
user behavior analytics (UBA)
What is user behavior analytics (UBA)?
User behavior analytics (UBA) is the tracking, collecting and assessing of user data and activities using monitoring systems. UBA is increasingly referred to as user and entity behavior analytics (UEBA) to reflect that user is just one category of entities with observable behaviors on modern networks. Other entities can include processes, applications and network devices.
UBA technologies analyze historical data logs -- including network and authentication logs collected and stored in log management and security information and event management (SIEM) systems -- to identify patterns of traffic caused by the behavior of users, both normal and malicious. UBA and UEBA systems are primarily intended to provide cybersecurity teams with actionable insights when the systems detect unusual behavior.
While UBA systems don't take action based on their findings, they can be configured to automatically adjust the difficulty of authenticating user accounts that show anomalous behavior or otherwise deviate from normal behavior.
What is UEBA and how does it differ from UBA?
The primary differences between the terms user behavior analytics and user and entity behavior analytics are the following:
- UEBA is newer. In 2015, analyst firm Gartner published a market guide for what it coined as user and entity behavior analytics.
- UEBA systems track more than just user activity. UEBA tracks the activity of devices, applications, servers and data. Instead of analyzing only user behavior data, this technology combines user behavior data with behavior data from entities.
- UEBA takes things a step further. UEBA systems may produce a higher volume of data and provide more complex reporting options than original UBA systems.
User and entity behavior analytics technologies have the same capabilities as traditional UBA, according to Gartner, although UEBA systems may use more advanced analytics techniques. While UBA is designed to track insider threats, UEBA is designed to use machine learning to look for more types of anomalous activities associated with more types of threats, including advanced threats, that may be obscured by legitimate network activities. Enterprises often use UEBA in conjunction with SIEM technologies to better analyze the information gathered.
This article is part of
What is data security? The ultimate guide
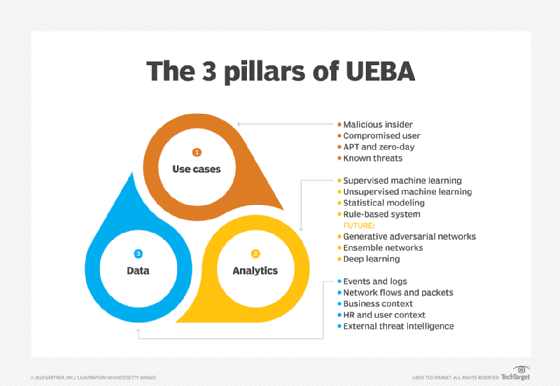
How user and entity behavior analytics works
UEBA works by collecting various types of data, such as user roles and titles, including access, accounts and permissions; user activity and geographical location; and security alerts. This data can be collected from past and current activity, and the analysis takes into consideration factors such as resources used, the duration of sessions, connectivity and peer group activity to compare anomalous behavior to. It also automatically updates when changes are made to the data, such as promotions or added permissions.
UBA and UEBA systems don't necessarily report all anomalies as risky. Instead, they evaluate the behavior's potential impact. If the behavior involves less-sensitive resources, it receives a low impact score. If it involves something more sensitive, such as personally identifiable information, it receives a higher impact score. This way security teams can prioritize what to follow up on while the UBA system automatically restricts or makes it more difficult to authenticate the user showing anomalous behavior.
Behaviors that UBA and UEBA systems monitor are generally those associated with specific attacks or other security events. Monitored behaviors include the following:
- brute-force attacks;
- improper data access;
- data loss;
- lateral movement by unauthorized users; and
- questionable activities by privileged users who may be malicious insiders.
Machine learning algorithms enable UBA systems to reduce false positives and provide clearer and more accurate actionable risk intelligence to cybersecurity teams. UBA systems may also use threat intelligence feeds to augment and support machine learning functions.
Why companies need user and entity behavior analytics
Behavior analysis systems first appeared in the early 2000s as tools to help marketing teams analyze and predict customer buying patterns.
Current user behavior analytics tools have more advanced profiling and exception monitoring capabilities than SIEM systems and are used for the following two main functions:
- to determine a baseline of normal activities specific to the organization and its individual users; and
- to identify deviations from the norm -- UBA uses big data and machine learning algorithms to assess these deviations in near-real time.
While applying user behavior analytics to just one user may not be useful for finding malicious activity, running it on a large scale can give an organization the ability to detect malware or other potential cybersecurity threats, such as data exfiltration, insider threats and compromised endpoints.
UEBA tools
The market for user behavior analytics tools continues to grow and evolve as the technology matures. Some of the leading UBA and UEBA products are the following:
- Cynet 360 AutoXDR
- Rapid7 InsightIDR
- Fortinet FortiInsight
- IBM QRadar User Behavior Analytics
- Microsoft Defender for Identity
As the market continues to consolidate, UEBA and UBA functions are also increasingly incorporated into comprehensive cybersecurity packages from leading vendors.
UEBA vs. SIEM vs. SOAR vs. XDR: Key differences in terminology and technology
UEBA products are just one way to address threat detection. Other related technologies include the following:
- SIEM systems collect and aggregate data from multiple sources to identify potential threats and issue alerts. SIEM systems are commonly used for detecting compliance issues and use statistical models to identify suspicious behavior patterns correlated with cyber attacks. SIEM products can overwhelm information security teams with a high volume of alerts, many of which may be false positives.
- Security orchestration, automation and response (SOAR) systems improve on SIEM systems by gathering rich event data and using automation to identify potential threats and anomalies. SOAR systems require integration with security data sources and still require significant effort from information security analysts.
- Extended detection and response (XDR) systems are the latest generation of endpoint detection and response (EDR) systems and network detection and response (NDR) systems. While EDR is focused on the endpoint systems -- end-user computers and organizational servers -- NDR monitors network transmissions. XDR is an emerging technology that is converging with UBA and UEBA functionality, as well as with SOAR and SIEM.
Given the abundance of related technologies, the different types of threat detection tools have considerable overlap. As with other types of information security systems, UBA and UEBA should be considered one of many tools in the cybersecurity toolkit. Despite the potential for overlap between these different systems, understanding the organization's use cases can help point cybersecurity professionals in the right direction.
UEBA and SIEM technology: Why use them in tandem?
Many organizations are opting to use UEBA and SIEM technologies in tandem. Looking at the differences between these two types of system highlights how they complement each other:
- UEBA systems focus on real-time data capture and analysis. SIEM systems examine event data over the course of a set length of time, from a single point in time to a restricted period of time.
- UEBA systems rely on machine learning to automatically flag potential threats as they are happening, while SIEM systems provide cybersecurity professionals a powerful tool to manually search for threats.
- UEBA systems amass events from many different types of data, including logs and both structured and unstructured data sets. UEBA depends on machine learning to assemble evidence of threats and identify approaches to mitigating threats. In contrast, SIEM systems tend to have more structures imposed on the inbound data, which usually comes from structured logs.
- UEBA systems depend on risk scoring to compare different threats and to identify which systems are at risk and in what ways. SIEM systems depend on alerts and notices generated automatically when the system detects a pattern of activities that correlates with known attacks.
While combining SIEM and UEBA systems can benefit organizations, some experts suggest that SIEM is poised to incorporate and replace UEBA.







