talent acquisition
What is talent acquisition?
Talent acquisition is the strategic process an organization uses to identify, recruit and hire the people it needs to achieve its business goals and optimize its processes. Companies analyze their long-term talent needs, identify and develop talent sources, and then execute the strategy by recruiting, evaluating and onboarding candidates. Talent acquisition is usually a function of the human resources (HR) department working in collaboration with talent acquisition specialists, with input from senior executives.
Talent acquisition is usually the first step in an organization's talent management strategy. Talent management is the process employers use to hire, deploy, train, evaluate, compensate and retain employees.
Why is talent acquisition important?
Talent acquisition is important because finding and hiring the right people is a crucial element of an organization's business plan and directly affects its success. Without the right employees, a business is likely to struggle with poor productivity, bad decision-making and unmotivated staff.
Talent acquisition is forward-thinking. Instead of simply hiring a candidate to fill an opening, a talent acquisition team considers the potential employee's possible career path in the organization and places a priority on employee retention. As a result, talent acquisition ensures the organization hires people who could eventually become managers and make other important contributions.
A good talent acquisition strategy begins by assessing candidates' skills and the value they would bring to an organization. It also involves consistent communication to foster positive experiences. This in turn makes candidates feel welcomed and valued once hired. Candidates who feel valued are likely to stay with an organization, reducing employee turnover and churn and ensuring more continuity and knowledge retention.
Talent acquisition vs. recruitment
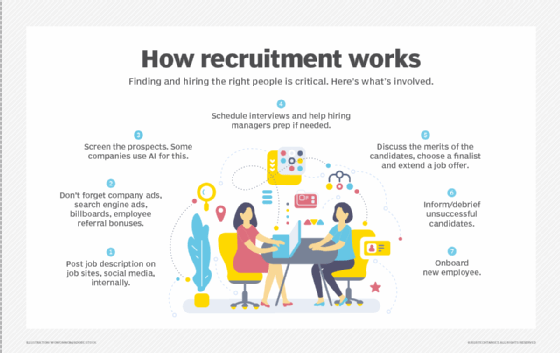
Recruitment is the biggest component of talent acquisition, and some organizations use the terms interchangeably. However, while talent acquisition and recruitment share a similar goal -- to fill open positions -- there are important differences. The biggest is that recruitment focuses on the present moment, while talent acquisition focuses mostly on the future.
Recruitment is invested in filling an open position as quickly as possible. Talent acquisition gives consideration to a company's goals and takes the time to find the candidate who best fits its business' needs. To gain this broader perspective, talent acquisition teams analyze a prospective employee's skills, how they fit with the company's culture, as well as their potential for future development to take on other roles in the company.
Other differences extend from this essential difference and include the following:
- Time investment. The best talent acquisition strategies usually require more time and planning than recruitment strategies.
- Analytics. Talent acquisition uses metrics and data analytics to improve the recruiting process and make informed hiring decisions.
- Roles and skills. Talent acquisition depends on hiring managers and recruiters understanding the different roles and segments in a company, as well as the skills and experience needed to succeed in each area. Recruiting pays less attention to these details.
- Job-specific hiring. Talent acquisition spends more time discovering the best places to find talent for specific jobs and initiatives and then building relationships with people in each area. Recruiting is more likely to use general-purpose hiring tools and spend less time on candidate relationship management.
While the recruitment process is mostly reactive and linear, talent acquisition is cyclical and strategic. Recruitment focuses on current needs, while talent acquisition focuses on creating a talent pipeline in anticipation of future needs.
How to create a talent acquisition strategy
Creating a talent acquisition strategy requires adding a strategic perspective to the recruiting process. The best steps to take when doing this include the following:
- Assessing organizational strategies. Examining the organizational business plan and goals, as well as departmental plans can provide insight into long-term talent and skill requirements. New lines of business, mergers and global expansion are major staffing drivers.
- Gathering feedback. Department managers, HR and senior executives are the best sources of experience and insight into business processes. They'll also expect to have input into the strategy.
- Defining the employer brand. Studying public perceptions of the brand through surveys and sites such as Glassdoor is a good way to evaluate the brand. Organizations should align the brand image with business goals and have it reflected in the recruiting process.
- Envisioning ideal candidates. With all this useful input, creating personas of the ideal candidates for each open position determines the ideal qualifications.
- Hiring with candidate engagement in mind. During the hiring process, candidates should be made to feel welcome at the organization. Positive points about the organization should be communicated up-front. For instance, emphasizing its inclusive vision can attract a diverse slate of candidates.
- Incorporating technology tools. Today's talent acquisition and recruiting software simplifies hiring. These tools can analyze large batches of candidate data, assess individual candidate's competencies and streamline onboarding.
Examples of talent acquisition strategies
Some approaches to talent acquisition that can be used in conjunction with an organization's internal strategy include the following:
Recruitment marketing
Recruitment marketing is a subset of marketing focused on promoting the organization as a desirable place to work, reinforcing the brand and gathering leads, including passive candidates who aren't actively looking. Employees participate in the marketing campaign through referrals, video testimonials and social media.
Source of hire (SoH)
The SoH is the place or way that employees in an organization are commonly hired. Knowing an organization's SoH for its top-performing employees can focus recruiting on the most productive sources, such as passive candidates, employee referrals and job boards. Often, an applicant tracking system is the best place to track and analyze SoH information.
Social media recruiting strategies
Besides helping to promote the employer brand, social media sites, such as LinkedIn and GitHub, serve as communication channels for posting jobs. They're also a good place to interact with candidates in the early stages of recruiting.
Talent acquisition tips and best practices
Experts advise doing the following to ensure an effective talent acquisition strategy:
- Create a strong brand. Make sure the company's website, culture and social media profiles appeal to both customers and potential job candidates. An appealing brand can attract top candidates.
- Make job descriptions as detailed as possible. Requirements should be specific, outlining exactly who the ideal candidate is. This approach increases the likelihood of finding a good match.
- Expand company outreach. Different skill sets and positions require talent acquisition team members to use different methods for sourcing talent. Instead of using general-purpose job sites like LinkedIn and Indeed, the company should consider specialized job boards, networking events and academic programs. Cultivating relationships with the top talent in each group builds the talent pool and job seekers' awareness of the brand, making it easier to attract new candidates in the future.
- Use data analytics. Providing a positive candidate experience and information to convince candidates to join the company is just as important as convincing consumers to buy products and services. Data analytics can uncover insights such as where the top talent in the company came from, whether certain questions are preventing candidates from completing applications and whether adding a video about the company culture will increase applications.
How to measure talent acquisition strategy success
Various metrics or key performance indicators are used to measure the success of an organization's talent acquisition process. Different organizations refer to them by different names, yet the information they convey is key. They include the following:
- Number of qualified candidates. The number of qualified candidates an organization attracts for an open role is a gauge of how effective its talent acquisition team is at reaching the right candidates.
- Acceptance rate. Talent acquisition teams can gauge how effective their job descriptions, outreach and subsequent communications are with candidates by looking at acceptance rates compared to the number of times candidates decline offers. Processes can then be refined to better engage candidates.
- Time to fill. The average time it takes to fill open positions at a company can reveal areas for improvement. Aspects of an organization's talent acquisition process that are taking longer than expected should be updated.
- Quality vs. cost per hire. Companies must hire qualified candidates for open positions that fit within their budgets. They can assess the quality of their hires to determine if the value the organization gets is equal to the associated costs.
- Ease of hiring. Regardless of whether a candidate is hired, it's important to monitor how smoothly the hiring process goes, looking for hangups and areas that present complications. Collecting candidates' feedback on the process can help identify areas for improvement.
- High turnover. How effectively a talent acquisition team conveys information about a position before a candidate is hired can determine whether that candidate stays with the company. If a high percentage of new hires leave within a year or two of joining an organization, the talent acquisition process might need to be adjusted.
Talent acquisition software
Talent acquisition is sometimes included as part of human capital management (HCM) suites. These tools automate core HR functions, such as payroll and benefits, and often have recruiting modules. However, applicant tracking systems are the real hub of recruitment and talent acquisition. They manage every step in the recruiting process, and provide analytics on candidate and employee data.
Many employers opt for talent management suites, such as Oracle Fusion Cloud HCM and SAP SuccessFactors. These types of software-as-a-service systems offer recruiting, performance management, compensation management, learning management and sometimes succession planning modules. More narrowly focused tools that provide talent acquisition and recruiting capabilities are also available.
Additionally, as artificial intelligence (AI) permeates various industries, more talent acquisition specialists are relying on software with AI-driven capabilities. Examples include existing software that incorporates more AI features over time and AI tools that screen candidates' data through analyses more efficiently than humans can.
Talent acquisition and job boards
Another talent acquisition option are job boards and job marketplaces where employers post open positions. Examples of these sorts of websites include Glassdoor, Indeed, Monster Worldwide, SimplyHired and ZipRecruiter. In addition to job postings, some of these sites also provide estimates of average annual salaries for various jobs and current and former employees' reviews of companies.
Major social media and technology players, such as LinkedIn and Google, also provide job-matching, business networking and job-search services. Talent acquisition specialists and recruiters increasingly use these platforms for social media recruiting.
Talent acquisition and onboarding
After a candidate is hired and becomes an employee, they go through a company's onboarding process, which includes steps like benefits enrollment, issuing of equipment, training on IT systems, and team introductions. Increasingly, onboarding is conducted online, especially for workers who will always work remotely. This has been crucial in the years following the COVID-19 pandemic.
Onboarding has become a universal component of talent management and talent acquisition software suites. A comprehensive talent acquisition platform will likely include an onboarding tool to streamline processes.
Talent acquisition specialist job description
A talent acquisition specialist is an HR professional who focuses on sourcing, identifying and hiring specific types of employees. Companies in competitive job markets that are growing and changing hire these professionals to deal with recruiting for in-demand jobs, such as tech, healthcare and finance.
Responsibilities of a talent acquisition specialist include the following:
- Building a qualified and diverse team of employees.
- Organizing and attending recruitment and networking events, conferences and job fairs.
- Anticipating each department's annual and quarterly hiring needs.
- Working with hiring managers and HR to determine staffing needs.
- Creating job descriptions and interview questions tailored to each job vacancy.
- Determining the selection criteria for open positions.
- Screening candidate resumes and applications.
- Providing managers with feedback on resumes and applications.
- Finding potential talent through online channels, such as LinkedIn, Facebook and professional networks.
- Planning the interview process and selection procedures that include everything from the initial screening interview to the job offer.
- Building relationships with potential candidates and previous applicants.
- Collaborating with management to ensure hiring procedures are ethical and fair.
- Performing introductory interviews with candidates to gauge their interest levels, personalities and salary expectations.
- Ensuring the onboarding process is a successful, positive experience for new employees.
Requirements for a talent acquisition specialist typically include a bachelor's degree in a field related to human resource management, ideally with a specialization in talent acquisition or management. These professionals usually need to have at least five years of previous HR experience.
The future of talent acquisition strategy
AI is increasingly being used in talent acquisition and recruiting. Its use coincides with the rise of data-driven AI. As talent acquisition data continues to expand exponentially, AI and machine learning tools are being used to analyze data and streamline recruiting.
An AI algorithm can screen candidates' resumes and other credentials to identify the best candidates faster than humans doing the same process manually. These algorithms can automate repetitive tasks like talent sourcing, which also speeds up hiring.
Organizations are also expected to emphasize strategic or cultural changes that are attractive to younger job candidates. These include workforce diversification efforts, better benefits and transparent salary policies.
As AI becomes more pervasive in the hiring process, it's important to be aware of the AI-based recruiting tools and software that are available.






