adiabatic cooling
What is adiabatic cooling?
Adiabatic cooling is the process of reducing heat through a change in air pressure caused by volume expansion. In data centers and other facilities, adiabatic processes have enabled free cooling methods, which use freely available natural phenomena to regulate temperature.
The principle of adiabatic cooling has been harnessed to develop cooling units that can save industry, and especially data centers, millions of liters of water annually. In the United States, older cooling towers use 1.5 quadrillion liters of water per year. And the water they use frequently ends up polluted.
How does adiabatic cooling work?
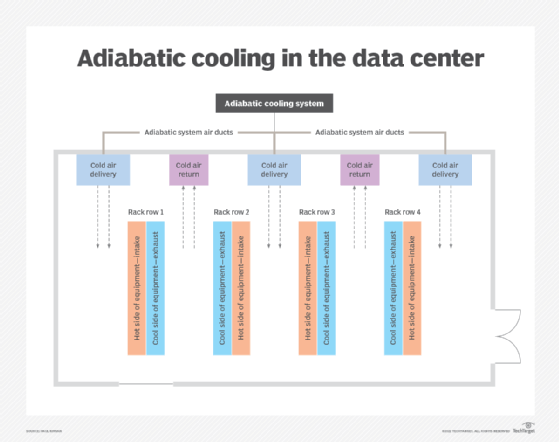
Adiabatic cooling systems are used with evaporative coolers. These systems are made up of a large fan that draws warm air through water-moistened pads. As the water in the pads evaporates, the air is chilled and pushed out to the data center room. The ambient air temperature can be controlled by adjusting the airflow of the cooler.
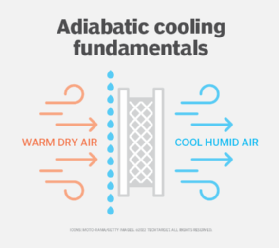
Conversely, adiabatic heating results when a cooler, less dense air mass sinks and increases in temperature due to the pressurized molecules becoming agitated and vibrating.
Adiabatic vs. evaporative cooling
Water use is the key difference between adiabatic and evaporative cooling systems.
Adiabatic cooling
Adiabatic cooling systems use less water than evaporative cooling systems. Adiabatic systems may use more energy, however. They also may take up more inside data center space. Adiabatic systems don't have cooling towers, which are usually positioned on rooftops.
Evaporative cooling
Evaporative cooling systems use more water than adiabatic systems. They also use chillers with cooling towers to cool water before it is circulated into a data center. Evaporative systems are more energy-efficient than adiabatic systems, and with their cooling tower, they may take up more total data center space.
Evaporative cooling systems, especially the cooling towers, have a history of serving as breeding grounds for Legionnaires' disease. Cooling towers must be regularly inspected and cleaned to prevent the growth of bacteria.
Data center cooling system evaluation
Heating, ventilation and air conditioning (HVAC) systems are essential to an efficient data center. Different kinds of HVAC systems are used in data centers, among them adiabatic cooling systems.
Each cooling system option has its pros and cons. When evaluating HVAC systems, look at the following factors:
- power consumption;
- space requirements;
- ductwork needed;
- water availability;
- temperature of available water;
- need for and location of cooling towers; and
- other plumbing requirements.
Adiabatic cooling in nature
In nature, adiabatic cooling is often associated with elevation. As seen with cloud formations, an air mass that is heated expands and decreases in density. Because it is less dense, it is lighter and rises above a higher-pressure air mass.
Once the air mass has reached areas with less dense air, it further expands, losing energy and cooling the air temperature in the process. When the cooling air crosses the dew point, moisture in the air accumulates as clouds. With enough moisture and cooling comes precipitation. The principles of adiabatic cooling are also applied to increase humidity in facilities.
Figuring out what sort of cooling system to use requires an assessment of data center cooling requirements. Several factors affect those requirements, including the equipment's heat output, floor area, facility design and electrical system power rating. Find out how to calculate these cooling requirements.
