location-based service (LBS)
What is a location-based service (LBS)?
A location-based service (LBS) is a software service for mobile device applications that requires knowledge about where the mobile device is geographically located. The application collects geodata, which is data gathered in Real Time using one or more location tracking technologies.
Location-based services integrate data from various resources, including Global Positioning System (GPS) satellites, cellular tower pings and short-range positioning beacons, to provide services based on the user's geographical location. Although location-based technologies have been commercially available for almost two decades, the applications and services that use geodata have recently become mainstream, thanks to the widespread use of Android and Apple smartphones and tablets.
What are the types and components required to operate location-based services?
Location-based services can be broken into the following distinct categories:
- Pull. The application user initiates the location-based service processes. One example of a query-based location-based service is a user checking a mobile map application, such as Waze, to find the nearest automated teller machine. Some location-based services also enable users to check in to restaurants, concerts or sporting events using apps such as Foursquare, Yelp or Google Maps.
- Push. The application initiates the location process based on a trigger or at regular intervals. The application then presents the user or device with relevant information based on their geographic location. Proximity-based marketing is a push-based location-based service example. Here, a user is sent an advertisement or coupon after the application proactively identifies that person as being near a specific retail outlet.
For location-based services to operate, the following four basic components are required:
- an application that uses location-based services;
- a positioning mechanism to collect geodata;
- a mobile network to transmit or receive data; and
- analytics software running on a remote server to compute and deliver relevant data to the user based on geographic location.
By law, location-based services must be permission-based, so the end user must opt in to the service in order to use it. In most cases, this means the user turns on the location-based service application and accepts a request to enable the service to know the device's location. For example, a user can enable or disable Apple's iPhone Location Services for a specific app, as well as specify whether the application can pull geodata at any time, only when the app is in use or ask each time a location is needed. This process is similar with Android devices as well.
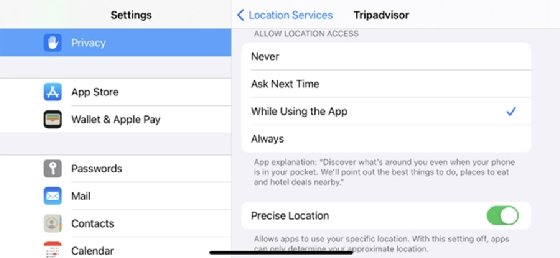
What types of technologies are used for tracking location?
Depending on the need, mobile device hardware type and available supporting technologies, the following tracking mechanisms are often used for location-based services:
- GPS
- Wi-Fi access point triangulation
- cellular tower triangulation
- Bluetooth beacons
- radio frequency identification
What are location-based services used for?
There are numerous location-based services, including Waze, Google Maps, Lyft, Uber, GasBuddy and WhatsApp. While the types and benefits of these services are growing, common uses include the following:
- navigation and travel information, including real-time traffic notifications;
- store and service locators;
- fleet and mobile workforce management tracking;
- inventory monitoring;
- anti-theft prevention;
- fraud prevention using a location-based service to match a customer's location to a credit card transaction;
- proximity-based marketing;
- roadside assistance;
- social networking;
- surveillance; and
- augmented reality.
What are the risks of using location-based services?
While there are clear benefits and relevant use cases for location-based services, there are some risks users must understand. In the recent past, application creators, mobile device developers and mobile network operators have been accused of tracking devices and users without their consent.
While the industry seems to be moving in the right direction, this topic brings up serious privacy risks for those who are not fully informed or tech-savvy. Location tracking data in the wrong hands can lead to situations where criminals, thieves or stalkers could use this information to assist with their crimes. And, on a lesser scale, the data can be used for unsolicited and unwanted targeted marketing or advertising campaigns that many find overly intrusive.
To reduce the security risks of using location-based services, it is wise to limit when applications are authorized to track users. This includes turning off or limiting when an application can track and verifying that the application owner will not use or sell location data in a way that could harm the end user.
Learn what location accuracy means for internet of things application requirements.






