VIPER (View, Interactor, Presenter, Entity and Router)
VIPER (View, Interactor, Presenter, Entity and Router) is a design pattern for software development that develops modular code based on clean design architecture. The modules in VIPER are protocol-oriented and each function, property input and output is performed by way of specific sets of communication rules.
VIPER is often used to develop smartphone apps and is heavily used in iOS along with Swift, Apple’s programming language. VIPER is based on SOLID design principles, specifically the single responsibility principle.
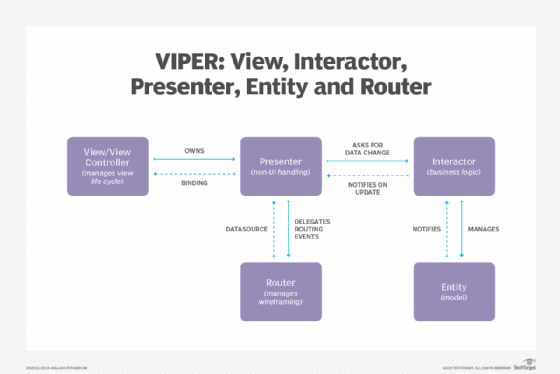
The words represented in the VIPER acronym note the types of modules in the design pattern:
- View (also known as the view controller): Both displays information for the user and detects user interaction. The Presenter is the only module the View module has contact with.
- Interactor: Manipulates entities or models and fetches and stores data.
- Presenter: Contains the user interface and prepares data for presentation. The Presenter contacts the Interactor for data requests, the View to present prepared data to the user and the Router in order to hand off objects.
- Entity: The data models that are manipulated by the Interactor.
- Router (also known as wireframe): Handles navigation in the module or application. It creates the View and wires the Presenter to act as output to the Interactor. Contacts the Presenter in order to route requests.
The abstraction of code into the layers of entities, program logic and devices and external interfaces is a commonality seen in VIPER and in clean design architectures in general.