controller (computing)
What is a controller (computing)?
A controller, in a computing context, is a hardware device or a software program that manages or directs the flow of data between two entities. In computing, controllers may be cards, microchips or separate hardware devices for the control of a peripheral device. In general, a controller can be thought of as something or someone that interfaces between two systems and manages communications between them.
Who uses controllers?
Anyone who uses a computing device, such as a laptop or smartphone, employs controllers to connect to devices and applications that are used for business or personal activities. Controllers extend a computer's processing power to resources that help improve a user's productivity.
What is the difference between a controller and a driver?
Think of a controller as a component interfacing with the central processing unit and moving data back and forth between the CPU and the device being controlled, such as a printer or disk drive. Controllers typically have a buffer to store data coming either from the CPU or the device being controlled. By contrast, a device driver is a software program that instructs the controller on how to operate. Figure 1 depicts the difference between a controller and a driver as implemented on a motherboard.
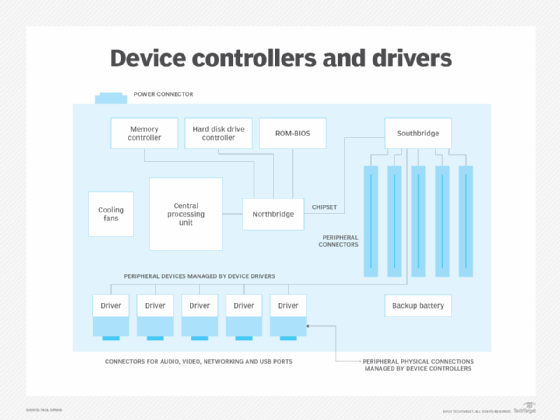
Figure 1 depicts circuit boards that have both device drivers and controllers. The controller links to a device, while the driver links the controller with the computer's operating system (OS).
Examples of controllers in technology applications
Control systems and controllers come in many forms and applications. This table offers examples of controller applications.
| Examples of Technology Controllers | |
| Type of Controller | Functions Performed |
| Graphics card | Integrated circuit card in a computer or, in some cases, a monitor that provides digital-to-analog conversion, video RAM and a video controller so that data can be sent to a computer's display |
| Game controller | Input device for playing video games |
| Network interface card (NIC) | Computer circuit board or card that is installed in a computer so that it can be connected to a network |
| Wide area network interface card (WIC) | Specialized NIC that enables devices to connect to a wide area network |
| Flash controller | Part of flash memory that communicates with the host device and manages the flash file directory |
| Application delivery controller (ADC) | Data center network device that helps manage client connections to complex web and enterprise applications |
| Baseboard management controller (BMC) | Specialized service processor that monitors the physical state of a computer, network server or other hardware device using sensors and communicating with the system administrator through an independent connection |
| Session border controller (SBC) | Device or application that governs the way calls, also called sessions, are initiated, conducted and terminated in a voice over IP network |
| Primary domain controller (PDC) | Role that can be assigned to a server to manage access to a set of network resources -- e.g., applications, printers -- for a group of users |
| Backup domain controller (BDC) | Role that can be assigned to a server to manage access to a set of backup resources -- storage devices -- for a group of users |
The importance of controllers
Controllers and drivers provide important links between the computer and devices and applications being used. While the OS controls computer functions, controllers and their associated drivers extend OS functionality to specialized tools and resources that increase a user's productivity.
Learn about the benefits of application delivery controllers, and see what software-defined network data center controllers do in a network.