Mini-ITX
What are Mini-ITX motherboards?
Mini-ITX is a compact motherboard configuration designed to support relatively low-cost computers in small spaces such as in automobiles, set-top boxes and network devices. It can also be used to make thin client computers.
The Mini-ITX motherboard configuration was developed by VIA Technologies, a Taiwanese chipset manufacturer, in 2001. It was first demonstrated by its designers in set-top box configurations. The first Mini-ITX motherboard was sold commercially in 2002 to industrial customers.
This compact motherboard measures just 6.7 in. x 6.7 in. (170 mm × 170 mm). Mini-ITX motherboards typically consume less than 100 watts of power, about 5 to 25 watts less than larger architectures.
The ITX in Mini-ITX refers to Information Technology eXtended. The idea behind Mini-ITX was to build computing systems for industrial and consumer use with useful features and a high-speed processor in a compact footprint. Cars, network devices, routers, small robots and set-top boxes are the most common applications of Mini-ITX motherboards.
Components of Mini-ITX motherboards
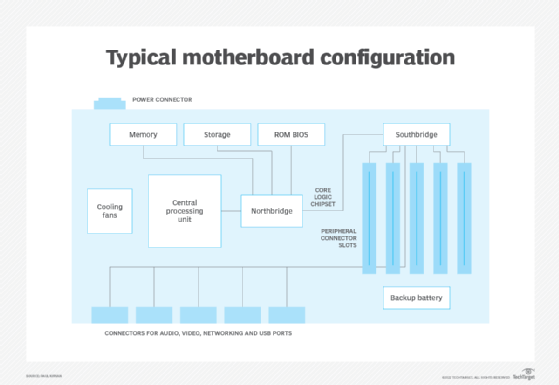
The processor on a Mini-ITX motherboard is soldered to the board and is accompanied by a heat sink. Most Mini-ITX motherboards contain two memory slots, 1 PCI Express (PCIe) or mini-PCI slot, and multiple USB ports. A network port is also standard in these motherboards, along with a power supply, a hard drive, and graphics and sound capabilities. Some Mini-ITX motherboards also include a VGA port and an HDMI port.
A computer built based on a Mini-ITX motherboard is a complete device. It has fairly powerful processing capabilities and its performance is comparable to that of computers with larger motherboards, especially for running everyday applications such as email, web browsing, word processing and playing music and video.
Applications of Mini-ITX motherboards
The Mini-ITX motherboard is suitable for almost every computing or embedded device that operates in a space-constrained environment, including the following:
- Toys.
- Musical instruments.
- Home devices.
- Robots.
- Consumer electronics.
- Self-service kiosks.
- Digital displays.
- Home theater PC systems.
Computers with Mini-ITX motherboards are also suitable for operation in challenging environments, such as industrial or embedded settings. In those environments, high reliability and consistent performance are essential, which Mini-ITX-based systems are capable of delivering. Also, for such applications, most Mini-ITX motherboards are either sold as bulk components or integrated into finished systems.
Mini-ITX vs. micro-ATX and flex-ATX
In addition to the Mini-ITX, the ITX motherboard family includes other small motherboards such as the micro-ATX, nano-ITX and pico-ITX form factors. All of these configurations are much smaller than standard-ATX motherboards, which measure 12 in. x 9.6 in. (305 mm x 244 mm).
The micro-ATX is 9.6 in. x 9.6 in. (244 mm x 244 mm); the nano-ITX and pico-ITX motherboards are 4.72 in. x 4.72 in. (120 mm x 120 mm) and 3.94 in. x 2.83 in. (100 mm x 72 mm), respectively.
The Mini-ITX is backward compatible with micro-ATX and other ATX motherboard variations. This is because the four mounting holes in a Mini-ITX board line up with four of the holes in ATX-specification motherboards. Also, the backplate and expansion slot have the same locations in all these boards, so a micro-ATX case and cases designed for other ATX variants will work with the Mini-ITX board.
Backward-compatibility notwithstanding, the Mini-ITX has several features that set it apart from the other ITX and ATX motherboards. For one, the Mini-ITX is smaller than the micro-ATX. Also, its processors are ultra-low power x86 processors that are soldered to the motherboard and cooled with just a heatsink rather than a heatsink and a fan.
Video and audio capabilities, plus a local area network (LAN) connection are built into the Mini-ITX. In addition to two USB ports, serial and parallel ports, audio input and output ports, the Mini-ITX has a PCI slot that can support two devices with a riser card. It doesn't have a floppy drive interface, but there is a CD-ROM and DVD-ROM interface.
Benefits of a Mini-ITX motherboard
A Mini-ITX motherboard is ideal for computing systems required for space-constrained applications. Its low-power processors deliver high performance while generating very little heat. Off-the-shelf Mini-ITX boards also reduce system cost since they don't require a lot of custom development. At the same time, the board's configuration can be customized thanks to its modular design and onboard pin headers.
Many board and enclosure options are available for Mini-ITX motherboards, including rugged and fanless options. And since the configuration has been around for over two decades, it has an established support and vendor ecosystem to help system developers and organizations.
Mini-ITX products
Mini-ITX motherboards are now available with processors from processor manufacturers, including Intel and AMD. Intel's Mini-ITX motherboards feature either onboard or socketed CPUs. Onboard (or embedded) CPUs draw minimal power and are best-suited for fanless configurations and embedded computing applications. Intel's and Zotac's boards with socketed CPUs have integrated processor graphics, so there's no need for either motherboard graphics or discrete graphics cards.
AMD has also released many socketed Mini-ITX motherboards for its processors, many of which also have integrated motherboard graphics. Some AMD motherboards use mobile CPUs, provide passive cooling and incorporate powerful integrated graphics. These features make them suitable for home theater and media center computers.
Apart from Intel, AMD and Zotac, many manufacturers have also put out Mini-ITX ARM boards. These boards support various operating systems, including Windows CE, Android and Linux. They also come with graphics processors, RAM and baseboard management controllers (BMC).