com
What is com?
On the Internet, "com" is one of the top-level domain names that can be used when choosing a domain name. Usually, it describes the entity owning the domain name as a commercial organization. Along with the second-level domain name -- for example, the "whatis" in whatis.com -- the top-level domain name is required in web and email addresses.
"Com" is also short for "commercial," although operation of a commercial website isn't required to own a domain suffix.
What is com in a URL?
A Uniform Resource Locator (URL), commonly called a web address, is the address of a unique resource on the web. It has three parts:
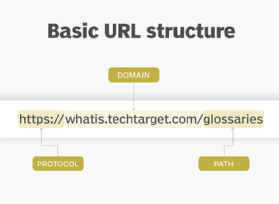
- protocol, the primary access medium;
- domain, which refers to the website and where com is often seen; and
- path, which refers to a location on the site.
Web browsing and most other Internet activities rely on the Domain Name System (DNS) to provide the information necessary to connect users to remote hosts. DNS falls into a category of utility protocols that underpin communications on the Internet. These are robust protocols that help keep traffic flowing and servers talking; most users don't know they exist.
Who assigns and manages domain names?
The Internet Corporation for Assigned Names and Numbers (ICANN) has overall responsibility for assigning domain names, Internet Protocol (IP) addresses and many other Internet parameters. Day-to-day responsibility is delegated to specific registrars, such as Network Solutions and several competing companies for .com, .org, .net and .edu top-level domains. Although .com is the most popular domain extension, .net came first. The Nordic Infrastructure for Research and Education first debuted Nordu.net in 1985.
Today, we also have domains such as .agency, .co, .fund, .media, .shop, .store, .solution, .xyz, and many more. Specific criteria are set forth for the use of the top-level domain name in RFC 1591: Domain Name System Structure and Delegation. The top-level domain names administered by ICANN and its delegate agencies are .com, .edu, .gov, .io, .net and .org.
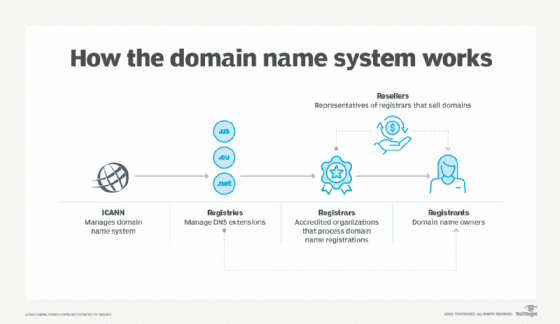
Domain name applicants within the U.S. may also be able to register a name under a U.S. top-level domain name based on geography. Refer to RFC 1480: The US Domain and visit the U.S. Domain Registry for registration procedures.
Top-level domain names for countries other than the U.S. are administered by each country and based on the International Standards Organization (ISO) 3166 list of country codes.
What is a com port?
The serial port interfaces found on personal computers (PCs) are called COM or a communication port. It may refer to a single port or several emulated ports like USB 3.0 and Bluetooth.
What is com in electrical?
In electrical switches, com stands for common. For example, in a one-way light switch, there are two terminals usually called C or common. One terminal represents the live wire or input supply power to the switch. The second terminal, typically called L1, is the output that connects to the light fixture.
What is COM in Microsoft?
In Microsoft software architecture, COM stands for Component Object Model. This component software architecture defines the structure where program routines or objects can be built, called up and executed in a Microsoft Windows environment.
Explore IPv4 vs. IPv6 and learn the difference between a MAC address and IP address.
