code
What is code?
In computer programming, computer code refers to the set of instructions, or a system of rules, written in a particular programming language (i.e., the source code).
It is also the term used for the source code after it has been processed by a compiler and made ready to run on the computer (i.e., the object code).
In addition to building computer programs and mobile applications, code is used heavily for innovative concepts such as artificial intelligence and machine learning. Of course, there are several other uses and applications for the word code, explained in the next section.
What are some other types of code?
To answer the question, "What is code?" it is important to understand that the term code has a few different meanings, as well as different applications.
Let's take a look at some of those now.
Cryptography code
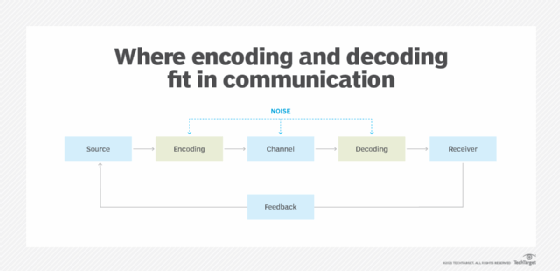
In cryptography, code is the substitution of one word or phrase by another word, number or symbol for the purpose of concealing the original word or phrase.
This could be used to hide someone's true intention from prying eyes and ears or to designate a military mission such as in World War II when Germany's invasion of the Soviet Union was given the code name of Barbarossa.
Thus, encoding refers to the conversion of data into undecipherable symbols or false names, whereas decoding converts those symbols or the false name back into an understandable form.
Abbreviations or acronyms as code
Abbreviations and acronyms are also referred to as codes in the sense that they are shortened versions of a word, meant to symbolize the full word.
For example, when referencing a state, a reader might see the abbreviation FL and will understand that it is referring to the state of Florida.
Or, in healthcare, a patient that arrives at the hospital that is already deceased would have their medical chart notated with the acronym DOA, which indicates dead on arrival.
Other examples of acronyms include:
- BASIC for Beginners' All-purpose Symbolic Instruction Code
- COBOL for Common Business Oriented Language
- NOW for National Organization for Women
- WHO for World Health Organization
- OASIS for Organization for the Advancement of Structured Information Standards
Genetic code
Additionally, in biology, the genetic material that makes up an organism and defines its development is referred to as the genetic code. This is also commonly referred to as DNA, an acronym for deoxyribonucleic acid.
It may sound like science fiction, but researchers have been working on encoding data into the double helix of DNA. This cutting-edge research promises a future storage technology with far higher storage densities (hence capacities) than today's flash, hard disk, optical and tape technologies.
(Editor's note: For the remainder of this definition, when we refer to code, we will be referencing it from the perspective of computer science.)
Coding in computer science
As stated previously, in computer science, code refers to the computer program algorithms, made up of symbols from a source alphabet, that represent the set of rules on what actions the program is expected to perform.
Essentially, it is our human language, translated by a coder, into lines of code that a computer can understand and respond to. It allows programmers to create software programs, operating systems and mobile applications.
Within computer language, specifically, there are a number of ways in which machine code can be used to provoke action or facilitate functionality.
What are the different coding languages?
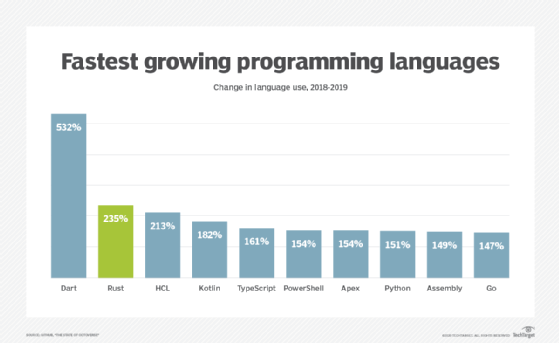
When writing code, there are a number of different coding languages in use today and each has different benefits and applications they are most commonly used for, such as:
- PHP. PHP is a general scripting language used heavily in web development.
- Java. Java is an object-oriented programming language built to have minimal dependencies for implementation and requires compilation. It is heavily used in back-end software
- JavaScript. JavaScript is an all-text programming language that, unlike Java, can be run on a browser only.
- Python. Python is another general-purpose programming language designed to emphasize readability.
What is the difference between code and markup language?
As it relates to websites and webpages, markup language also becomes part of machine language as it dictates to the system how a page should be formatted.
It is sometimes confused with or used interchangeably with programming language (or code). But there are some important distinctions to recognize.
The main difference between the two is that markup language is readable by both machines and humans, and, again, it is a set of instructions for how a webpage should be laid out.
Conversely, programming code is the instructions given to a machine to create a computer program. While these two operate in the same universe, they are used for different purposes.
Examples of markup languages include:
- HTML (Hypertext Markup Language)
- XML (Extensible Markup Language)
- SAML (Security Assertion Markup Language)
- DCML (Data Center Markup Language)
- SGML (Standard Generalized Markup Language)
