acceptable use policy (AUP)
What is an acceptable use policy (AUP)?
An acceptable use policy (AUP) is a document stipulating constraints and practices that a user must agree to for access to a corporate network, the internet or other resources. Many businesses and educational institutions require employees or students to sign an AUP before being granted a network ID.
From an information technology (IT) perspective, an AUP states what a user can and cannot do when using computers and computing resources. This applies whether the organization provides the device or it is a personal device that the user provides.
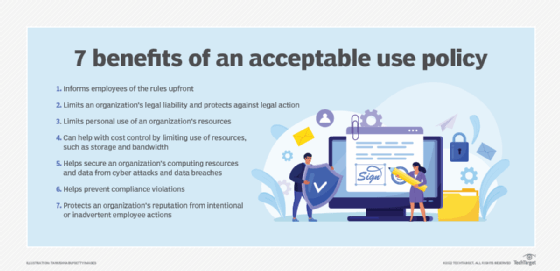
One of the benefits of an AUP is that it spells out acceptable and unacceptable employee behavior and actions. AUPs also provide a company with a legal mechanism to compel compliance, and they describe penalties for noncompliance.
9 key elements of an acceptable use policy
Internet service providers (ISPs) usually require new customers to sign an AUP. It may be part of a service level agreement (SLA) between the ISP and customer.
The following are nine stipulations that might be included in an ISP's acceptable use policy:
- not using the service in violation of any law;
- not attempting to disrupt the information security of any computer network -- such as internet use -- or end user;
- not posting commercial messages to usenet groups without prior permission;
- not sending junk email messages or spam to anyone who doesn't want to receive them;
- not attempting to mail bomb a site in order to flood the server;
- not attempting to steal intellectual property from the vendor;
- requiring users to report any attempt to break into their account;
- acknowledging that disciplinary action may be imposed if the AUP is violated; and
- noting that the AUP complies with applicable law as applied IT and related issues and may be subject to periodic audits.
A disclaimer is often included in an AUP absolving the organization from responsibility for a data breach, malware or other issue. Statements about when a person is in violation of this policy and when law enforcement might be called in could also be included.
Examples of how AUPs are used
The following are examples of areas where an acceptable use policy could be helpful:
- Social media. An AUP sets parameters on how employees should use social media sites, often stipulating what should not be discussed about the company and its business.
- Internet and other system use. Policies usually cover whether an organization's computer systems can be used only for business purposes. They often stipulate whether these resources can be used for personal email or other electronic communications, shopping, playing computer games and gambling.
- Cybersecurity. An AUP sets rules related to an organization's IT security policies. These include rules around accessing restricted information; changing access data, such as passwords; opening questionable email attachments; using public Wi-Fi services; and using company approved authentication procedures.
- Non-employee users. Use policies set restrictions on how non-employees can use company information systems and network resources.
- Accessing private or confidential information. AUPs prevent users from unauthorized access to proprietary or confidential data and unauthorized use of that data.
- Bring your own device (BYOD). Many organizations allow or require employees to use personal devices for business purposes. However, with BYOD, an AUP is necessary to prevent security issues and misunderstandings about how these devices should be used.
Best practices to ensure AUPs are followed
Signing an acceptable use policy may be required as part of an employment contract. It often happens during the employee onboarding process or as needed with existing employees.
However, employees must be reminded periodically of their responsibility to understand and adhere to the rules spelled out in the AUP. Some best practices that help employees comply with these policies include the following:
- Work with the company legal department to ensure the AUP addresses issues properly.
- Have clearly written policies with minimal technical jargon or confusing legal terms.
- Provide training classes that emphasize the rules included in an AUP.
- Test employee knowledge, awareness and understanding of an AUP with periodic questionnaires.
- Ensure that AUP language is periodically reviewed and updated, especially when there is a major change in business operations, such as introducing a new product or a merger, or when an audit is conducted.
BYOD acceptable use policies are becoming common. Find out more about BYOD policy enforcement and creation.
