social engineering
What is social engineering?
Social engineering is an attack vector that relies heavily on human interaction and often involves manipulating people into breaking normal security procedures and best practices to gain unauthorized access to systems, networks or physical locations or for financial gain.
Threat actors use social engineering techniques to conceal their true identities and motives, presenting themselves as trusted individuals or information sources. The objective is to influence, manipulate or trick users into releasing sensitive information or access within an organization. Many social engineering exploits rely on people's willingness to be helpful or fear of punishment. For example, the attacker might pretend to be a co-worker who has some kind of urgent problem that requires access to additional network resources.
Social engineering is a popular tactic among attackers because it is often easier to exploit people than it is to find a network or software vulnerability. Hackers will often use social engineering tactics as a first step in a larger campaign to infiltrate a system or network and steal sensitive data or disperse malware.

How does social engineering work?
Social engineers use a variety of tactics to perform attacks.
The first step in most social engineering attacks is for the attacker to perform research and reconnaissance on the target. If the target is an enterprise, for instance, the hacker may gather intelligence on the organizational structure, internal operations, common lingo used within the industry and possible business partners, among other information.
One common tactic of social engineers is to focus on the behaviors and patterns of employees who have low-level but initial access, such as a security guard or receptionist; attackers can scan social media profiles for personal information and study their behavior online and in person.
From there, the social engineer can design an attack based on the information collected and exploit the weakness uncovered during the reconnaissance phase.
If the attack is successful, the attacker gains access to confidential information, such as Social Security numbers and credit card or bank account information; makes money off the targets; or gains access to protected systems or networks.
Types of social engineering attacks
Popular types of social engineering attacks include the following techniques:
- Baiting. An attacker leaves a malware-infected physical device, such as a Universal Serial Bus flash drive, in a place it is sure to be found. The target then picks up the device and inserts it into their computer, unintentionally installing the malware.
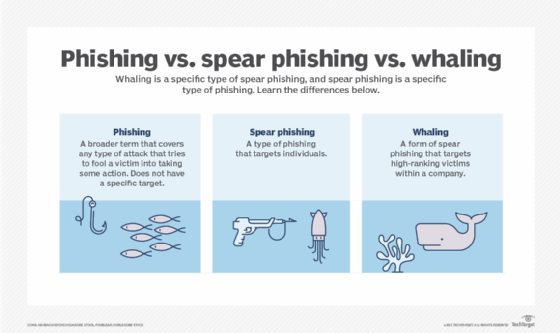
- Phishing. When a malicious party sends a fraudulent email disguised as a legitimate email, often purporting to be from a trusted source. The message is meant to trick the recipient into sharing financial or personal information or clicking on a link that installs malware.
- Spear phishing. This is like phishing, but the attack is tailored for a specific individual or organization.
- Vishing. Also known as voice phishing, vishing involves the use of social engineering over the phone to gather financial or personal information from the target.
- Whaling. A specific type of phishing attack, a whaling attack targets high-profile employees, such as the chief financial officer or chief executive officer, to trick the targeted employee into disclosing sensitive information.
![phishing vs. spear phishing vs. whaling]()
These three types of phishing attacks fall under the wider umbrella of social engineering. - Pretexting. One party lies to another to gain access to privileged data. For example, a pretexting scam could involve an attacker who pretends to need financial or personal data to confirm the identity of the recipient.
- Scareware. This involves tricking the victim into thinking their computer is infected with malware or has inadvertently downloaded illegal content. The attacker then offers the victim a solution that will fix the bogus problem; in reality, the victim is simply tricked into downloading and installing the attacker's malware.
- Watering hole. The attacker attempts to compromise a specific group of people by infecting websites they are known to visit and trust with the goal of gaining network access.
- Diversion theft. In this type of attack, social engineers trick a delivery or courier company into going to the wrong pickup or drop-off location, thus intercepting the transaction.
- Quid pro quo. This is an attack in which the social engineer pretends to provide something in exchange for the target's information or assistance. For instance, a hacker calls a selection of random numbers within an organization and pretends to be a technical support specialist responding to a ticket. Eventually, the hacker will find someone with a legitimate tech issue whom they will then pretend to help. Through this interaction, the hacker can have the target type in the commands to launch malware or can collect password information.
- Honey trap. In this attack, the social engineer pretends to be an attractive person to interact with a person online, fake an online relationship and gather sensitive information through that relationship.
- Tailgating. Sometimes called piggybacking, tailgating is when a hacker walks into a secured building by following someone with an authorized access card. This attack presumes the person with legitimate access to the building is courteous enough to hold the door open for the person behind them, assuming they are allowed to be there.
- Rogue security software. This is a type of malware that tricks targets into paying for the fake removal of malware.
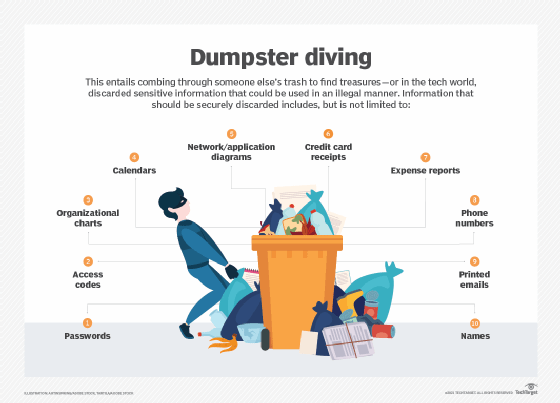
- Dumpster diving. This is a social engineering attack whereby a person searches a company's trash to find information, such as passwords or access codes written on sticky notes or scraps of paper, that could be used to infiltrate the organization's network.
- Pharming. With this type of online fraud, a cybercriminal installs malicious code on a computer or server that automatically directs the user to a fake website, where the user may be tricked into providing personal information.
Examples of social engineering attacks
Perhaps the most famous example of a social engineering attack comes from the legendary Trojan War in which the Greeks were able to sneak into the city of Troy and win the war by hiding inside a giant wooden horse that was presented to the Trojan army as a symbol of peace.
In more modern times, Frank Abagnale is considered one of the foremost experts in social engineering techniques. In the 1960s, he used various tactics to impersonate at least eight people, including an airline pilot, a doctor and a lawyer. Abagnale was also a check forger during this time. After his incarceration, he became a security consultant for the Federal Bureau of Investigation and started his own financial fraud consultancy. His experiences as a young con man were made famous in his best-selling book Catch Me If You Can and the movie adaptation from Oscar-winning director Steven Spielberg.
Once known as "the world's most wanted hacker," Kevin Mitnick persuaded a Motorola worker to give him the source code for the MicroTAC Ultra Lite, the company's new flip phone. It was 1992, and Mitnick, who was on the run from police, was living in Denver under an assumed name. At the time, he was concerned about being tracked by the federal government. To conceal his location from authorities, Mitnick used the source code to hack the Motorola MicroTAC Ultra Lite and then sought to change the phone's identifying data or turn off the ability for cellphone towers to connect to the phone.
To obtain the source code for the device, Mitnick called Motorola and was connected to the department working on it. He then convinced a Motorola employee that he was a colleague and persuaded that worker to send him the source code. Mitnick was ultimately arrested and served five years for hacking. Today, he is a multimillionaire and the author of a number of books on hacking and security. A sought-after speaker, Mitnick also runs cybersecurity company Mitnick Security.
A more recent example of a successful social engineering attack was the 2011 data breach of security company RSA. An attacker sent two different phishing emails over two days to small groups of RSA employees. The emails had the subject line "2011 Recruitment Plan" and contained an Excel file attachment. The spreadsheet contained malicious code that, once the file was opened, installed a backdoor through an Adobe Flash vulnerability. While it was never made clear exactly what information was stolen, if any, RSA's SecurID two-factor authentication (2FA) system was compromised, and the company spent approximately $66 million recovering from the attack.
In 2013, the Syrian Electronic Army was able to access the Associated Press' (AP) Twitter account by including a malicious link in a phishing email. The email was sent to AP employees under the guise of being from a fellow employee. The hackers then tweeted a fake news story from AP's account that said two explosions had gone off in the White House and then-President Barack Obama had been injured. This garnered such a significant reaction that the Dow Jones Industrial Average dropped 150 points in under 5 minutes.
Also in 2013, a phishing scam led to the massive data breach of Target. A phishing email was sent to a heating, ventilation and air conditioning subcontractor that was one of Target's business partners. The email contained the Citadel Trojan, which enabled attackers to penetrate Target's point-of-sale systems and steal the information of 40 million customer credit and debit cards. That same year, the U.S. Department of Labor was targeted by a watering hole attack, and its websites were infected with malware through a vulnerability in Internet Explorer that installed a remote access Trojan called Poison Ivy.
In 2015, cybercriminals gained access to the personal AOL email account of John Brennan, then the director of the Central Intelligence Agency. One of the hackers explained to media outlets how he used social engineering techniques to pose as a Verizon technician and request information about Brennan's account with Verizon. Once the hackers obtained Brennan's Verizon account details, they contacted AOL and used the information to correctly answer security questions for Brennan's email account.
Preventing social engineering
There are a number of strategies companies can take to prevent social engineering attacks, including the following:
- Make sure information technology departments are regularly carrying out penetration testing that uses social engineering techniques. This will help administrators learn which types of users pose the most risk for specific types of attacks, while also identifying which employees require additional training.
- Start a security awareness training program, which can go a long way toward preventing social engineering attacks. If users know what social engineering attacks look like, they will be less likely to become victims.
- Implement secure email and web gateways to scan emails for malicious links and filter them out, thus reducing the likelihood that a staff member will click on one.
- Keep antimalware and antivirus software up to date to help prevent malware in phishing emails from installing itself.
- Stay up to date with software and firmware patches on endpoints.
![top cybersecurity training topics]()
Phishing, social engineering, password hygiene and secure remote work practices are essential cybersecurity training topics. - Keep track of staff members who handle sensitive information, and enable advanced authentication measures for them.
- Implement 2FA to access key accounts, e.g., a confirmation code via text message or voice recognition.
- Ensure employees don't reuse the same passwords for personal and work accounts. If a hacker perpetrating a social engineering attack gets the password for an employee's social media account, the hacker could also gain access to the employee's work accounts.
- Implement spam filters to determine which emails are likely to be spam. A spam filter might have a blacklist of suspicious Internet Protocol addresses or sender IDs, or they might detect suspicious files or links, as well as analyze the content of emails to determine which may be fake.