IP telephony (Internet Protocol telephony)
What is IP telephony?
IP telephony (Internet Protocol telephony) is a general term for technologies, products and services that use the Internet Protocol's packet-switched connections to support voice calling, voicemail, video calling, video conferencing, faxing and instant messaging (IM).
Traditionally, these communications have been carried over the dedicated circuit-switched connections of the public switched telephone network (PSTN). Using the internet, calls travel as packets of data on shared lines, avoiding the tolls of PSTN.
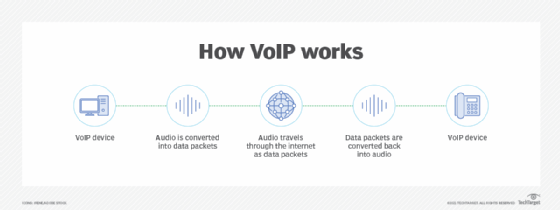
IP telephony works by converting voice calls, faxes and other information into digital signals. These digital signals travel through IP networks, such as the internet, as data packets, using IP packet-switched connections. Voice features within IP technology -- such as voice calls and voicemail -- are referred to as voice over IP (VoIP).
IP telephony was introduced in 1991 with the creation of the first VoIP application, Speak Freely. The next year, InSoft released Communique for desktop video conferencing. In 1995, Intel, Microsoft and Radvision began to standardize VoIP systems.
In addition to voice calling, IP telephony also includes other features, such as the following:
- video calling
- video conferencing
- IM
- text messaging
- faxing
IP telephony vs. VoIP
The term IP telephony is often used interchangeably with VoIP. The two terms overlap, and it is not considered incorrect to use them synonymously, as they both use a local area network to connect to the internet via a router. However, defined in the most formal and specific terms:
- VoIP is more specific and describes the standardized technologies that deliver voice-based features, such as calling and voicemail, through IP-based networks; and
- IP telephony, on the other hand, is a more general term encompassing the full set of technologies, features and products -- this includes voice-based features, as well as nonvoice-based features, such as IM.
What are the IP telephony business benefits?
IP telephony services can offer the following benefits to organizations of all sizes:
- No need to maintain two networks. Before IP telephony, businesses needed to deploy and maintain separate networks for internet and phone.
- Lower costs. Using IP telephony is significantly more cost-effective than using wired phone services on a similar scale. Long distance and international calls are also less expensive with IP telephony.
- Streamlined infrastructure. IP telephone systems can integrate with existing infrastructure, enabling communications to work through business applications. For example, faxes can be sent and received via email.
- Scalability. Deploying new IP business telephone lines, which can be done through an online interface, is far simpler and easier than adding new wired phone lines.
- Mobility. IP phones can be accessed beyond a physical office, from portable computers and mobile devices.
For more in-depth information on how VoIP technologies work, read our definition.
What are the challenges of IP telephony?
Despite the benefits associated with the use of IP telephony, its use can carry specific challenges:
- Problems with 911 calls. Despite the Federal Communications Commission requirement that VoIP services offer 911 as a standard feature, it is up to callers to register their physical address with their provider. If they neglect to do this, VoIP 911 calls may not provide the callers' proper location and phone number information.
- Server latency. Services require a high-speed internet connection. Disruptions in internet connection strength can lead to server latency.
- Power requirements. IP telephony systems connected to office power supplies will not work during power outages.
Who manages IP telephony?
IP telephony is managed by providers of VoIP and unified communications (UC) services. Well-known vendors that manage IP telephony services include the following:
- Avaya
- Microsoft
- RingCentral
- Skype
- Zoom
For a more comprehensive overview of the differences between IP telephony and VoIP, click here.







