Tor browser
What is the Tor browser?
The Tor (the onion routing) browser is a web browser designed for anonymous web surfing and protection against traffic analysis. Although Tor is often associated with the darknet and criminal activity, law enforcement officials, reporters, activists, whistleblowers and ordinary security-conscious individuals often use the browser for legitimate reasons.
The United States Navy originally designed the browser to protect sensitive U.S. government communications. While Tor continues to be used by the government, it is now an Open Source, multi-platform browser that is available to the public. Today, human rights activists and dissidents who need to keep their internet activities private from oppressive governments, law enforcement, intelligence agencies and criminals use Tor, for example.
Law enforcement agencies are able to use various techniques and tools to track down the users of Tor, especially if the sites they visit are not using end-to-end encryption (E2EE). The browser uses exit relays and encrypted tunnels to hide user traffic within a network but leaves the endpoints more easily observable and has no effect beyond the boundaries of the network.
How Tor works
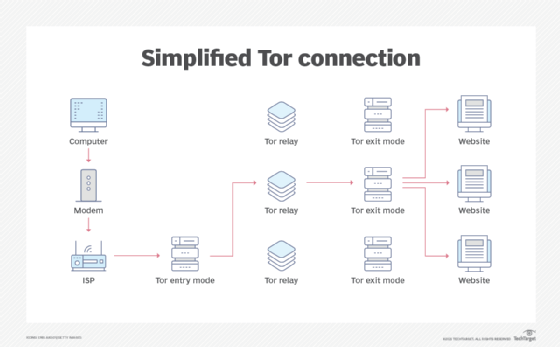
The Tor browser works by using a technology known as onion routing. The onion router is a peer-to-peer (P2P) overlay network that enables users to browse the internet anonymously. Onion routing uses multiple layers of encryption to conceal both the source and destination of information sent over the network. It is designed so no one can monitor or censor online communication.
Once a user installs Tor, the browser uses Tor servers to send data to an exit node, which is the point at which data leaves the network. Once this data has been sent, it is encrypted multiple times before being sent to the next node. Repeating this process makes it difficult to trace the data back to the original source. In addition to encryption, the Tor browser does not track browsing history or store cookies.
Levels of security
The Tor browser offers three levels of security, including the default level plus two additional levels. Each level provides a different degree of protection, with the maximum protection found in the highest level.
- On the default setting, the browser is the most user-friendly; however, this setting provides the lowest level of security.
- The second level provides more security but offers a slower experience. For example, JavaScript-enabled sites may run slower as this setting disables JavaScript on non-Hypertext Transfer Protocol Secure (HTTPS) sites.
- The third and highest level of security disables some fonts and images, in addition to JavaScript, on all sites.
Tor weaknesses
Although Tor is more secure than most commonly used browsers, it isn't impervious to attack. While Tor protects against traffic analysis, it does not prevent end-to-end correlation, which is the process of using more than one data point from a data stream to identify the source and purpose of an attack.
Other Tor browser weaknesses include the following:
- Consensus blocking. The Tor exit relay is vulnerable to a class of attacks that enables a malicious user to temporarily block consensus nodes from communicating. This problem is similar to a denial of service (DoS) attack, which blocks access to a website by flooding it with so many requests that it is impossible for the servers to keep up.
- Eavesdropping. The Tor exit nodes are vulnerable to eavesdropping, as the traffic passing through does not use E2EE. While this method does not explicitly reveal a user's identity, the interception of traffic can expose information about the source.
- Traffic analysis attack. In a passive traffic analysis attack, an intruder extracts information and matches that information to the opposite side of the network. In an active traffic analysis attack, the intruder modifies packets following a pattern to assess their impact on traffic.
- Tor exit node block. Websites can block users using the Tor browser from accessing their page.
- Bad apple attack. In 2011, a documented attack revealed the exposure of the Internet Protocol (IP) addresses of BitTorrent users on the Tor browser.
- Sniper attack. A type of distributed DoS (DDoS) attack, a sniper attack overwhelms exit nodes until they run out of memory. An attacker can reduce the number of functioning exit nodes, increasing the chances of users using exit nodes controlled by the attacker.
- Relay early traffic confirmation attack. In 2014, Tor released a security advisory after discovering a deanonymization attempt on the browser's users. Bad actors modified the headers of cells and sent them back to the user. If the entry node was also part of the attack, an attacker could capture the IP address of users by the attacking relays.
- Mouse fingerprinting. In 2016, a researcher discovered they could track mouse fingerprinting using a time measurement at the millisecond level. Using this method, third parties could identify users by tracking their mouse movements when using a specific website and comparing their mouse movements on the Tor browser or a regular browser.
Access to the dark web
The dark web refers to the parts of the internet not indexed by search engines. It contains a range of websites, including forums and marketplaces, that require specific software for access. While anyone can surf the public internet, the dark web is a private network where users do not disclose their real IP addresses. This makes it a more secure place to do business on the web but also a place where many illegal activities occur.
Users such as the military, politicians, journalists and criminals use the dark web. The dark web was created to enable individuals or groups to communicate in a way that is, in their view, untraceable. Besides potential illegal uses, the dark web also serves a number of legitimate purposes, including enabling whistleblowers to share information that they might not otherwise be able to share.
The Tor browser enables people to have access to the dark web. While many associate the dark web with illegal activities, the Tor network also has a number of legitimate uses. These include communicating or browsing in countries implementing internet censorship.
Furthermore, although the Tor network can be used for illegal activity, it is not illegal to use it.