cryptojacking
What is cryptojacking?
Cryptojacking is a cybercrime in which another party's computing resources are hijacked to mine cryptocurrency. Cryptojacking, which is also referred to as malicious cryptomining, lets hackers mine cryptocurrency without paying for electricity, hardware and other mining resources.
Cryptojacking malware often infects devices through standard phishing techniques. It also can embed itself in websites and then run in a victim's web browser when they visit that site. Cryptojackers target computers, laptops, phones, servers and cloud infrastructures. They go after everyone from average users to the government agencies around the world.
Cryptojacking was the third most prevalent cybersecurity threat in 2021, according to the European Union Agency for Cybersecurity's (ENISA) annual report. In the same year, Google's Cybersecurity Action Team found that 86% of its observed compromised cloud platforms resulted from cryptojacking. In 2020, Cisco reported 69% of its customers were affected by cryptomining malware.
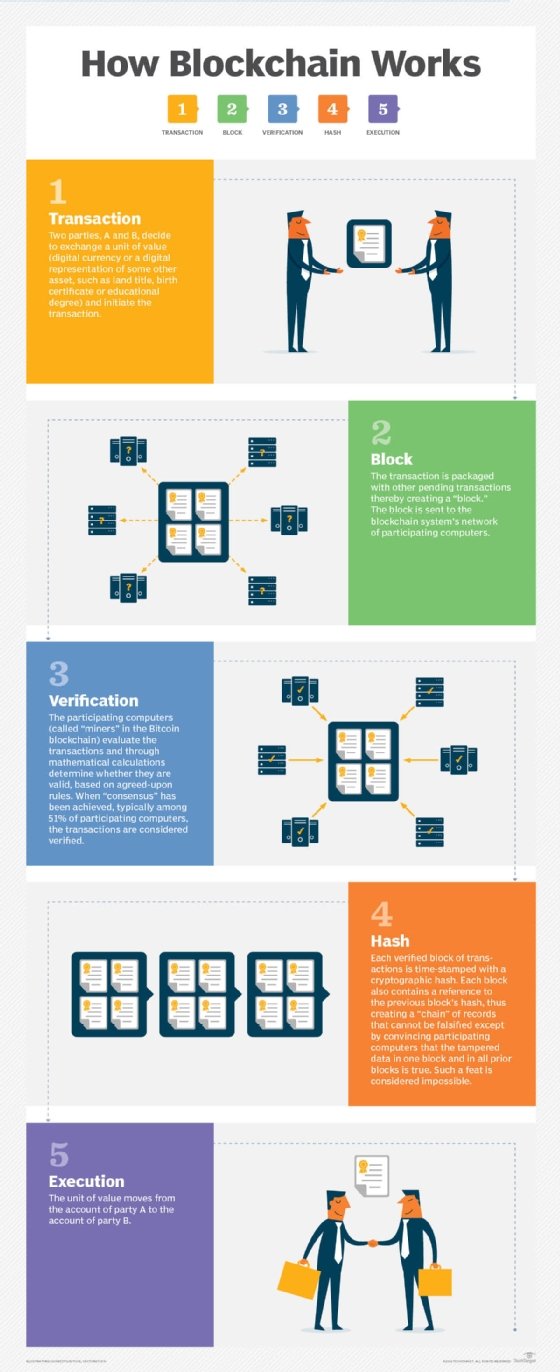
How does cryptojacking work?
Cryptojacking is an illegal form of cryptomining. In simple terms, cryptomining is the operation that generates new cryptocurrency, a type of Digital currency created and encrypted on the record-keeping technology called blockchain.
Blockchain transactions generate complex mathematical puzzles that must be solved before the transaction can be authenticated and completed. Cryptocurrency miners are the people who solve the encrypted puzzles, validate the transaction and earn cryptocurrency for their efforts. The cryptomining process is the only way to create and encrypt new coins on the blockchain.
Cryptojacking uses a victim's computing power to perform the complex mathematical operations needed to mine cryptocurrency and send the results to the cryptojacker's server. Unlike some types of malware that damage victims' devices or data, cryptojacking is designed to exploit its victims' resources as long as possible without being detected. Cryptojackers use a small amount of a victim's processing resources, while targeting a large number of victims. The malware runs in the background, quietly redirecting victims' processing power toward illicit cryptomining tasks.
Cryptojackers use two main attack modes: web browser and host-based. Web browser attacks embed cryptomining software on a website that runs when a victim visits that particular site. Host-based attacks use malware that gets downloaded onto a victim's device.
Both attack methods involve the following steps:
- Script preparation. A miner prepares a cryptomining script to infect a website or device.
- Script infection. A website is infected or a victim's device is compromised when they click on a link and unknowingly download cryptomining software.
- Attack. The cryptomining script is executed and begins using the victim's computing resources to run cryptomining software. The cybercriminal controls how much power is directed from the victim's device to the illicit mining operation.
Why do some miners cryptojack?
Mining for cryptocurrency is not a crime, but it is a high-cost, nonstop operation that requires substantial electricity and expensive mining network nodes. Many cryptocurrencies have market caps that limit the supply of coins that can be mined. These cryptocurrencies are designed to be harder to mine as they approach their market cap, in order to extend the mining process as long as possible, while simultaneously driving up the price of the currency.
Growing mining competition and high electricity costs mean the cost of mining can outweigh the profits. For instance, the entire ecosystem of Bitcoin mining -- the most well-known cryptocurrency -- uses nearly 100 terawatt hours a year, which is more than many countries use in a year, according to Cambridge University's Bitcoin Electricity Consumption Index.
Mining just one bitcoin costs, on average, $35,000, according to Visual Capitalist calculations. One bitcoin requires nearly 1,400 kilowatt hours, equivalent to the average amount of energy consumed by an American family in 50 days, according to Digiconomist. Cryptocurrency prices are quite volatile. As a result, the cost of mining a single bitcoin can be higher than the price of that one bitcoin.
Cryptojackers target victims' computing resources to offload the mining expenses to as many entities as possible. Though cryptojacking is designed to be undetectable, over time, its high processing demands can damage victims' devices and cause poor device performance, high electricity bills and shorter device life spans.
Types of cryptojacking
As previously mentioned, there are two main types of cryptojacking. One is based on infecting the web browser, and the other uses host-based methods.
Browser cryptojacking
The browser-based approach works by creating content that automatically runs cryptomining software in a user's web browser when they visit the webpage hosting it. This method is also known as drive-by cryptomining. Cryptojackers may create a website with embedded cryptomining JavaScript code and direct traffic to it for the purpose of cryptojacking, or they may compromise an existing site.
Existing websites can be compromised through Programmatic advertising, which contains malware that automatically places ads on sites. This is done without website owners' knowledge, and they have little control over whether their site runs the software.
Compromised ads can also be placed on a site as pop-unders designed to hide under windows already open on a victim's computer or phone and avoid detection. This type of malware uses domain generation algorithms to bypass ad blockers and serve ads to all site visitors.
Cryptojackers can also embed JavaScript in websites without using ads. Some websites even disclose that their pages use visitors' devices to run cryptomining software while being visited. This technique has been proposed for other uses, such as providing revenue for sites and services and Crowdfunding for disaster relief efforts. In these instances, cryptomining code is not stored on the victim's devices, but runs only when a victim visits an infected website or does not detect the compromised pop-under ad.
Host cryptojacking
This method works like standard phishing and malware attacks. Cryptojackers lure victims into clicking on harmless-looking links that install cryptomining software onto a victims' device. Host-based cryptojacking can affect all types of devices. For instance, Google Android phones are susceptible to Trojan horse cryptojack attacks through apps on Google Play Store.
Cryptojacking malware can also infect open source code and public application programming interfaces, thereby infecting devices that download the code or API and any software developed using them. Unprotected cloud storage is also vulnerable to cryptojacks.
Once inside a victim's endpoint, cryptojacking software can move across all devices on the network, including servers, cloud infrastructures and software supply chains. A lot of cryptojacking scripts also have worming capabilities that detect other cryptojacking malware already operating on a victim's device, disable it and replace it.
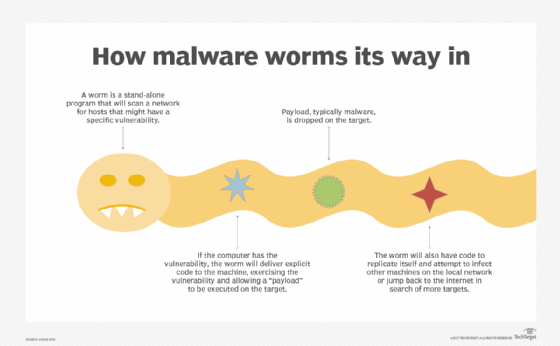
4 methods to detect cryptojacking
Cryptojacking is designed to be as undetectable as possible. However, these four main symptoms are worth watching for:
- Poor performance is a common symptom of cryptojacking. Devices affected may run slower than usual or crash at unusual moments due to strain on processing power from the extra workload.
- Overheating is a common result. Fans in infected devices run faster than usual, or batteries may overheat if a cryptojacking script is taxing the processor of an infected device. Overheating can damage a device or shorten its life span.
- High electricity costs are also a sign of an attack. The energy and processing power required for mining draws significant electricity.
- Central processing unit (CPU) use spikes in response to cryptojacking. Victims with Windows can check their CPU use in Activity Monitor or Task Manager when visiting sites that run little or no media content. If users notice an odd spike, this may indicate a cryptojacking cyber attack. However, cryptojacking malware can be written to hide as legitimate processes and be hard to detect through this method.
How to prevent cryptojacking
Cryptojacking is similar to other types of malware attacks and so are its prevention techniques. The following methods are some of the best ways to prevent cryptojacking attacks:

- Use strong cybersecurity protection. Security admins should use strong antimalware and cybersecurity software built to detect the presence of malicious code, such as cryptomining software. They should also ensure their organizations implement the latest operating systems, web browsers and cybersecurity software updates.
- Use anticryptojacking browser extensions. Browser extensions, such as minerBlock and No Coin, block cryptojacking software running in web browser
- Use ad blocker and disable JavaScript. Using a strong ad blocker and disabling JavaScript can prevent cryptojacking software from running in web browser However, some cryptojacked ads are designed to evade ad blockers.
- Secure servers and cloud configurations. Publicly exposed servers and cloud services are vulnerable to cryptojacks and, as such, should be identified, rooted out and/or secured.
- Use software composition analysis (SCA). SCA technology can identify what open source code is being used in software and security.
- Block infected sites. Blocking sites known to host cryptojacking software or that have outdated plugins and security keeps users from accidentally accessing them.
- Stay up to date. Cryptojacking is a constantly evolving threat, and staying up to date on the latest attack methods keeps users aware of what security threats they might be at risk for.
Examples of cryptojacking attacks
Cryptojacking attacks are at an all-time high, according to ENISA's 2021 "Threat Landscape" report. Some of the most notable victims of attacks in recent years are the following:
- U.S. Defense Department website
- United Kingdom government websites
- Russian nuclear facility supercomputer
- Los Angeles Times Homicide Report page
- YouTube ads
- free apps in Microsoft's app store
Many of these attacks were browser-based ones focused on mining Monero, the most popular coin among cryptojackers. However, ENISA reported that cryptojackers are moving away from browser-based attacks, preferring host-based ones, which, in 2021, accounted for 87% of all cryptojacking attacks. This is partly because the Coinhive website shut down. It provided the browser-based cryptojacking JavaScripts to mine Monero.
Since Coinhive went away, attacks have become more sophisticated and surreptitious to include the infection of APIs, open source code, cloud infrastructures and containers, according to ENISA. Cryptojackers now distribute their attacks to as many people as possible, letting the attackers use less power per device and decrease their detectability.
Some recent attacks use JavaScript package repositories, such as Node Package Manager, and VMware Horizon software. The latter attack comes through a breach in Log4Shell, an open source logging library used by many cloud services and software developers. More Log4Shell attacks are expected with this vulnerability, which the U.S. government predicted will be around for the next decade.
Cryptojacking is a cybercrime that generates currency on blockchain technology. Learn more about blockchain and its benefits to businesses.
