context switch
What is a context switch?
A context switch is an operation that a computer's central processing unit (CPU) carries out when alternating between processes or threads while ensuring that the processes do not conflict. Effective context switching makes it possible to support a multitasking environment.
Each time the CPU makes a switch, the system temporarily suspends the currently executing task, saves its state (context) to a process control block (PCB), and then executes the next task in the queue. If that task has already been started, the CPU retrieves the state for that task so it can start the execution where it left off. These operations continue and repeat as the CPU rotates between the queued processes.
The ability of context switching to switch rapidly between tasks is a core capability of a multitasking operating system (OS) such as Windows, Linux or macOS. Context switching enables multiple processes to share a single CPU, while making it appear as though the CPU is executing multiple processes simultaneously. It is this capability that enables users to switch seamlessly between the open applications on their desktops.
How does a context switch work?
Each time the CPU switches to a different process, it saves the state data to its assigned PCB. The exact data can vary between systems, but it generally includes the pointer, program counter, registers and other information associated with the process.
A process control block is a data structure that is created for each process. In addition to state data, it also stores the process's execution state, process number and memory management information.
Context switching generally occurs as a result of one of the following triggers:
- Multitasking operation. Context switching occurs when one process gives way to another process so the second one can be executed. In some cases, context switching takes place because the process has been allocated only a certain amount of CPU time. However, it can also occur when a process must cede the CPU to a process with a higher priority. Or a process might cede the CPU voluntarily, such as when waiting on an input/output operation.
- Interrupt. Content switching occurs because of a system interrupt from a hardware or software component. For example, a keyboard might issue an interrupt when a user presses a key, or an application might issue an interrupt when it requires user input. An OS typically contains an interrupt handler to process and prioritize these requests.
- User/kernel switching. In some cases, context switching can occur when the OS transitions between user mode and kernel mode. For example, a process might need to switch from user mode to kernel mode to access a system resource, which could require a context switch to accommodate the different privilege level.
When the CPU encounters one of these triggers, it kicks off a series of steps that alternate between executing processes. The following figure provides a high-level overview of how context switching might occur between two processes. The exact approach to context switching depends on the operating system and other variables. Conceptually, however, the various systems follow a similar pattern.
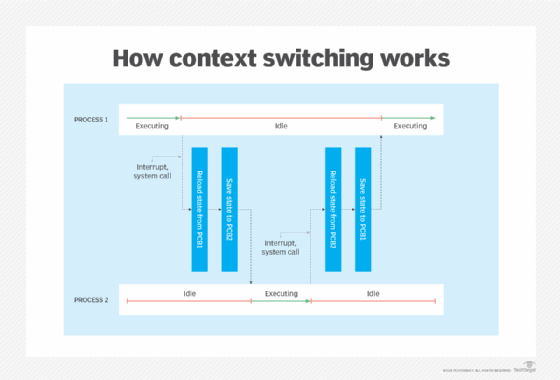
The figure illustrates how the CPU alternates between Process 1 and Process 2, switching back and forth between executing and idle states. The following steps describe the basic sequence of events when moving between processes:
- The CPU executes Process 1.
- A triggering event occurs, such as an interrupt or system call.
- The system pauses Process 1 and saves its state (context) to PCB 1, the process control block that was created for that process.
- The system selects Process 2 from the queue and loads the process's state from PCB 2.
- The CPU executes Process 2, picking up from where it left off (if the process had already been running).
- When the next triggering event occurs, the system pauses Process 2 and saves its state to PCB 2.
- The Process 1 state is reloaded, and the CPU executes the process, once again picking up from where it left off. Process 2 remains in an idle state until it is called again.
The greater the number of active processes, the more complex these operations become, especially as processes are started and stopped. Even so, the CPU can still execute only one process at a time, no matter how many tasks wait in queue. Context switching also takes time to carry out because state data must be saved and retrieved for each transition. The more switching that occurs, the more time needed to alternate back and forth. If the overhead gets to be too much, system performance can degrade.
A context switch can be performed entirely in hardware, although this approach tends to be limited to older CPUs, such as those in the early x86 series. Today, context switching is software-based and typically handled in the kernel, which is faster and more efficient than hardware-based context switching. A modern system can perform hundreds of context switches per second. Although the computer appears to be performing multiple tasks in parallel, the CPU is alternating between operations at a high rate of speed.
Explore the differences between CPUs vs. microprocessors. Learn about the differences between monolithic and microkernel architectures and check out memory management techniques improve system performance.
