biotechnology (biotech)
What is biotechnology?
Biotechnology is the use of biology to develop new products, methods and organisms intended to improve human health and society. Biotechnology, often referred to as biotech, has existed since the beginning of civilization with the domestication of plants, animals and the discovery of fermentation.
Early applications of biotech led to the development of products such as bread and vaccines. However, the discipline has evolved significantly over the last century in ways that manipulate the genetic structures and biomolecular processes of living organisms. The modern practice of biotechnology draws from various disciplines of science and technology, including the following:
- molecular biology
- chemistry
- bionics
- genetic engineering
- genomics
- nanotechnology
- informatics
This approach has resulted in innovations and breakthroughs in the following areas:
- medicines and therapeutics that prevent and treat disease;
- medical diagnostics such as pregnancy tests;
- biofuels that are sustainable, reducing waste and pollution; and
- genetically modified organisms (GMOs) that lead to more efficient and cost-effective agriculture.
Modern applications of biotechnology work most often through genetic engineering, which is also known as recombinant DNA technology. Genetic engineering works by modifying or interacting with the genetic cell structures. Every cell in an animal or plant contains genes that produce proteins. It's those proteins that determine the characteristics of the organism.
By modifying or interacting with genes, scientists can strengthen the characteristics of an organism or create an entirely new organism. These modified and new organisms may be beneficial to humans, such as crops with higher yields or increased resistance to drought. Genetic engineering also enables the genetic modification and cloning of animals, two controversial developments.
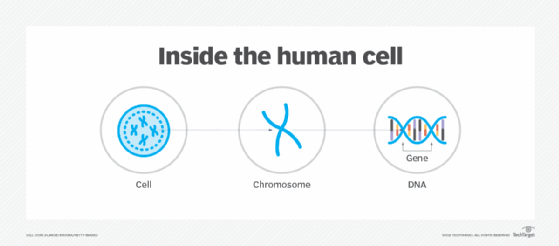
History of biotechnology
Biotechnology began at least 6,000 years ago with the agricultural revolution. This early era was characterized by exploiting living organisms in their natural forms or modifying their genetic makeup through selective breeding.
Around the same time, humans learned to harness the biological process of fermentation to produce bread, alcohol and cheese. People also began changing the genetic makeup of domesticated plants and animals through selective breeding.
Selective breeding works by breeding parents with desirable characteristics to express or eliminate certain genetic characteristics in their offspring. Over time, species that are selectively bred evolve to be different from their wild ancestors. For instance, during the agricultural revolution, wheat was selectively bred to stay on its stem when harvested instead of falling to the ground like wild wheat. Dogs were selectively bred to be more docile than their wolf ancestors.
However, biotech methods such as selective breeding can take a long time to show changes in species. Biotechnology remained limited to these slow, agricultural methods until the 19th century when biologist Gregor Mendel discovered the basic principles of heredity and genetics.
Also, during that era, scientists Louis Pasteur and Joseph Lister discovered the microbial processes of fermentation. This laid the foundation for biotechnology industries where scientists interact more directly with the molecular and genetic processes of organisms.
Based on the work of these scientists, genetic engineering was developed in 1973. This method is the foundation of modern biotechnology practices and recent advances. It enabled the first direct manipulation of plant and animal genomes, which is the complete set of genes present in a cell.
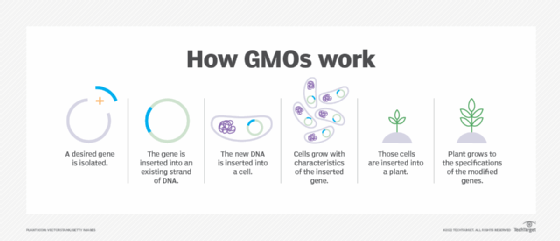
Over the last 100 hundred years or so, biotechnology emerged with the following discoveries and advancements:
1919. Hungarian scientist Karl Ereky coins the term biotechnology.
1928. Alexander Fleming discovers penicillin, the first true antibiotic.
1943. Oswald Avery proves DNA carries genetic information.
1953. James Watson and Francis Crick discover the double helix structure of DNA.
1960s. Insulin is synthesized to fight diabetes, and vaccines for measles, mumps and rubella are developed.
1969. The first synthesis of an enzyme in vitro, or outside the body, is conducted.
1973. Herbert Boyer and Stanley Cohen develop genetic engineering with the first insertion of DNA from one bacteria into another.
1980s. The first biotech drugs to treat cancer are developed.
1890. The United States Supreme Court rules that a "live human-made microorganism is patentable subject matter," meaning GMOs can be intellectual property.
1982. A biotech-developed form of insulin becomes the first genetically engineered product approved by the U.S. Food and Drug Administration (FDA).
1983. The first genetically modified plant is introduced.
1993. GMOs are introduced into agriculture with the FDA approval of growth hormones that produce more milk in cows.
1997. The first mammal is cloned.
1998. The first draft of the Human Genome Project is created, giving scientists access to over 30,000 human genes and facilitating research on treatment of diseases such as cancer and Alzheimer's.
2010. The first synthetic cell is created.
2013. The first bionic eye is created.
2020. MRNA vaccine and monoclonal antibody technology is used to treat the SARS-CoV-2 virus.
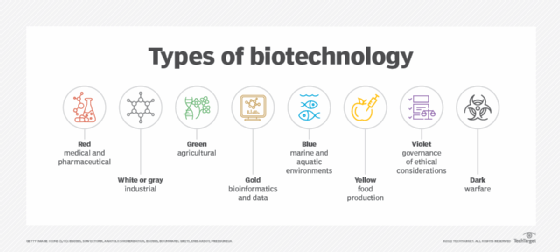
Types of biotechnology
The science of biotechnology is broken down into subdisciplines that are color-coded based on common uses and applications.
- Red biotechnology involves medical processes, such as using organisms to produce new drugs and stem cells to regenerate damaged human tissues and grow and regrow entire organs.
- White or gray refers to industrial processes, such as the development of new chemicals or new biofuels for vehicles.
- Green covers agricultural processes, such as producing pest-resistant crops, disease-resistant animals and environmentally friendly agricultural practices.
- Gold, also known as bioinformatics, is a cross between biological processes and informatics. It refers to the methods healthcare workers use to gather, store and analyze biological data to treat patients.
- Blue encompasses processes in marine and aquatic environments, such as converting aquatic biomass into fuels and pharmaceuticals.
- Yellow refers to processes that aid food production, the most popular application being the fermentation of alcohol and cheese.
- Violet ensures the practice of biotechnology is in compliance with laws and ethical standards governing each field.
- Dark is the use of biotechnology for weapons or warfare.
Uses and applications of biotechnology
The use and commercialization of modern biotechnology often fall into four main fields: environment, medicine, industry and agriculture.
Environment
The aim of environmental biotechnology is to develop sustainable environmental practices that reduce pollution and waste. The following are examples of environmental biotech:
- Phytoremediation uses genetically engineered microorganisms to purify soils of heavy metals and other pollutants.
- Bioremediation introduces microorganisms into waste sites in order to organically break down nonrecyclable waste.
- Plastic-eating bacteria breaks down waste such as plastic in soils and water.
- GMO foods stay fresher longer and reduce food waste.
- Genetic restoration attempts to restore endangered species such as the American chestnut tree.
- Cover-crops such as corn are used as biofuels, replacing traditional fuel sources that produce greenhouse gas emissions when extracted and used.

Medicine
Medical biotechnology, also known as biopharma, aims to fight and prevent disease and improve healthcare. Biotechnology and biomedical research are the basis of the modern pharmaceutical industry. Uses include the following:
- stem cell research that helps replace or repair dead or defective cells;
- antibiotics development;
- gene therapies for diseases such as leukemia;
- research into dangerous pathogens and the antibodies that fight them;
- 3D printing or growing of organs and bones in labs; and
- mRNA vaccines, monoclonal antibody treatments and research for COVID-19.
Industry
Industrial biotechnology involves using microorganisms to produce industrial goods. Examples include the following:
- fermentation and the use of enzymes and microbes to streamline chemical manufacturing and reduce operational costs and chemical emissions;
- biofuels that use renewable crops such as corn to produce combustible fuel instead of natural, nonrenewable fossil fuel resources, such as petroleum and oil; and
- biodegradable garments and textiles made from the proteins of living organisms, such as the silk proteins of spiders.
Agriculture
Agricultural biotechnology genetically engineers plants and animals to produce more efficient agriculture, increase nutritional value and reduce food insecurity. Some examples of agricultural biotechnology are the following:
- biologically produced pesticides and herbicides that are less harmful to humans than chemical ones;
- drought-resistant crops;
- minimal space-resilient crops;
- meat grown in labs or using 3D printers;
- gluten-free grains friendly to sufferers of celiac;
- selective breeding that produces healthier, bigger livestock and crops; and
- nutrient supplementation that infuses food with added nutrients to improve diets and medical treatments.
What are the advantages of biotechnology?
Biotechnology production offers a variety of advantages and solutions to critical problems. The main ones are the following:
- reducing pollution and waste to reverse catastrophic climate change and environmental damage;
- creating healthier, stronger and more-sustainable food products that boost nutrition and combat food insecurity;
- treating diseases in children before they are born by altering their genomes;
- designing medicine to boost the health and longevity of people, animals and plants; and
- cutting costs of farm supplies such as pesticides, while increasing crop yields and profits.
What are the disadvantages of biotechnology?
Biotechnology also comes with disadvantages and misuse. The main disadvantages include the following:
- Biological warfare. The potential exists for the development of pathogens and epidemics that could be used in a conflict zone to infect populations.
- Decrease in biodiversity. Monocropping or the farming of only a small number of genetically engineered crops could shrink the natural gene pool of species and make them less resilient and adaptable to sudden changes in environment.
- Loss of soil fertility. Bio-enhanced plants require more nutrients from soil and yield more crops. This can drain soil of fertile nutrients, devastate farmland and require the use of environmentally harmful fertilizers to make up for the nutrient shortfall.
- High costs. Biotechnology products often cost more than traditional products and have the potential to raise pricing structures in various industries.
- Ethical considerations. Gene manipulation raises a range of ethical issues, such as the genetic engineering of humans.
- Safety questions. Various groups have raised safety concerns about the health risks of GMOs and biotech-related medical developments, such as mRNA vaccines.
Concerns about biotechnology's disadvantages have led to efforts to enact legislation restricting or banning certain processes or programs, such as human cloning, GMOs and embryonic stem-cell research.
Biotechnology is critical to environmentally sound advancements in agriculture. Learn more about how technology like artificial intelligence (AI) is improving the food industry.