circuit
What is a circuit?
In electronics, a circuit is a complete circular path that electricity flows through. A simple circuit consists of a current source, conductors and a load. The term circuit can be used in a general sense to refer to any fixed path that electricity, data or a signal can travel through.
How electronic circuits work
In an electronic circuit, electrons come out of the power source, travel along conductors, go through a load to perform work and are finally returned to the source. It is called a circuit because of the circular path that the electrons flow through. The relationship between the electrical flow and load is described in Ohm's Law. In a circuit, the electrons travel from the negative side of the power supply to the positive side.
Most modern electronic devices use printed circuit bords that have circuit traces that act as the conductors. The circuit boards will also contain all the connectors and other components needed for the circuit to perform the needed job.
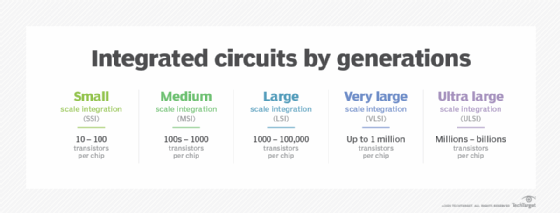
Circuits can be miniaturized and printed on a substrate in an integrated circuit (IC). The IC will contain all the needed circuit traces, capacitors, transistor and other parts needed to do a job. In most devices an IC will be put on a circuit board and then connected to a power supply.
An open circuit is when the path for electricity is broken so that it cannot flow in a complete circuit. In an open circuit, no electricity can flow and no work can be done.
A short circuit is when there is an electrical path directly from the output to the input of a power supply. Since electricity wants to find the shortest path, or path of least resistance, all of the current will go through the short, bypassing the load. This will cause the circuit to no longer work properly and can damage the power supply, cause parts to overheat and potentially start a fire. To protect against short circuits causing damage, a fuse or circuit breaker is placed in the circuit to break the electric path if too much current is drawn by a short circuit.
Circuits in networking and telecommunications
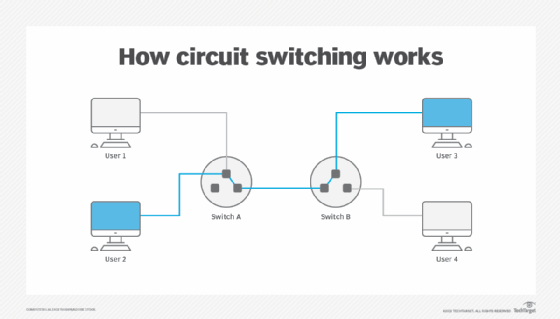
In telecommunications, a circuit is the complete path that a message takes to go from the sender to the receiver and back again. Historically, for telegraphs and early telephone systems to work, they required a complete electrical path between the sender and receiver. This was accomplished with long wire runs that could be connected as needed at switchboards.
In telephony, each voice connection is a circuit and the number of simultaneous calls, or circuits, is used to rate telephone service capacity. Circuit switched networks create physical circuit connections automatically. In switched fiber networks instead of an electrical circuit being connected, the path that the light travels is changed.
Even though a direct electrical connection is no longer needed in modern networks, the term circuit is still used. In these contexts, the circuit can be the routing that a data packet takes as it traverses a network. Virtual circuits can be created in a frame relay network, such as in ethernet or the internet, to define dedicated paths that certain packets should follow. A permanent virtual circuit (PVC) is a logical packet routing path through another network established for an indefinite period.
See also: monostable circuit, crosstalk, microcontroller, optoisolator, conductance, phase-locked loop, international private leased circuit, electromagnetic interference, impedance, apparent power, propagation delay and backplane.
