and Java are both general-purpose, statically typed programming languages. In many ways, Kotlin is considered a replacement for Java. While it is not compatible with syntax, it is interoperable with Java code and libraries. Kotlin also has its own libraries that were created through an application programming interface for Android apps.
In Java, redundancy results in verbose and longer code. Kotlin is simpler, making it easier for beginners to learn. Kotlin focuses on stripped-down, functional code and avoids repetitive boilerplate code. Semicolons at the end of every line are not needed, although Kotlin does not have an issue if a developer uses them. Additional features reduce the complexity and length of code needed to achieve the end goal of a Kotlin team.
An Android developer might choose Java over Kotlin if they are new to Android software development. Historically, most examples of Android documentation are in Java. A new developer combing through these might find it easier to engage with them in Java rather than converting to Kotlin.
Kotlin syntax and code examples
Kotlin has advantages over Java because it uses a less redundant syntax. For example, the following is a Java idiom:
String s = new String();
It becomes the following in Kotlin:
val s = String()
Here, val stands for a variable whose value never changes.
There is less repetition in instantiating variables in Kotlin than there is in Java. In the example above, the phrase String does not need to be repeated in the Kotlin code. The new operator also isn't used because Kotlin automatically infers the data type. Semicolons are optional when coding new lines.
Below are some more Kotlin code examples:
- The following is an example of how to use Kotlin to declare a function and print "Hi" as an output. The fun operator creates a function:
fun main() {
println("Hi")
} - The following code shows how to assign variables using the val operator in Kotlin:
fun main() {In the above example, Kotlin infers the Int type after the initial variable assignment. If the initializer isn't provided, the Int type must be specified as in val c. This example prints the following:
val a: Int = 1 // initial variable assignment
val b = 2 // Kotlin infers 'Int' type
val c: Int //
c = 3 // deferred assignment
println("a = $a, b = $b, c = $c")
}
a = 1, b = 2, c = 3 - The following code depicts a variable being reassigned using the var operator:
var x = 5 // `Int` type inference
x += 1 - The following example lists properties of the class using the class operator in its declaration and calculating the perimeter of a square:
class Square(var height: Double, var length: Double)This prints the following:
{
var p = (height + length) * 2
}
fun main() {
val Square = Square(10.0, 10.0)
println("The perimeter is ${Square.p}")
}
The perimeter is 40.0The first line of the above code, starting with the word class, is known as a data class because its main purpose is to hold data at the top level with no other function. At least one of the datapoints contained must be a parameter.
History of Kotlin
JetBrains, a company headquartered in the Czech Republic, developed Kotlin in St. Petersburg, Russia, with help from Open Source programmers. The first official release of the language was in 2016.
Kotlin was designed to be a better language than Java and interoperable with Java. Its simplicity and interoperability were the incentives to learn Kotlin. The intention was that Java developers and their organizations could gradually transition to the new language without having to worry about incompatibility.
At the Google I/O 2017 conference, Google announced that Kotlin would be the first officially supported program added to Android Studio. That same year, Kotlin 1.2 was released. It included a new feature that enabled sharing code between JavaScript platforms and JVM. In 2019, Google announced that Kotlin was the preferred language of Android developers.
Kotlin 1.7 is the most recent version as of this writing. It was released in June 2022. In it, Kotlin unveiled the new Kotlin/JVM K2 compiler.
Enterprise IT environments that feature Android devices need personnel with a knowledge of Kotlin to perform unified endpoint management. Take a look at this compilation of device management tools and services that help companies manage Android implementations.
