
flash memory card
What is a flash memory card?
A flash memory card -- sometimes called a storage card -- is a small storage device that uses non-volatile semiconductor memory to store data on portable or remote computing devices. Such data includes text, pictures, audio and video.
Most current products use flash memory, although other memory technologies are being developed, including devices that combine dynamic RAM (DRAM) with flash memory, such as UltraRAM, which is based on quantum memory and computing.
Evolution of the flash memory card
Earlier removable storage media -- such as the PC card, smart card and similar cards used for computer gaming systems -- are also considered memory cards. However, the newer types of memory cards are smaller, require less power, have higher storage capacities and are portable among more devices. Because of these features, memory cards are influencing the production of an increasing number of small, lightweight, low-power devices.
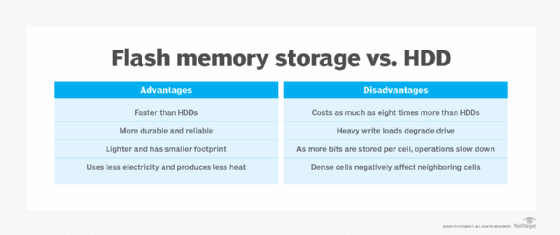
Memory cards offer several advantages over a hard disk drive (HDD): They're much smaller and lighter, are extremely portable, are silent, enable more immediate access and are less prone to mechanical damage. However, an HDD still offers a compelling advantage: Although flash prices are coming down, a typical memory card still costs more -- and has a lower storage capacity -- than a high-capacity HDD.
This article is part of
Flash memory guide to architecture, types and products
Types of memory card formats: Consumer devices
There are several flash memory card types on the market, roughly divided between consumer devices and enterprise storage devices. The cards come in varying sizes and storage capacities, typically corresponding directly to their price.
Popular memory card formats used in consumer devices include the following:
- Secure Digital (SD) cards. One of the most widely used flash memory cards, they're available in a variety of formats, speed classes and capacities. These postage stamp-sized memory devices are widely used in handheld devices, including digital cameras, smartphones and tablets. SD cards, which secure digital data by encrypting it on the device, are also available as miniSD and microSD cards.
- SD High Capacity (SDHC) and SD Extended Capacity (SDXC) cards. SDHC and SDXC cards are variants of the common SD card format. SDHC cards normally have capacities ranging from 4 gigabytes to 32 GB, and SDXC cards have capacities ranging from 32 GB to 2 terabytes (TB). SDHC and SDXC cards are backward-compatible with ordinary SD devices.
- MicroSD cards. In 2005, SanDisk and Motorola teamed up to introduce the original microSD product, then known as TransFlash, as a 128 GB and 11x15 millimeter removable card for mobile phones. In June 2016, SanDisk -- now part of Western Digital Corp. -- launched a suite of 256 GB microSD cards, including Ultra microSDHC and microSDXC Ultra High Speed-I cards geared for Android-based devices. The primary distinction between SD cards and their microSD cousins, besides size, is capacity. The maximum storage capacity for the microSD format is 1 TB, although the most recent SDHC ultra capacity cards can support up to 128 TB. MicroSD cards can also be used in a regular SD card slot with a microSD-to-SD adapter.
- CompactFlash cards (CF cards). The forerunner to the SD card, the original CF cards were designed on the Parallel Advanced Technology Attachment standard and were no larger than a matchbook. CF cards included a microcontroller and were used as flash memory storage for high-resolution photography. CF and SD cards lack built-in USB computer device connectivity. They are larger than SD cards and are mostly utilized in professional cameras, such as high-end digital single-lens reflex cameras, and industrial applications. Due to their larger storage capacities and faster transfer speeds, they're ideal for high-volume photography and video recording.
- Memory stick cards. Sony developed its memory stick technology as a removable flash storage device to transfer photos and high-definition video. They were widely used in numerous products, including cameras, camcorders and game consoles, such as the PlayStation Portable. However, their popularity has waned as SD cards have risen to dominate the market.
- USB drives. This portable plug-and-play flash storage device, also known as a flash drive, is inserted into a computer's standard USB port. USB drives ushered in the demise of floppy disks and, to some extent, the reduced use of compact discs. While most flash drives have between 2 GB and 64 GB of memory, depending on the type and manufacturer, some drives can store as much as 2 TB of data.
- Multimedia cards (MMCs). Developed in 1997 by SanDisk and Siemens, MMCs were originally designed to use NAND flash memory technology from Toshiba. However, MMCs are less common with the arrival of SD card technology. Most computer hardware vendors no longer provide ports for inserting an MMC device.
- Embedded MMCs (eMMCs). EMMCs integrate a flash card into the computer motherboard, along with controller software, to use the eMMC as a bootable system drive. EMMCs weigh approximately 2 grams and are used extensively in smartphones, tablets and other embedded devices. EMMC storage combines the flash memory and controller into a single chip, resulting in a small, low-cost storage option.
- Universal flash storage (UFS) cards. UFS cards are relatively new and offer better data transfer speeds when compared to other flash card formats. They're often found in high-end smartphones, tablets and other devices requiring quick, dependable storage performance.
- CFast and CFexpress cards. These high-performance flash memory card formats are suited for professional photography and cinematography. CFast and CFexpress cards have the same form size as CF cards but provide quicker read/write rates, making them well suited for capturing high-resolution photos and videos.
Most types of memory cards available have constantly powered, non-volatile memory, particularly NAND flash. Non-volatile memory safeguards data in the event of a power outage, software bug or other disruption and also eliminates the need to periodically refresh data on the memory card. Because memory cards use solid-state media, they have no moving parts and are less likely to suffer mechanical difficulties.
Consumer solid-state drive flash cards
Unlike SD memory cards, solid-state drives (SSDs) are nonremovable storage typically built into larger devices, such as servers and computers. Consumer-grade SSDs embed silicon-based memory chips as storage media for persistent storage of data.
The earliest SSDs were generally designed for consumer devices. The debut of the Apple iPod in 2005 marked the first notable flash-based device to broadly penetrate the consumer market. Today, SanDisk offers a line of extreme portable SSDs known as SanDisk Extreme that scale to 4 TB of flash capacity.
The earliest commercially designed SSDs were made with single-level cell (SLC) or multi-level cell (MLC) flash. SLC uses a high grade of flash media to provide performance and endurance, but it typically costs twice as much as MLC flash.
Some consumer-grade flash memory cards are used by companies to cache reads and writes with hybrid flash storage. Enterprise MLC is an MLC NAND variant with enhanced write cycles compared to consumer-grade MLC. Some newer enterprise SSDs use triple-level cell NAND flash, which stores 3 data bits per flash cell, and quad-level NAND (QLC NAND), which can store up to 4 bits of data per memory cell. SSDs made with QLC NAND represent the next evolution in flash memory products.
Enterprise-grade SSDs
In most respects, the above types of flash memory cards differ from those used in enterprise storage. SSDs aren't all created equally and, therefore, aren't suited for all applications. As such, the difference between a client SSD and an enterprise SSD is vast. For example, the low-cost, consumer-grade SSDs, such as Samsung Evo, WD Green from Western Digital and Seagate BarraCuda, are meant for consumer use cases, while the expensive enterprise-grade options, including Samsung PM883, Western Digital Ultrastar, Seagate Nytro and Kingston Technology DC500, are used in data centers and corporate environments.
EMC -- now Dell EMC -- is credited with being the first vendor to include SSDs in enterprise storage hardware when it added them to its Symmetrix disk arrays in 2008, spawning the advent of hybrid arrays that combine flash drives with a traditional spinning disk. Initially, enterprise SSDs in hybrid arrays were relegated to caching read data in flash due to their higher cost and lower endurance compared to HDDs.
SSDs are commonly available in form factors similar to traditional HDDs, such as 1.8-inch, 2.5-inch and 3.5-inch. SSDs can be inserted into slots in computer servers -- referred to as server-side flash storage -- or used as part of an enterprise flash storage array system.
PCIe-based SSDs are designed around Peripheral Component Interconnect Express (PCIe), a high-speed expansion card format that connects a computer with its attached peripherals. Compared to Serial Advance Technology Attachment (SATA) SSDs, PCIe SSDs are preferred but are costlier, due to their direct connection to a system's motherboard. They offer faster data transfer rates and are commonly used in devices that require high write/read speed data connections.
PCIe has a point-to-point architecture, enabling each device to connect to a host via its own serial link, rather than by sharing a network bus. By virtue of this direct connection, PCIe SSDs are generally rated to deliver higher performance than SATA, Serial-Attached SCSI (SAS) or Fibre Channel (FC) SSDs.
Flash memory cards in servers
Aside from SSDs, other form factors for server-based flash storage include the following:
- Add-in card (AIC) SSDs. These fit in a PCIe serial connection.
- Disk-on-module devices. These mount to a motherboard as a flash-based boot drive. These devices have non-volatile memory and are frequently used where an HDD would be inappropriate due to the usage environment.
- Flash dual inline memory modules (DIMMs). Otherwise known as memory channel solid-state storage, these exploit idle DIMM DRAM slots as low-latency, high-performance flash cache to buffer host server performance.
- M.2 form factor SSDs. Introduced in 2012 as a replacement for mini SATA flash drives, M.2 SSDs are used for ultrabooks, mini PCs, laptops and other portable devices because of their compact and thin design. They can hold up to 2 TB of data and take up less space than 2.5-inch SSDs or hard drives.
- Non-volatile DIMMs (NVDIMMs). These combine DRAM with non-volatile memory, usually NAND flash. There are three categories of NVDIMM cards:
- NVDIMM-N devices make only the DRAM visible to the system. The flash component isn't addressable storage and serves only as a backup to DRAM.
- NVDIMM-F, also known as memory channel flash, contains flash and no DRAM. NVDIMM-F capacities are similar to SSDs, with the earmark of lower latencies than standard flash storage.
- NVDIMM-P combines the functionality of NVDIMM-F and NVDIMM-N on one module. This non-volatile memory is allocated in two ways. Part of it provides persistence to DRAM, while the remainder is available as block storage.
Emerging flash memory card specifications
The non-volatile memory express (NVMe) protocol is a specification that enables an SSD to exploit the PCIe bus. NVMe operates at the host controller to define the command set and feature set needed to streamline the input/output stack. The goal is to enable PCIe-based SSDs to deliver low latency and higher throughput and consume less power when compared to SAS or SATA SSDs. The newest specification of NVME, NVMe 2.0c, was released in October 2022.
The nonprofit NVM Express Inc. developed the NVMe over Fabrics (NVMe-oF) industry specification to enable the NVMe storage interface to transfer data commands via Ethernet, FC, InfiniBand and other network fabrics. NVMe-oF is quickly becoming a popular storage networking protocol that offers high performance, low latency, scalability and support for existing network protocols, such as FC, TCP and remote direct memory access.
Hybrid RAM-flash memory and next-gen memory card technology
For decades, traditional memory technologies, including DRAM and NAND flash, have served as reliable memory technologies. However, with the explosive growth in data generation and consumption, these options are nearing their performance, capacity and energy efficiency limits. To overcome these constraints and unlock new possibilities, several next-generation memory technologies have emerged that have the power to meet the increasing needs of the data-focused world.
The following are a few next-generation flash memory offerings that are changing the way industries work by offering faster, better and more dependable memory options:
- Resistive RAM (ReRAM). One of the most promising contenders is ReRAM, also known as RRAM. ReRAM modifies the resistance of a material, typically a metal oxide, to store data. This approach delivers faster read/write speeds, higher storage densities and lower power consumption compared to traditional memory technologies. By combining the strengths of RAM and flash memory, ReRAM has the potential to replace both DRAM and NAND flash across a wide range of applications, from data centers to consumer electronics.
- Magnetoresistive RAM (MRAM). MRAM uses magnetic elements to store data, enabling them to retain their state even without power, making it a non-volatile memory option. MRAM offers several advantages over traditional memory technologies, including rapid read/write operations, reduced power consumption and exceptional endurance. Due to its non-volatile nature and high reliability, MRAM is beneficial in fields such as automotive and industrial systems, where it has already made significant progress. According to a report from McKinsey, the number of MRAM chips used in automobiles is forecasted to increase from 600 in 2021 to approximately 1,220 by 2030.
- Phase-change memory (PCM). By switching a substance's phase between its amorphous and crystalline states, commonly a chalcogenide glass, PCM retains data. High storage densities, quick read/write rates and non-volatile data storage are all made possible by this. PCM has the potential to be applied in a variety of fields, including consumer electronics and high-performance computers.
QLC flash is quickly gaining popularity as a viable memory storage technology. Explore its importance and influence on the hybrid cloud storage options available on the market.







