ambient temperature
What is ambient temperature?
Ambient temperature is the air temperature of any object or environment where equipment is stored. The adjective ambient means "relating to the immediate surroundings." This value is also referred to as the ordinary temperature or the baseline temperature. It is important for system design and thermal analysis.
In a computing context, maintaining an appropriate ambient temperature is crucial to the proper functioning and longevity of computer equipment. In general, a safe ambient temperature range is between 60 degrees and 75 degrees Fahrenheit or 15 degrees and 24 degrees Celsius. The cooler end of that range is better. Higher ambient temperature readings or lower temperatures make it difficult for a computer's or data center's cooling system to maintain a safe operating temperature.
How to measure ambient temperature
A thermometer or temperature sensor is used to measure a room's or component's ambient temperature. To get the most accurate reading, the measuring device should be kept in the shade, at midheight of the room and in a well-ventilated space.
When measuring ambient temperature indoors, it is important to monitor the temperature values over the length of a day to pinpoint the maximum and minimum ambient temperature. Historical temperature averages are used to help determine outdoor environment ambient temperature.
Avoid the following three approaches when measuring ambient temperature:
- Don't put the sensor or thermometer in direct sunlight.
- Don't put the sensor too low as it absorbs excess heat from the ground. Five feet is a safe distance from the ground.
- Don't put the sensor above concrete, pavement or stone if measuring outside since these surfaces radiate heat toward the thermometer.
Importance of ambient temperature
Maintaining the correct ambient temperature is an important part of maximizing the life of devices and preventing malfunction and damage. Ambient temperature plays an important role in scenarios such as the following:
- analyzing components to make sure maximum and minimum temperatures do not affect functionality or use;
- controlling the temperature of an environment within an acceptable range;
- determining the energy efficiency or power usage effectiveness of a heating or cooling system;
- ensuring materials such as food and chemicals are stored safely;
- limiting the power dissipation, or power current, to a safe value; and
- ensuring a device's internal cooling system, such as a laptop fan, is working.
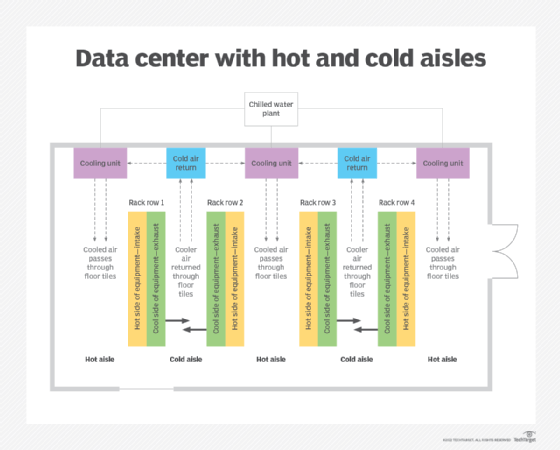
It is particularly important to monitor and control ambient temperature in the data center. Controlling airflow is the main way safe data center ambient temperatures are maintained.
Servers and other hardware that come into contact with hot, stagnant air cannot cool themselves efficiently and may malfunction or fail. Hot and cold aisle containment is a method used in many data centers to control ambient temperature, as well as other factors, like humidity.
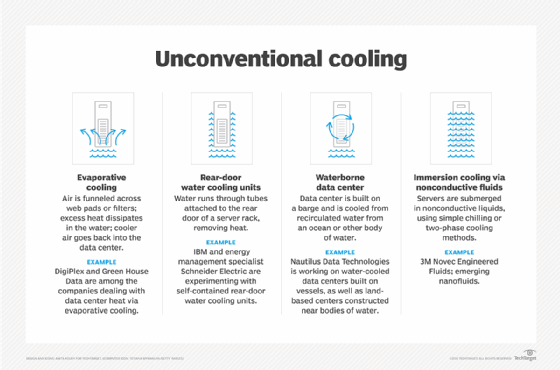
Liquid cooling is an alternative method used to maintain data center temperature.
The American Society of Heating, Refrigerating and Air-Conditioning Engineers maintains a list of humidity and temperature level standards for data centers. Adherence to these standards can help an organization ensure the longevity of its hardware.
Ambient vs. room temperature
The definition of ambient temperature is different from that of room temperature, and the terms are used in different contexts.
The term ambient temperature is an environment's actual air temperature. It is measured with a thermometer and is a precise, quantifiable value. If a computer must be stored in a room with an ambient temperature of 68 degrees Fahrenheit, that temperature refers to the room or controlled temperature of the air in the surrounding environment. It doesn't refer to the temperature of the object itself.
By contrast, room temperature refers to the range of temperatures that most people feel comfortable in. Room temperature is a qualitative, subjective measurement of the environment that describes the temperature of an object in the room. It is a more casual expression. Here is an example of how it's used in a sentence: "The water is room temperature, not too hot or too cold." The ambient temperature of an environment may vary greatly from its accepted room temperature, such as when the air conditioning malfunctions.
Another similar term is apparent temperature, which relates to how the current air temperature feels and doesn't refer directly to a quantifiable measure of temperature. Apparent temperature considers factors like relative humidity, wind chill and insulation. These affect the feeling of the temperature in the air, but they do not affect the actual ambient temperature. The factors that affect apparent temperature can be equally as important as the ambient air temperature in data centers and internet of things implementations.
Learn how to calculate data center cooling requirements and what factors to consider.






