communication plan
What is a communication plan?
A communication plan is a policy-driven approach to providing company stakeholders with certain information.
Communication plans are typically used in business settings to ensure all parties have the latest updates on projects, goals and objectives. They are also critical aspects of both incident response and business continuity (BC) planning.
Why communication plans are important
Businesses need communication plans for several reasons:
- They help ensure everyone is on the same page.
- They can prevent or mitigate the impact of potential crises.
- They can help improve efficiency and optimize workflows.
Communication plans matter because they help businesses run more smoothly and effectively.
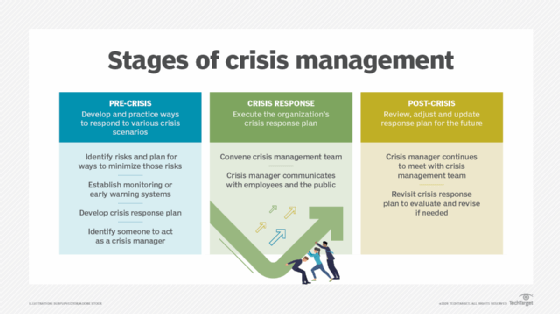
Elements of a communications plan
A communication plan formally defines the following:
- who should receive specific information;
- when that information should be delivered; and
- what communication channels should be used to deliver the information.
An effective communication plan anticipates what information needs to be communicated to specific audience segments.
The plan should also address who has the authority to communicate confidential or sensitive information and how information should be disseminated -- email, websites, printed reports and/or presentations at meetings that may be virtual or given in person.
The plan should also define what communication channels stakeholders use to solicit feedback and how communication is documented and archived.
The specifics of what should be included in a communication plan vary from business to business, but the following are common elements typically included:
- the forms of communication that are used, including announcements over a building paging system, automated text messages, email alerts, prerecorded phone calls, meetings and social media;
- who communicates what information to whom;
- how often communication occurs; and
- how communication is documented and archived.
Finally, a communication plan should be tailored to the specific needs of the business and the people involved and be reviewed and updated regularly to ensure it remains relevant and effective.
How communications plans are used
Communication plans have a variety of use cases. They're frequently used in crisis management and BC planning, but those aren't their only uses.

Communication plans play an important role in change management. An effective communication strategy can help lower resistance to change by getting everyone on the same page and helping stakeholders become engaged and, ultimately, endorse the need for change and the steps being taken to bring it about.
In project management, the communications plan may include a glossary of common terms to facilitate understanding among stakeholders. This glossary may also define and include samples of templates, reports and forms that the project manager uses to communicate information.
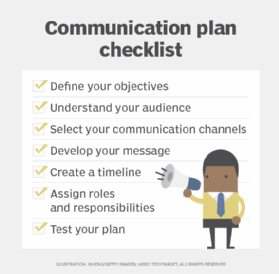
Steps in creating a communications plan
To build a useful communication plan, start by understanding the needs of your business and the people who are impacted by the communication. With a clear understanding of these needs, you can begin to develop a plan that meets them. Here are some steps to follow as you create the plan:
- Define your objectives. What do you hope to achieve?
- Understand your audience. Who is impacted by the communication? What do they need to know? When do they need to know it?
- Select your communication channels. What communication channels work best for your audience and your objectives?
- Develop your message. What information do you need to communicate, and how can you do so effectively?
- Create a timeline. When does your communication take place? How often?
- Assign roles and responsibilities. Who is responsible for generating and delivering the communication? Who approves messages before they're sent?
- Test your plan. Once you've developed your communication plan, test it to ensure it works as intended. Get feedback from your audience, and make adjustments as needed.
By following these steps, you can create a communication plan that meets the specific needs of your business and helps you achieve your objectives.
Learn how to implement a communication plan, explore tips for building a crisis communication plan and check out a template for BC planners developing an emergency communications plan.
