virtual reality
What is virtual reality?
Virtual reality is a simulated 3D environment that enables users to explore and interact with a virtual surrounding in a way that approximates reality, as it is perceived through the users' senses. The environment is created with computer hardware and software, although users might also need to wear devices such as helmets or goggles to interact with the environment. The more deeply users can immerse themselves in a VR environment -- and block out their physical surroundings -- the more they are able to suspend their belief and accept it as real, even if it is fantastical in nature.
What are the main types of virtual reality?
The VR industry still has far to go before realizing its vision of a totally immersive environment that enables users to engage multiple sensations in a way that approximates reality. However, the technology has come a long way in providing realistic sensory engagement and shows promise for business use in a number of industries.
VR systems can vary significantly from one to the next, depending on their purpose and the technology used, although they generally fall into one of the following three categories:
- Non-immersive. This type of VR typically refers to a 3D simulated environment that's accessed through a computer screen. The environment might also generate sound, depending on the program. The user has some control over the virtual environment using a keyboard, mouse or other device, but the environment does not directly interact with the user. A video game is a good example of non-immersive VR, as is a website that enables a user to design a room's decor.
- Semi-immersive. This type of VR offers a partial virtual experience that's accessed through a computer screen or some type of glasses or headset. It focuses primarily on the visual 3D aspect of virtual reality and does not incorporate physical movement in the way that full immersion does. A common example of semi-immersive VR is the flight simulator, which is used by airlines and militaries to train their pilots.
- Fully immersive. This type of VR delivers the greatest level of virtual reality, completely immersing the user in the simulated 3D world. It incorporates sight, sound and, in some cases, touch. There have even been some experiments with the addition of smell. Users wear special equipment such as helmets, goggles or gloves and are able to fully interact with the environment. The environment might also incorporate such equipment as treadmills or stationary bicycles to provide users with the experience of moving through the 3D space. Fully immersive VR technology is a field still in its infancy, but it has made important inroads into the gaming industry and to some extent the healthcare industry, and it's generating a great deal of interest in others.
collaborative VR is sometimes cited as a type of virtual reality. In this model, people from different locations come together in a virtual environment to interact with one another, with each individual represented by a projected 3D character. The users typically communicate through microphones and headsets.
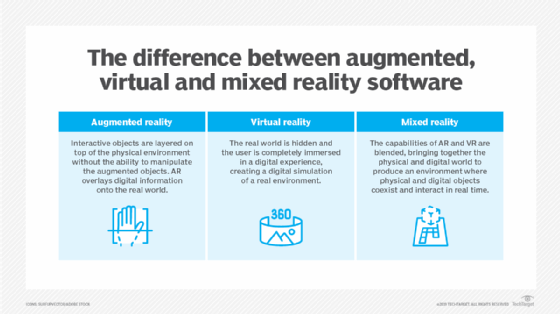
Augmented reality also is sometimes referred to as a type of virtual reality, although many would argue that it is a separate but related field. With augmented reality, virtual simulations are overlaid onto real-world environments in order to enhance or augment those environments. For example, a furniture retailer might provide an app that enables users to point their phones at a room and visualize what a new chair or table might look like in that setting.
Another category that is sometimes considered a type of virtual reality is mixed reality, which blends the physical and virtual worlds into a single space. Like augmented reality, however, it is more often considered a separate but related field. In fact, there's been a growing consensus to group virtual reality, augmented reality and mixed reality under the umbrella term "extended reality," which provides a handy way to reference all three, while still distinguishing among them.
Today's VR technologies and applications have inspired multiple companies and experts to advocate for advanced uses of the metaverse.
For more on the metaverse, read the following articles:
Metaverse pros and cons: Top benefits and challenges
Metaverse interoperability challenges and impact
Metaverse privacy concerns and how to address them
The Metaverse Standards Forum: What you need to know
Metaverse vs. multiverse vs. omniverse: Key differences
Top metaverse platforms to know about
Top metaverse cybersecurity challenges: How to address them
7 top technologies for metaverse development
Top 8 metaverse events in 2022
Top metaverse investors and how to start investing
12 top metaverse predictions for 2030
Web3 vs. metaverse: What's the difference?
How can virtual reality be used?
Virtual reality is often associated with gaming because the industry has been at the forefront of the VR effort, as evidenced by the popularity of products such as Beat Saber, Minecraft VR and Skyrim VR. Even so, there has been a growing interest in the potential of VR across a number of other areas:
- Training. VR makes it possible to train personnel safely, efficiently and cost-effectively. It can be especially beneficial to those in high-risk or highly specialized positions, such as firefighters, EMTs, police officers, soldiers, surgeons or other medical personnel.
- Education. VR offers educational institutions new methods for teaching and learning. It can provide students with intimate insights into environments that are typically inaccessible, while keeping them engaged in the learning process. For example, a history teacher might use VR to show students firsthand what life was like in ancient Greece or China.
- Healthcare. VR has the potential to benefit individuals across the healthcare industry, including patients, practitioners and researchers. For example, VR shows promise in treating disorders such as anorexia, anxiety or post-traumatic stress disorder (PTSD). On the other hand, doctors might be able to use VR when working with the patients to explain diagnoses or treatment options. VR could also benefit individuals who are physically limited in some way.
- Retail. VR has already made some inroads into retail, but the industry has only scratched the surface. With the right apps, customers will be able to try on clothes, decorate their homes, experiment with hair styles, test eye glasses and in general make more informed decisions about products and services.
- Real estate. VR can benefit real estate in a number of ways. For example, architects can show detailed plans in 3D; home buyers can tour homes virtually; building engineers can tour HVAC systems; and home owners can see what their remodels would look like.
- Entertainment. VR has already had an impact on gaming, but it also promises to transform the film and television industries, providing viewers with an immersive experience that puts them right into the scene. VR could also lead to an entire industry in virtual tourism, making it possible for people to experience places that they might never be able to see in-person.
The simplest form of virtual reality is a 3D image that can be explored interactively through a personal computer, usually by manipulating keys or the mouse so that the content of the image moves in some direction or zooms in or out. More sophisticated efforts involve such approaches as wraparound display screens, physical rooms augmented with wearable devices, or haptic devices that let users "feel" the virtual images.
See also: VR room, virtual reality cloud, immersive virtual reality
