enterprise architecture framework
What is an enterprise architecture framework?
An enterprise architecture framework (or simply EA framework) is the collection of processes, templates and tools that software teams use to plan and build large, enterprise-grade application architecture systems. Alongside an enterprise architecture's conceptual blueprint, the specific purpose of a framework is to help architects, designers and engineers understand the logical structure and component relationships that define that system.
An EA framework often segments an architecture into layers, architectural views or domains based on core application logic. Since there are many types of enterprise architecture designs to implement, a the benefits of an EA framework typically become more apparent as the complexity and diversity of the architecture increases.
EA framework tooling is often cited as an important resource for companies pursuing digital transformation initiatives, which has spurred a strong vendor market aimed at this aspect of software development. Ardoq and SAP PowerDesigner are examples of providers aiming to ease the process of framework implementation and management.
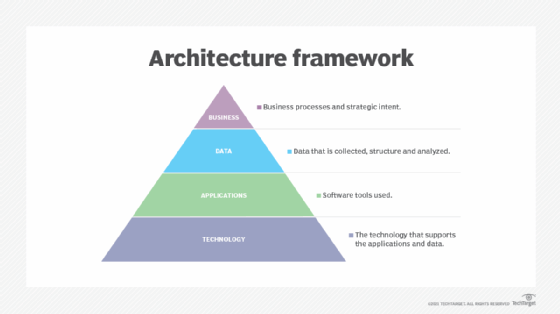
EA framework components
There are three basic components that make up the creation of an enterprise architecture framework:
- A description of the architecture that outlines the procedures surrounding documentation creation and access;
- A design method that dictates the steps architects should follow when forming an architectural model; and
- A record of the technical knowledge, niche proficiencies and general experience levels possessed by those involved, including a record of any notable skill gaps to address.
How to implement an EA framework
To successfully implement an enterprise architecture framework, each organizational stakeholder should be able to understand the architecture from their own viewpoint in the organization. To do so, software teams should adhere to these six important implementation steps:
- Identify the architecture's overarching goals and context, as well as the degree of management complexity its dependencies will introduce.
- Become familiar with established framework models (covered below) and select one that aligns with the organization's existing culture and business goals.
- Determine how introducing a certain framework will affect application development needs or future change requests from the business side.
- Identify and document the specific business rules that will act as architectural constraints.
- Create visual models and diagrams that provide transparent and accessible information regarding the architecture, its critical characteristics and the various software projects that fall within its realm.
- Consolidate the architecture by integrating the framework's various components with the organization's existing application components, databases and development workflows.
Types of EA frameworks
The type of EA framework used will differ depending on the chosen type of enterprise architecture. Some of these enjoy wide use across the software industry as de-facto standards for framework implementation, while others are closely associated with more specialized initiatives.
Some of those frameworks considered standard across the industry include:
- The Zachman Framework, which is often used to define and standardize what components and processes should be used to develop an IT architecture.
- The Open Group Architectural Framework (TOGAF), a popular framework designed to help software engineers ensure development projects support business goals, maintain timelines, stay on budget and improve architectural resilience.
- Open Agile Architecture (O-AA), another standard fostered by The Open Group and largely geared toward self-governing software teams tasked with rolling out both Agile and digital transformation initiatives.
Other specialized types of frameworks include:
- The European Space Agency Architectural Framework, which aims to facilitate system of systems engineering for the internet of space.
- SAP Enterprise Architecture Framework, an extension of TOGAF calibrated to readily integrate the framework with SAP-based platforms and tooling.
- ISO 19439 Framework, which dictates guiding concepts surrounding consistency, convergence and interoperability for the various modeling methodologies an organization uses.
- FDIC Enterprise Architecture Framework, which -- alongside the FDIC's IT Governance Framework -- focuses heavily on defining and documenting roles and responsibilities related to information security.
- Unified Architecture Framework (UAF), a framework created to support software development initiatives within the U.S. military and federal government.






