mesh network topology (mesh network)
What is a mesh network?
A mesh network is a network in which devices -- or nodes -- are linked together, branching off other devices or nodes. These networks are set up to efficiently route data between devices and clients. They help organizations provide a consistent connection throughout a physical space.
Mesh network topologies create multiple routes for information to travel among connected nodes. This approach increases the resilience of the network in case of a node or connection failure. Larger mesh networks may include multiple routers, switches and other devices, which operate as nodes. A mesh network can include hundreds of wireless mesh nodes, which allows it to span a large area.
Full mesh vs. partial mesh topology
In a full mesh network topology, each node is connected directly to all the other nodes. In a partial mesh topology, only some nodes connect directly to one another. In some cases, a node must go through another node to reach a third node.
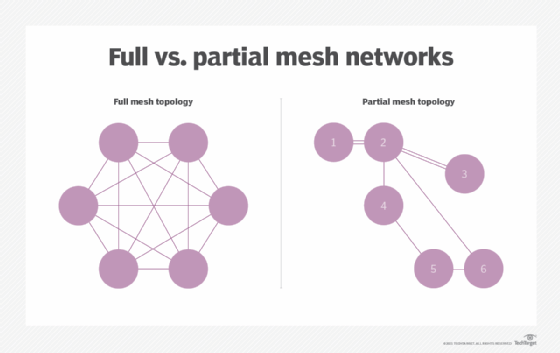
The connections in either a full or partial network can be wired or wireless mesh networks. The decision to use a full or partial mesh depends on factors like the overall traffic pattern of the network and the extent to which nodes or connections are at risk of failure.
Nearly all networks appear to be full mesh networks because everyone on the network can connect with everyone else. This full connectivity is a property of the network protocols, not the topology; any network can appear fully meshed at the logical level if data can be routed between each of its users. Mesh networks are where the difference between logical and physical topologies are most important.
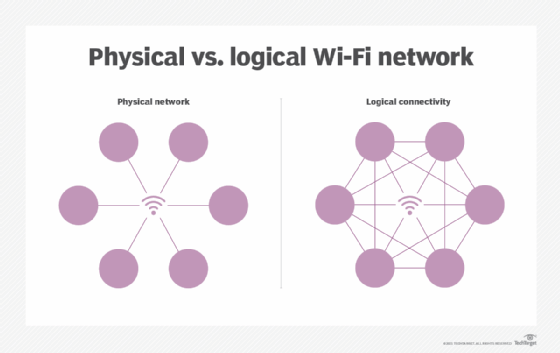
The most common full mesh network is the data center fabric, a local area network (LAN) designed to provide full bandwidth connectivity to each connected device. Wide area networks (WANs) are typically partial mesh networks or tree topologies.
How do mesh networks work?
Nodes in a network are programmed with software that tells the node how to handle information and interact with the network.
Mesh networks use routing or flooding techniques to send messages. In routing, a message hops from node to node to get to its destination. The mesh network must have continuous connections and reconfigure itself if a path is broken, using self-healing algorithms. There will often be more than one path between a source and a destination.
Flooding techniques rely on distributing data from one node to the rest in a network. Data is sent by a subset of the nodes because all nodes may not be available at one time. Each node possesses a subset of the data. A protocol chooses the senders for every data transmission to maximize throughput.
What are the use cases for mesh networks?
Mesh networks can be used in small home networks or large organizations. They are best for larger spaces, however.
Mesh networks enable many devices to share internet connectivity, and for devices to communicate directly without first going through the internet. The utility of a mesh network over other network types, such as a hub and spoke network, is that if a node is too far away from the hub, it can still communicate via a closer node until it reaches a router.
Mesh networks can be used for:
- home monitoring;
- industrial monitoring and control;
- medical monitoring;
- security systems; and
- public service communication.
For example, a monitoring system can have multiple sensor nodes set up in a mesh configuration and spanning a broad area.
What are the benefits of a mesh network?
Mesh networks include the following benefits:
- Increased stability. Single points of failure don't harm the whole network.
- Increased range. Mesh networks can transmit signals over a greater distance. They have fewer dead spots where Wi-Fi signals don't reach.
- Direct communication. Nodes can message each other directly. There is no need for intervention from a central access point.
- Less power is needed for each node. Each device in the network doesn't need to put out a signal strong enough to reach a central access point.
- Better security. If attacked, single nodes are easily replaced.
- Simpler topology. Mesh networks require less infrastructure than other types of networks configurations.
What are the drawbacks of a mesh network?
Mesh networks come with some drawbacks. For example, these include:
- Cost. A single router and Wi-Fi range extenders can make for a more cost-efficient network. Individual nodes also won't cover the same range that a wireless router and range extender would. This means more nodes are needed in a mesh network.
- Scalability. Scaling the size of the network may be more difficult depending on the number of nodes needed.
- Complexity. Each node must send messages and act as a router. The more intricate a mesh network becomes, the more difficult it can be to manage or troubleshoot all the nodes.
- Latency. With lower-power WANs, latency can be an issue because there may not be enough processing capability to handle messaging.
- Power consumption. With a lower-powered node, mesh networks are difficult to deploy.
What is the difference between a mesh network and traditional Wi-Fi?
The biggest difference between Wi-Fi and mesh networks is that with Wi-Fi, a traditional router acts as a centralized access point, while mesh networks are decentralized. Traditional Wi-Fi has single network connections where requests from devices are granted permission to connect to a central router.
All the traffic is funneled through the one access point. Rather than relying on a single access point, mesh networks allow devices to link together to route data between clients.
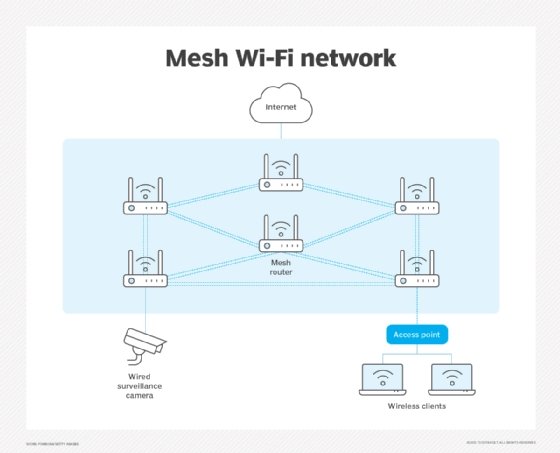
Traditional Wi-Fi is recommended for users on a smaller budget and in smaller spaces. However, if a larger area needs to be covered, and cost is not a factor, then a mesh network is worth considering.
Mesh network vendors and products
Three examples of other mesh network products include the Asus ZenWiFi AX, Google Nest Wifi and the Netgear Orbi AC3000 Tri-Band Mesh WiFi System.
- Asus ZenWiFi AX. A home Wi-Fi 6 mesh router that uses 802.11ax hardware. The system offers a multigig LAN port, USB connectivity and antimalware software.
- Google Nest Wifi. Another home Wi-Fi mesh system that uses 11ac hardware. It features a built-in Google Assistant; however, it does not include antimalware tools or USB ports.
- Netgear Orbi AC3000 Tri-Band Mesh WiFi System. A mesh network option for larger homes and office spaces that has good signal coverage and throughput performance, according to Colocation America, a colocation hosting provider. However, it does not have antimalware tools, USB connectivity or support for WPA3.
Business networks can be set up with mesh networks or other types of networks. Learn more about how to set up a new business network, including how to choose the right architecture and build a network diagram.







