OS X
What is OS X?
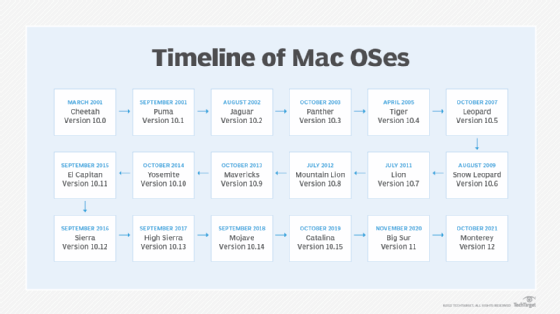
OS X, also referred to as macOS X or Mac OS X, is Apple's proprietary, Unix-based operating system. Released in 2001 as the successor to Mac OS 9, OS X incorporates support for Unix-based applications as well as for those written specifically for the Mac.
Although the name macOS X was used for several OS X versions, Apple rebranded the OS to simply macOS starting with the release of macOS Sierra in 2016. This change helped align it with the naming conventions of the company's other OSes, such as iOS, watchOS and tvOS.
Since the first version of OS X, the operating system has gone through a series of upgrades. The latest macOS version at time of publication, Ventura 13.4, was released in May 2023. Each iteration of the OS includes improvements to functionality. It is renowned for its smooth, sleek design and user-friendly interface, as well as other characteristics that are iconic to Apple's design ethos.
OS X blends Unix's proven stability and flexibility with Apple's intuitive user interface (UI) design, providing users with a highly functional and seamless computing environment. Key features of OS X include a multilingual UI and support for an extensive range of software and hardware.
It also boasts advanced graphics processing, robust security mechanisms, and seamless integration with other Apple devices and services. This approach further enhances the user experience by facilitating synchronization of data and settings across devices.
What is OS X Base System?
OS X Base System generally refers to Apple's recovery partition that is included on the hard drive of Mac computers. This recovery system is a critical component of macOS or OS X because it provides several utilities to troubleshoot issues, repair the system and reinstall the entire OS when necessary.
OS X Base System was first introduced in OS X Lion. This hidden partition included several utilities via macOS Recovery, including Disk Utility, Terminal, options for reinstalling macOS, restoring from a Time Machine backup or browsing the web with Safari.
Explore more about macOS and learn how to select the right Mac computer to meet your needs.
