critical path method (CPM)
What is critical path method?
The critical path method (CPM) is a step-by-step project management technique for process planning that defines critical and non-critical tasks with the goal of preventing project schedule problems and process bottlenecks. CPM is ideally suited to projects consisting of numerous activities that interact in a complex manner.
In applying CPM, the following five steps are often followed:
- Define the required tasks and arrange them in an ordered, sequenced list.
- Create a flowchart or other critical path diagram showing each task in relation to the others.
- Identify the critical and non-critical relationships or paths among the tasks.
- Determine the expected end date or execution or completion time for each task.
- Locate or devise alternatives or backups for the most critical paths.
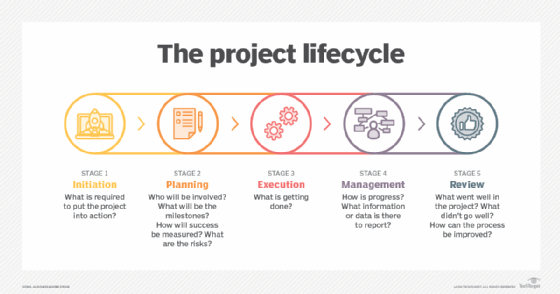
What is the critical path method?
When developing an overall project management plan it is essential to identify the project scope, which is all the activities and tasks that must be performed. In addition, those tasks must be assembled in the correct sequence and estimated time frames to complete provided for each. This helps project managers track the following:
- where the project is at any time;
- whether activities are ahead of or behind the critical path schedule;
- which steps need additional resources;
- which steps need to be rescheduled; and
- whether the project is on budget.
The critical path method is the piece of the project management plan that identifies the steps that must be completed -- the critical path. CPM also provides insight into ancillary activities that support the outputs and deliverables needed for other critical path activities and parallel critical paths that are linked to the primary critical path. These are all important to keeping a project on schedule and budget and reaching its goals.
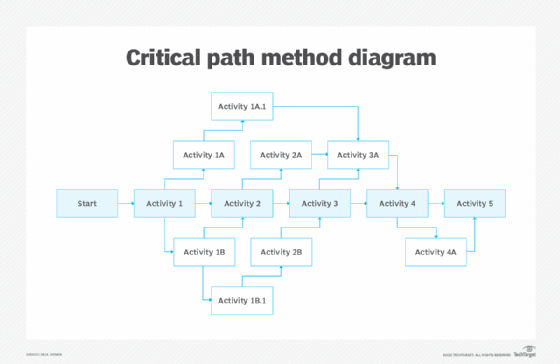
In Figure 2, the critical path is highlighted. It includes the activities that must be completed for the project to reach its conclusion and is usually the longest path in the diagram. The diagram also depicts other elements of project planning: the sequence of tasks and the ancillary activities that are initiated from other parts of the plan and the activities they impact. The arrows identify the sequence of events.
Each activity box could be filled in with specific details related to each activity, such as a project timeline that includes the earliest start time and earliest finish time for each task, required resources and options to launch if the activity is not completed on time. Depending on the complexity of the project, more information may be embedded in each activity box.
Steps in the CPM process
CPM encompasses the following six steps:
- Identify each activity to be completed in the project; start with the high-level ones and then identify ancillary activities.
- Define the activity sequence. This also requires identifying dependencies among activities, such as which ones occur before or after others and which should occur concurrently.
- Build a flow diagram, also called a network diagram, similar to the one in Figure 2, that positions all activities for the entire project.
- Estimate the amount of time for completion of each activity and map that to the whole project plan, including the estimated completion date.
- Perform a critical path analysis to define the activities that must be completed to ensure project completion and success.
- Update the plan as the project progresses, accounting for delays, resource allocation, staffing issues and other factors. For this step, project management software with CPM capabilities is essential. These tools use a critical path algorithm that automatically adjusts the plan based on specific inputs, such as changes in scope or time frame.
Pros and cons of using CPM
Some of the advantages of using the critical path method include the following:
- identifies the sequence of activities and work breakdown structure;
- defines the activity duration for all elements of the plan;
- specifies cross-functional relationships among project activities;
- identifies dependent tasks for each activity;
- cites risks to the project, such as failure to complete a specific activity on time;
- identifies ways to shorten time frames;
- compares the plan with performance to quickly identify issues;
- helps optimize project resources;
- identifies opportunities to change time frames, adjust team members and their duties, and modify the overall plan to achieve the desired outcome.
CPM provides many benefits, but it may not always be the most appropriate method for managing a project. For example, smaller, less complicated projects may not need the complexity of CPM. Various project management applications provide simpler tools and templates that might be more applicable to a less complicated project.
For complex projects, a project management team with CPM experience is essential. That, however, requires factoring in the overhead and related costs of using CPM.
What was the origin of CPM?
DuPont developed CPM in the 1950s. The chemical company first used the methodology in developing neoprene, a type of synthetic rubber. CPM streamlined production and maintenance in that development process.
Around the same time, the U.S. Navy developed a similar project management method -- Program Evaluation Review Technique (PERT) -- to address the development and production of submarine-based Polaris missiles. The two methods have similar objectives. PERT and Gantt charts are often used as part of project planning methodologies.
As a project planning tool, CPM has been adapted to other fields, including hardware and software product research and development. Various computer programs are available to help project managers use CPM.
CPM is part of overall project management and business process management (BPM) practices. Learn more about BPM best practices and how they affect project success.
