Nyquist theorem
What is the Nyquist theorem?
The Nyquist theorem is also known as the sampling theorem. It is the principle to accurately reproduce a pure sine wave measurement, or sample, rate, which must be at least twice its frequency. The Nyquist theorem underpins all analog-to-digital conversion and is used in digital audio and video to reduce aliasing. The Nyquist theorem is also known as the Nyquist-Shannon theorem or the Whittaker-Nyquist-Shannon sampling theorem.
The Nyquist theorem is an important component of digital communication. Much of the human experience is analog in nature, such as sound and light waves. Digital electronics can only work in discrete numbers. To convert an analog wave to a digital signal, it must be measured at a regular frequency, which is the sample rate. If the sample rate is too low, it will not accurately express the original signal and will be distorted, or show aliasing effects, when reproduced. If the sample rate is too high, it will needlessly take up extra storage and processing resources. The Nyquist theorem helps to find the perfect sweet spot where all the necessary information is recorded but nothing extra.
How the Nyquist theorem works
Analog signals have a frequency, or how many times they go up and down in a second. This frequency is measured in hertz. Claude Shannon's explanation of the theorem is: "If a function x(t) contains no frequencies higher than B hertz, it is completely determined by giving its ordinates at a series of points spaced 1/(2B) seconds apart." To accurately reproduce a signal, the sample rate must be twice the highest frequency.
To help illustrate this, imagine a sensor on the earth with the job of measuring sky brightness. Imagine it only took one measurement every 24 hours. If you read the results back later, you would be led to believe that the sky is the same brightness all day, an inaccurate result. What if it was measured every 18 hours? The results would be very confusing, going between full brightness, complete darkness and somewhat dim, seemingly at random.
Now imagine the sensor took a measurement every 12 hours. The results would show one period of light followed by a period of darkness; this would accurately describe our 24-hour day/night cycle on earth. As shown by the Nyquist theorem, to accurately measure the 24-hour period of the rotation of the earth, you must take a measurement at least twice its rate, or every 12 hours.
The Nyquist theorem defines the minimum sample rate for the highest frequency that you want to measure. The Nyquist rate is 2x the given frequency to be measured accurately. The theorem can be used in reverse. The Nyquist frequency is the highest frequency that equipment of a given sample rate can reliably measure, one-half the given sample rate.
The Nyquist theorem is an important part of information theory. In radio communications, it is used with Shannon's law to help establish system bandwidth with a specific signal-to-noise ratio.
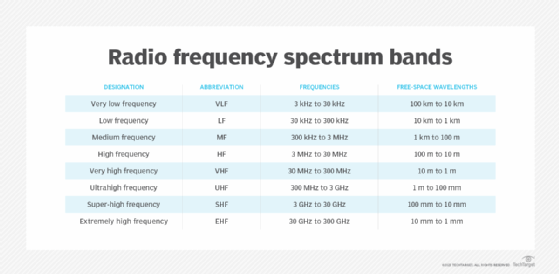
Nyquist theorem and aliasing
Aliasing is the undesirable imperfections introduced during analog to digital conversion. It may present as unwanted frequencies in an audio recording or strange patterns in an image. Some information is necessarily lost during analog to digital conversion; therefore, two differing analog signals may have the same output when converted to digital.
If the Nyquist theorem is not obeyed, higher frequency information is recorded in too low a sample rate, resulting in aliasing artifacts.
Several techniques can reduce aliasing in a reproduced signal.
Pure sine wave signals do not exist in nature. Most signals have extremely high-frequency components such as harmonics and resonance well outside of the Nyquist frequency of any practical analog-to-digital capture device. To reduce the effects of these components, a low-pass filter is applied to remove any extraneous high frequencies before the signal is sampled.
Analog low-pass circuitry does not have perfect responsiveness. Also, the signal may have some desirable components slightly higher than the target frequency. It is therefore advantageous to choose a sample rate slightly higher than the optimal Nyquist rate.
Nyquist theorem in audio signals
The Nyquist theorem is important for capturing audio through digital methods. The average human ear is only sensitive to frequencies between 20 Hz and 20 kHz. Therefore, according to the Nyquist theorem, the optimal sample rate for the human ear is 40 kHz. This is why standard music and audio recording sample rates are close to this value. Any values greater than 40 kHz would be undetectable to most people.
The standard CD audio rate of 44.1 kHz was chosen to satisfy the Nyquist frequency while being compatible with existing video equipment. The Digital Audio Tape (DAT) format is similarly at 48 kHz.
Telephones are optimized to transmit the human voice. The frequencies required for speech to be intelligible fall between 300 and 3400 Hz. Therefore, the sample rate of 8 kHz is used for narrowband voice-only communication. This lowers the amount of data that needs to be transmitted and is a popular sample rate for telephone and VoIP system codecs such as G.771. Wideband voice, or HD voice, uses 16 kHz to better capture the human voice for more clear calls.
Neither of these is sufficient to cover the whole range of hearing, so most music played over telephone or conferencing systems sounds distorted. Many video conferencing applications offer an option for high-quality sound or music playback to use the higher sample rates.
Note that the sample rate, measured in hertz is, is different from the bit depth measured in bits and the bit rate measured in bits per second.
Nyquist theorem in pictures and video
The principles of the Nyquist theorem also apply to digital photography and videography. Digital imaging sensors capture light in discrete pixel sites. A sampling artifact occurs when the camera lens reduces the scene detail to a smaller level than the pixel sites. This is called a moiré pattern. You can see this effect as a strange overall pattern in finely detailed areas, such as a picture of a finely striped shirt or of a screen door. It can also become present in downscaled images.
Various methods can fight this effect. In high-end digital cameras, a physical optical low-pass filter may be used to reduce the fine detail and break up aliasing. In consumer cameras and cellphones, digital methods are employed in post-processing steps to remove them.
See also: radio access network, wireless, cognitive radio, base station and multiplexing
