
e-commerce
What is e-commerce?
E-commerce (electronic commerce) is the buying and selling of goods and services, or the transmitting of funds or data, over an electronic network, primarily the internet. These e-commerce transactions typically fall within four types: business-to-business (B2B), business-to-consumer (B2C), consumer-to-consumer or consumer-to-business.
The terms e-commerce and e-business are often used interchangeably. The term e-tail is also sometimes used in reference to the transactional processes that make up online retail shopping.
In the last two decades, e-commerce platforms -- such as Amazon and eBay -- have contributed to substantial growth in online retail. In 2011, e-commerce accounted for 5% of total retail sales according to the U.S. Census Bureau. By Q2 2020, after the start of the COVID-19 pandemic, e-commerce accounted for 16.5% of retail sales. Since then, it has fallen slightly to about 15% as physical stores reopened.
How does e-commerce work?
E-commerce is powered by the internet. Customers use their own devices to access online stores. They can browse products and services those stores offer and place orders.
This article is part of
The evolving CIO role: From IT operator to business strategist
As an order is placed, the customer's web browser communicates back and forth with the server hosting the e-commerce website. Data pertaining to the order is relayed to a central computer known as the order manager. The data is then forwarded to databases that manage inventory levels; a merchant system that manages payment information using payment processing applications, such as PayPal; and a bank computer. Finally, it circles back to the order manager. This ensures store inventory and customer funds are sufficient for the order to be processed.
After the order is validated, the order manager notifies the store's web server. It displays a message notifying the customer that their order has been processed. The order manager then sends order data to the warehouse or fulfillment department, letting it know the product or service can be dispatched to the customer. At this point, tangible and digital products are sent to the customer, or access to a service is granted.
Platforms that host e-commerce transactions include online marketplaces that sellers sign up for, such as Amazon; software as a service (SaaS) tools that let customers rent online store infrastructures; and open source tools that companies manage using their in-house developers.
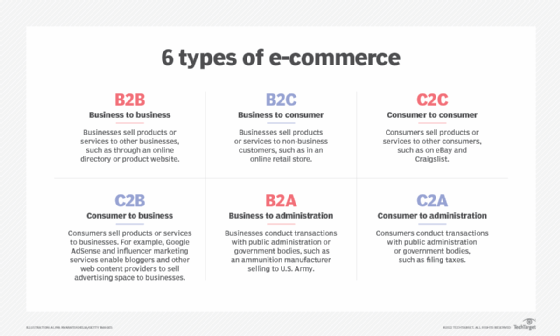
Types of e-commerce
The main types of e-commerce business models include the following:
B2B. This refers to the electronic exchange of products, services or information between businesses rather than between businesses and consumers. Examples include online directories and exchange websites that let businesses search for products, services or information and initiate online transactions through e-procurement interfaces.
B2C. These transactions are when businesses sell products, services or information to consumers. There are typically intermediaries or middlemen that handle shipping, delivery and customer service, however. The term was popular during the dot-com boom of the late 1990s, when online retailers and sellers of goods were a novelty.
Today, there are innumerable virtual stores and malls on the internet selling all types of consumer goods. Amazon is the most recognized among these sites, dominating the B2C market.
Direct-to-consumer (D2C). This is where a business that manufactures or produces goods and services sells directly to consumers online without any middlemen or distributors involved, in contrast to B2C e-commerce.
Consumer-to-consumer (C2C). This is a type of e-commerce in which consumers trade products, services and information with each other online. These transactions are generally conducted through a third party that provides an online platform in which the transactions are carried out.
Online auctions and classified advertisements are two examples of C2C platforms. EBay and Craigslist are two well-known examples of these platforms. Because eBay is a business, this form of e-commerce could also be called consumer-to-business-to-consumer. Platforms like Facebook marketplace and Depop -- a fashion reselling platform -- also enable C2C transactions.
Consumer-to-business (C2B). This is a type of e-commerce in which consumers make their products and services available online for companies to bid on and purchase. This is the opposite of the traditional commerce model of B2C.
A popular example of a C2B platform is a market that sells royalty-free photographs, images, media and design elements, such as iStock. Another example would be a job board.
Business-to-administration (B2A). This refers to transactions conducted online between companies and public administration or government bodies. Many branches of government are dependent on various types of e-services or products. These products and services often pertain to legal documents, registers, Social Security, fiscal data and employment. Businesses can supply these electronically. B2A services have grown considerably in recent years as investments have been made in e-government capabilities.
Consumer-to-administration (C2A). This refers to transactions conducted online between consumers and public administration or government bodies. The government rarely buys products or services from individuals, but individuals frequently use electronic means in the following areas:
- Social Security. Distributing information and making payments.
- Taxes. Filing tax returns and making payments.
- Health. Making appointments, providing test results or information about health conditions and making health services payments.
Mobile commerce. Also known as m-commerce, mobile commerce refers to online sales transactions using mobile devices, such as smartphones and tablets. It includes mobile shopping, banking and payments. Mobile chatbots facilitate m-commerce, letting consumers complete transactions using voice or text conversations.
Advantages of e-commerce
The benefits of e-commerce include its availability, accessibility, speed of access, selection of goods and services and international reach.
- Around-the-clock availability. Aside from outages and scheduled maintenance, e-commerce sites are available 24/7, enabling visitors to browse and shop at any time. Brick-and-mortar businesses tend to open for a fixed number of hours and even close entirely on certain days.
- Speed of access. While shoppers in a physical store can be slowed by crowds, e-commerce sites run quickly, depending on compute and bandwidth considerations of both the consumer device and the e-commerce site. Product, shopping cart and checkout pages load in a few seconds or less. A typical e-commerce transaction requires a few clicks and takes less than five minutes.
- Wide selection. Amazon's first slogan was "Earth's Biggest Bookstore." It could make this claim because it was an e-commerce site and not a physical store that had to stock each book on its shelves. E-commerce enables brands to make an array of products available, which are then shipped from a warehouse or various warehouses after a purchase is made. Customers are likely to have more success finding what they want.
- Easy accessibility. Customers shopping in a physical store might have difficulty locating a particular product. Website visitors can browse product category pages in real time and use the site's search feature to find the product quickly.
- International reach. Brick-and-mortar businesses sell to customers who physically visit their stores. With e-commerce, businesses can sell to anyone who can access the web. E-commerce has the potential to extend a business's customer base.
- Lower cost. Pure play e-commerce businesses avoid the costs of running physical stores, such as rent, inventory and cashiers. They might incur shipping and warehouse costs, however.
- Personalization and product recommendations. E-commerce sites can track a visitor's browsing, search and purchase histories. They can use this data to present personalized product recommendations and obtain insights about target markets. Examples of how such insights are used include the sections of Amazon product pages labeled "Frequently bought together" and "Customers who viewed this item also viewed."
Disadvantages of e-commerce
The perceived disadvantages of e-commerce include sometimes limited customer service, consumers not being able to see or touch a product prior to purchase and the wait time for product shipping. Security issues can also be a problem.
- Limited customer service. If customers have a question or issue in a physical store, they talk to a clerk, cashier or store manager for help. In an e-commerce store, customer service can be limited. The site might only provide support during certain hours and its online service options might be difficult to navigate or not able to answer specific questions.
- Limited product experience. Viewing images on a webpage can provide a good sense of a product, but it's different from experiencing the product directly, such as playing a guitar, assessing the picture quality of a television or trying on a shirt or dress. E-commerce consumers can end up buying products that differ from their expectations and have to be returned. In some cases, the customer must pay to ship a returned item back to the retailer. Augmented reality is expected to improve customers' ability to examine and test e-commerce products.
- Wait time. In a store, customers pay for a product and go home with it. With e-commerce, customers must wait for the product to be shipped to them. Although shipping windows are decreasing as next-day and even same-day delivery becomes common, it's not instantaneous.
- Security. Skilled hackers can create authentic-looking websites that claim to sell well-known products. Instead, the site sends customers fake or imitation versions of those products -- or simply steals credit card information. Legitimate e-commerce sites also carry risk, especially when customers store their credit card information with the retailer to make future purchases easier. If the retailer's site is hacked, threat actors may steal that credit card information. A data breach can damage a retailer's reputation.
E-commerce applications
Many e-commerce apps use online marketing strategies to improve the customer experience and get customers to use the platform. These include email, online catalogs, shopping carts, Electronic Data Interchange (EDI), file transfer protocol, web services and mobile applications.
These approaches are used in B2C and B2B e-commerce activities, as well as other types of outreach. They include emailing targeted ads and e-newsletters to subscribers and sending text messages to mobile devices. Sending unsolicited emails and texts is generally considered spam, so more companies now try to entice consumers online, using tools such as digital coupons, social media marketing and targeted advertisements.
Another area of focus for e-commerce companies is security. Developers and admins should consider customer data privacy and security, data governance-related regulatory compliance mandates, personally identifiable information privacy rules and information protection protocols when developing e-commerce applications. Some security features are added during the design of an application, while others must be continually updated to address evolving threats and new vulnerabilities.
E-commerce platforms and vendors
An e-commerce platform is a tool that's used to manage an e-commerce business. E-commerce platform options range in size from ones for small businesses to large enterprises. They include online marketplaces, such as Amazon and eBay, that simply require signing up for user accounts and little to no IT implementation.
SaaS is another e-commerce platform model. Business owners subscribe to a service where they essentially rent space in a cloud-hosted service. This approach doesn't require in-house development or on-premises infrastructure. Other e-commerce trends include open source platforms that require a cloud or on-premises hosting environment or complete manual implementation and maintenance.
Examples of e-commerce marketplace platforms include the following: Alibaba, Amazon, Chewy, eBay, Etsy, Newegg, Rakuten, Walmart Marketplace and Wayfair. Vendors offering e-commerce platform services for clients hosting their own online store sites include the following: Adobe Commerce, BigCommerce, Ecwid, NetSuite Commerce, Salesforce Commerce Cloud, Shopify, Squarespace and WooCommerce.
Government regulations for e-commerce
In the United States, the Federal Trade Commission (FTC) and the Payment Card Industry (PCI) Security Standards Council are among the primary agencies that regulate e-commerce activities. The FTC monitors activities such as online advertising, content marketing and customer privacy. The PCI Security Standards Council develops standards and rules, including PCI Data Security Standard compliance, which outlines procedures for the proper handling and storage of consumers' financial data.
To ensure the security, privacy and effectiveness of e-commerce, businesses should authenticate business transactions, control access to resources such as webpages for registered or selected users, encrypt communications and implement security technologies, such as secure sockets layer and two-factor authentication.
History of e-commerce
E-commerce began in the 1960s, when businesses started using EDI to share business documents with other companies. In 1979, the American National Standards Institute developed ASC X12 as a universal standard for businesses to share documents through electronic networks.

As the number of individual users sharing electronic documents with each other grew in the 1980s, the rise of eBay and Amazon in the 1990s revolutionized the e-commerce industry. Consumers can now buy many items online, from e-commerce-only vendors -- also called e-tailers -- and brick-and-mortar stores that have e-commerce capabilities. Almost all retail companies have integrated online business practices into their business models and sell online.
The COVID-19 pandemic caused a significant spike in e-commerce transactions. With shoppers confined to their homes for an extended period, e-commerce jumped to a record high of 16.4% of total U.S. retail sales in the second quarter of 2020, according to the U.S. Census Bureau. It has since leveled off at around 15%. The Census Bureau keeps a record of quarterly e-commerce data dating back to 1999. In Q3 2023, total U.S. retail e-commerce sales were estimated to be $284.1 billion.
Worldwide, Insider Intelligence estimated e-commerce sales would account for 20.8% of 2023 global retail sales and projected it will rise to nearly 22% of total sales in 2024.
Disruption to physical retail
Given the increase in e-commerce use in recent years, analysts, economists and consumers have debated whether the online B2C market will make physical, brick-and-mortar stores obsolete. There's little question that online shopping is growing at a significant rate. Gartner's 2023 "Magic Quadrant for Digital Commerce" estimated that by 2025, 80% of B2B sales transactions between suppliers and buyers will take place in digital spaces or channels.
Data from the U.S. Census Bureau shows the increasing importance of e-commerce in the U.S. retail market. The percent of total U.S. sales from e-commerce has consistently grown since 1999.
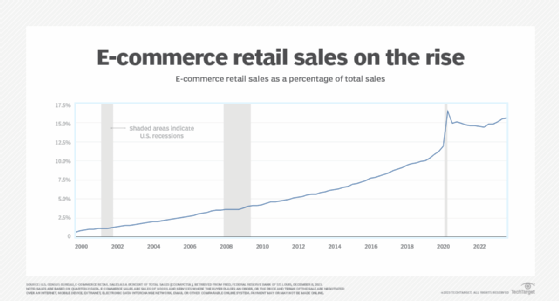
Despite the growth of online retail, many shoppers still prefer brick-and-mortar storefronts. In a 2023 report, Forrester analysts predicted that most retail sales will continue to come from physical stores and traditional retail. They estimated offline sales in the U.S. will reach $4.2 trillion and account for 72% of the country's retail sales by 2028.
Adoption of new tech also plays a part in the growth of online retail. A 2021 study from Juniper Research predicted e-commerce transactions made using a voice assistant will grow more than 320% to $19.4 billion by 2023 from $4.6 billion in 2021.
A consistent example of the effect e-commerce growth has had on physical retail is the post-Thanksgiving Black Friday and Cyber Monday shopping days in the United States. According to the National Retail Foundation's 2023 Thanksgiving Weekend Consumer Survey, about 90.6 million consumers made online purchases on Black Friday, up from 87.2 million in 2022. On Cyber Monday, approximately 73 million consumers shopped online.
M-commerce is one of the most important reasons why businesses should consider building mobile apps to better reach and engage with customers. Learn seven potential benefits for businesses gain from going m-commerce.






