Wi-Fi 6
What is Wi-Fi 6 (802.11ax)?
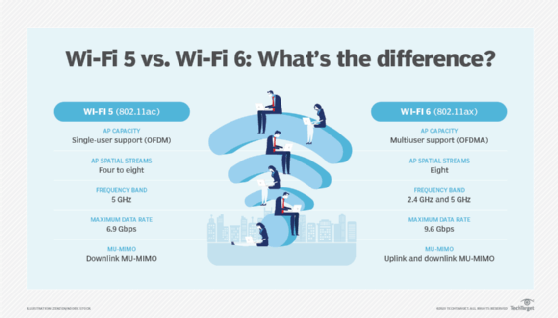
Wi-Fi 6, also known as 802.11ax, is the latest generation and standard for wireless networking that replaces the 802.11ac, or Wi-Fi 5, standard. Prior to the release of Wi-Fi 6, Wi-Fi standards were identified by version numbers ranging from 802.11b to 802.11ac.
Wi-Fi 6 is the most current standard for all things Wi-Fi. Its performance specifics cover a range of mandatory and optional features as specified in the body of the written standard by IEEE. As with any latest Wi-Fi standard, Wi-Fi 6 is potentially better than its predecessors because of modulation and signal processing techniques that promise a more extensive network experience in high-density environments.
Wi-Fi 6 uses the same 2.4 gigahertz and 5 GHz bands as 802.11a/g/n/ac but also has the option to use 6 GHz. This is new and different, and when 6 GHz is in play, it's referred to as Wi-Fi 6E. But it's all still 802.11ax.
As with earlier standards, Wi-Fi 6 provides the same basic functionality -- network access via radio technology -- but with potential improvements in capacity, coverage and performance. These benefits are most realized in well-designed wireless local area network (WLAN) environments where client devices also support Wi-Fi 6. This is an important point because older clients, interference and poor design work against Wi-Fi 6 just as they did with earlier standards. Wi-Fi 6 is also half-duplex, shared media technology.
Benefits of Wi-Fi 6
Assuming proper implementation and bug-free code from the WLAN vendors, Wi-Fi 6 is a significant evolution for Wi-Fi with impressive benefits. With a maximum theoretical data rate of almost 10 gigabits per second (Gbps) when eight spatial streams and 160 megahertz channels are used, it's easy to focus on speed. Real-world performance, however, is always inferior to theoretical specifications.
When properly implemented, Wi-Fi 6 can provide the following benefits:
- lower overall latency;
- improved connection quality;
- potentially better intracell roaming;
- faster data transfer and increased data capacity per cell;
- better handling of applications such as 4K or 8K video;
- support for higher user density per access point (AP) and for the overall WLAN system;
- improved power efficiency and longer client device battery life with better control of sleep modes, called target wake time; and
- more efficient wireless operations with techniques like orthogonal frequency-division multiple access (OFDMA), which enable new slicing of channels to simultaneously accommodate more clients of varying capabilities.
Additionally, with Wi-Fi 6, channels can be broken into a greater number of subchannels called resource units, improving efficiency for more clients simultaneously. Also, when 6 GHz is in play, there's less interference with other devices, like baby monitors and cordless landline phones.
Older WLAN standards operated under the paradigm of "only one device can use the medium at a time." But OFDMA accommodates multiple clients with lesser channel-width needs to communicate with the AP at the same time. Again, efficiency is just as significant as speed.
What makes Wi-Fi 6 faster?
A Wi-Fi 6 router or AP is just part of the overall network and bridges wireless 802.11 clients to the wired 802.3 Ethernet side of the LAN. Wi-Fi 6 APs can use uplinks to Ethernet switches that can range up to 10 Gbps to support the higher-capacity nature of 802.11ax.
Wi-Fi 6 supports a new top-end modulation of 1024 quadrature amplitude modulation -- an order of magnitude faster than 802.11ac's 256 QAM top end. Wi-Fi 6 also supports features such as multiuser multiple input, multiple output (MU-MIMO) to enable more than one client to use more than a single spatial stream at a time.
Basic service set (BSS) coloring enables better handling of wireless energy on the same channel as a given AP. In past standards, a competing cell on the same channel could slow down an AP while 802.11 politeness mechanisms sorted out who should transmit and who should wait for a quiet moment to take a turn.
BSS coloring reduces that slowness by enabling Wi-Fi 6 cells to be more nuanced in what energy they care about and want to coexist with. It all adds up to so-called faster speeds, along with more processing power and memory built into the latest APs and controllers.
How to upgrade to Wi-Fi 6
At home or in small and medium-sized business environments, upgrading to Wi-Fi 6 can be fairly simple: Get a new wireless router, phase in Wi-Fi 6 clients and you have upgraded. You may also want to consider increasing your internet connection; if you don't, it may become a bottleneck.
In bigger networks, however, things get a lot more complicated. Depending on what vintage switches and wireless controllers -- if applicable -- you have in service, both may need to be updated to accommodate Wi-Fi 6 APs. New Wi-Fi 6 APs may have higher Power over Ethernet requirements than older .11ac hardware.
If you want to take advantage of beefier uplinks to APs than the typical long-running 1 Gbps connection that has served Wi-Fi 5 and other previous standards, then you might also be faced with cabling upgrades. Additionally, you might find a wireless redesign is needed if your client counts are increasing significantly. In this case, an upgrade to large wireless environments would certainly be expensive, depending on several factors related to Wi-Fi and the underlying LAN.
To get an upgrade right, a methodical inventory and audit of your current environment are needed to expose areas not yet ready for Wi-Fi 6. Then, there's the replacement of existing client devices to fully use the new wireless technology. How to do that varies wildly across environments.
Wi-Fi version numbers and naming system
It's important to realize the hierarchy of authority in the Wi-Fi universe. The Federal Communications Commission sets the rules for spectrum usage, and IEEE writes the actual standards.
The Wi-Fi Alliance tries to get more Wi-Fi products sold for its member companies, while creating various certification programs with varying degrees of relevance and effectiveness. In 2018, the Wi-Fi Alliance added branding, of sorts, to Wi-Fi standards with simple numerical conventions, such as Wi-Fi 5, Wi-Fi 6 and Wi-Fi 6E. This naming system aims to decrease end-user confusion and identify compatibility between devices.
Whether the branding works better than using the IEEE standard numbers to identify a given Wi-Fi technology is up for debate. Most wireless professionals still use the standards nomenclature along with the numbers the Wi-Fi Alliance threw into the mix.
The following are the renamed Wi-Fi standards and the year that the standard was introduced.
| IEEE standard | Year introduced | Wi-Fi Alliance branding |
| 802.11b |
1999 |
Wi-Fi 1 |
| 802.11a |
1999 |
Wi-Fi 2 |
| 802.11g |
2003 |
Wi-Fi 3 |
| 802.11n |
2009 |
Wi-Fi 4 |
| 802.11ac |
2014 |
Wi-Fi 5 |
| 802.11ax |
2019 |
Wi-Fi 6 |
| 802.11ax (with 6 GHz spectrum) |
2020 |
Wi-Fi 6E |
| 802.11be |
Expected in 2024 |
Wi-Fi 7 |
A great deal of backward compatibility is written into the standards but can be negated in configuration for greater performance. For example, legacy data rates can be disabled, thus rendering 802.11b client devices unusable in an environment built on the 802.11ax standard.