application migration
What is application migration?
Application migration is the process of moving an application program from one environment to another. Examples include migration from an on-premises enterprise server to a cloud provider's environment or from one cloud environment to another.
Migrating an application can be complicated because there are often differences between the original and target environments. Furthermore, applications -- even cloud applications -- are not typically designed to be portable. Applications created on various cloud development platforms, such as Microsoft Azure and Google App Engine, are usually designed to run on the platforms they were developed on. Other elements, such as operating systems, management tools, the networking architecture, the storage system and the virtual machine (VM) configuration, can all differ from those in the environment where the application was developed or deployed.
A successful application migration may require middleware products to bridge any gaps between technologies.
There are several ways to go about application migration:
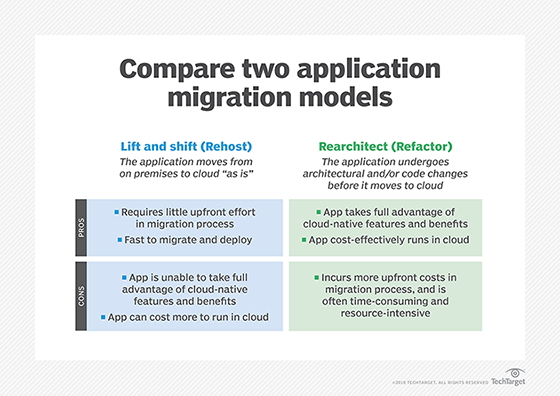
- Rehost. Rehosting, or lift-and-shift, refers to the strategy in which an organization moves the application without making any changes. The long-term costs of this can be higher than other options.
- Refactor. Also known as rearchitect, this strategy calls for an application to undergo significant changes so that it will scale within a cloud environment.
- Replatform. An application undergoes minor tweaks so it can benefit from cloud architecture. This revision can look like upgrading the application, containerizing the application or changing the operating systems.
- Rebuild. During a rebuild, developers rewrite an application specifically for the cloud. This option is also called a forklift replacement of a whole application, which is usually disruptive.
- Retire/replace. In some instances, it is in an organization's best interest to decommission the application or choose a new one.
Application migration best practices
To help ensure a successful application migration, organizations should follow these best practices:
Perform an assessment. The foundation of any migration project is an assessment of an enterprises application portfolio, including any legacy systems or applications. User must also have an understanding of the ecosystem surrounding the applications, including the configurations of the physical and virtual servers, network topology, current support and data dependencies, security and compliance.
Involve the business as soon as possible. Ensure all the relevant business units take part in planning the migration and aware of how it might affect them and existing business processes. Clear communication is key.
Map out a migration strategy. Identify the business reasons and use cases for migrating to the cloud. Decide whether to migrate in phases or maybe start with the least business-critical workloads to gain experience and then move to more mission-critical applications.
Develop a cloud governance framework. This should consist of clear, policy-based rules to help an organization prepare for a secure cloud adoption, including structures, roles, responsibilities, plans, objectives and a decision framework.
Train staff as soon as possible. Set up a series of training sessions to get employees across different teams and business units up to speed on cloud concepts.
Manage software licensing properly. Document all enterprise applications, closely studying their licensing as it relates to cloud computing. If necessary, check with vendors to determine if existing licenses can be updated so the applications can be used in the cloud.
Implement automation. To improve the overall efficiency of the migration and minimize disruption to the business, organizations should automate repeated patterns where possible. This will speed up the migration process, as well as lower risk and save money. The phased cloud migration approach and automation can work together, i.e., identify repeated patterns over time that can be automated in future migration phases.
Test, test and retest. An enterprise that doesn't have a proper testing plan in place won't have a successful migration. Star talking about testing on the first day of the assessment.
Challenges of a cloud migration
While there are several benefits to migrating applications to the cloud, including improved operational efficiently, faster deployment times and lower costs, there are still some challenges that organizations face, such as the following:
Lacking a defined strategy. For successful cloud adoption and implementation, organizations need an end-to-end migration plan that doesn't include any shortcuts. As some data centers and applications will be more difficult to migrate than others, a one-size-fits-all strategy won't work.
Security and compliance. When moving to the cloud, enterprises must ensure that the data they move to the cloud is secure. However, they also must be sure they comply with all the relevant industry and government regulations.
Failing to properly calculate costs. Organizations must accurately evaluate the costs of their migrations and operations in advance to help them save money. Some things to take into consideration include capital and operational expenditures as well as the cost of the migration.
Skills gap. One of the main obstacles to moving applications to the cloud is finding people who have the skills to manage a migration effectively. Enterprises that don't have the resources to hire cloud migration talent should cultivate these skills internally or look for vendors that offer dedicated people to support successful migrations. These individuals can also help train organizations' employees in the necessary cloud skills.
Application migration tools
There are several application migration services and tools on the market, including the following:
- AWS. Amazon offers a variety of cloud migration services, including AWS Database Migration Service and AWS Migration Hub. Most services are free for AWS customers. However, the tools only support AWS.
- Azure. Microsoft offers free Azure migration tools, including Azure Migrate, to assess and migrate workloads, and free Azure Cost Management to optimize costs to help organizations move to its Azure public cloud computing platform. However, Microsoft doesn't support any other cloud vendors.
- Google Cloud. Google has various tools to migration, such as Migration Center which is a unified platform for migration and modernization. It also includes open source and container migration options.
- PlateSpin Migrate. PlateSpin Migrate is a third-party option that offers a comprehensive and highly scalable cloud migration product that supports multiple clouds and includes advanced security features, such as role-based permissions.






